WolfsBane: Gelsemium APT Group’s Linux Backdoor Debut
ESET researchers have unveiled WolfsBane, the Linux counterpart to the Windows-based Gelsevirine backdoor, marking a significant milestone in the evolution of the Gelsemium Advanced Persistent Threat (APT) group. Known for its cyber-espionage campaigns targeting Eastern Asia and the Middle East, this China-aligned group has added Linux systems to its arsenal, signaling a shift in strategy as adversaries adapt to strengthened Windows defenses.
WolfsBane is the first documented Linux malware attributed to Gelsemium, a group active since 2014. “This is the first public report documenting Gelsemium’s use of Linux malware, marking a notable shift in their operational strategy,” the report states. The malware, alongside a second Linux backdoor named FireWood, represents a growing trend of APT groups pivoting toward Linux systems.
ESET attributes this shift to improvements in Windows security, such as widespread adoption of Endpoint Detection and Response (EDR) tools and Microsoft’s disabling of Visual Basic for Applications (VBA) macros by default. These changes have forced adversaries to explore new attack surfaces, with Linux-based internet-facing systems becoming a prime target.
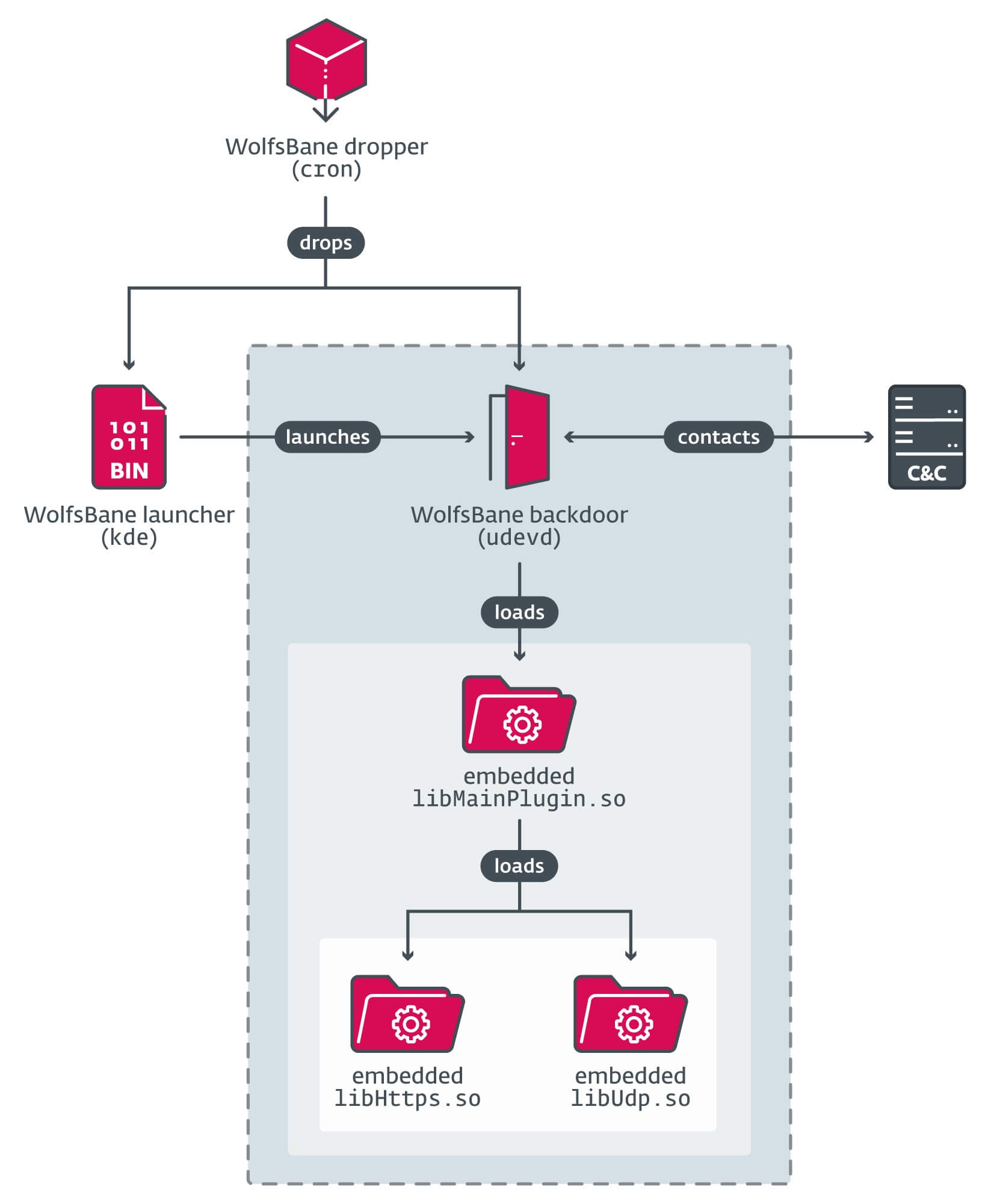
WolfsBane was discovered in archives uploaded to VirusTotal from Taiwan, the Philippines, and Singapore. The malware comprises a three-stage chain: a dropper, a launcher, and the backdoor itself. The dropper mimics legitimate system utilities, such as cron, to evade detection. Once deployed, it establishes persistence by exploiting system services and deploying a userland rootkit to conceal its presence.
The backdoor itself exhibits strong ties to Gelsevirine, as evidenced by:
- Command Execution Mechanism: Both Linux and Windows variants use a table of command hashes mapped to functions for executing commands received from the Command and Control (C&C) server.
- Custom Libraries: Both versions load custom libraries for network communication, with identical typos, such as “create_seesion,” in their codebases.
- Configuration Structures: Similar field names and values in configuration files, including pluginkey and controller_version.
WolfsBane’s C&C communications rely on embedded libraries supporting UDP and HTTPS protocols, facilitating data exfiltration and remote command execution. Its encryption mechanisms allow updates without detection, making it a highly persistent and adaptable threat.
ESET also identified FireWood, a Linux backdoor potentially related to the Project Wood malware family. While its ties to Gelsemium remain tenuous, FireWood shares several traits with known Chinese APT tools, including specific naming conventions, TEA encryption, and consistent C&C communication patterns. FireWood leverages the Netlink protocol for kernel-level interactions and employs various persistence mechanisms to ensure operational longevity.
The shift toward Linux malware reflects broader changes in the threat landscape. According to ESET, “The vulnerabilities present in internet-facing infrastructure, particularly those systems that are Linux-based, are becoming increasingly targeted.” As Linux systems dominate server environments and power critical applications, their exploitation offers adversaries a pathway to sensitive data and prolonged access.
The WolfsBane malware exemplifies the adaptability of the Gelsemium APT group as they expand their attack surface to include Linux systems. By leveraging stealth, persistence, and advanced communication mechanisms, WolfsBane poses a significant risk to organizations with Linux-based infrastructure. As ESET concludes, “These Linux systems are becoming the new preferred targets for these adversaries.”





