Wprecon v2.4.4 releases: vulnerability recognition tool in CMS WordPress
WPrecon (WordPress Recon)
Wprecon (WordPress Recon), is a vulnerability recognition tool in CMS WordPress, 100% developed in Go.
Features
- Detection WAF
- Fuzzing Backup Files
- Fuzzing Passwords
- Random User-Agent
- Plugin(s) Enumerator
- Theme(s) Enumerator
- Scripts
- Tor Proxy
- User(s) Enumerator
- Vulnerability Version Checking (Beta)
Use
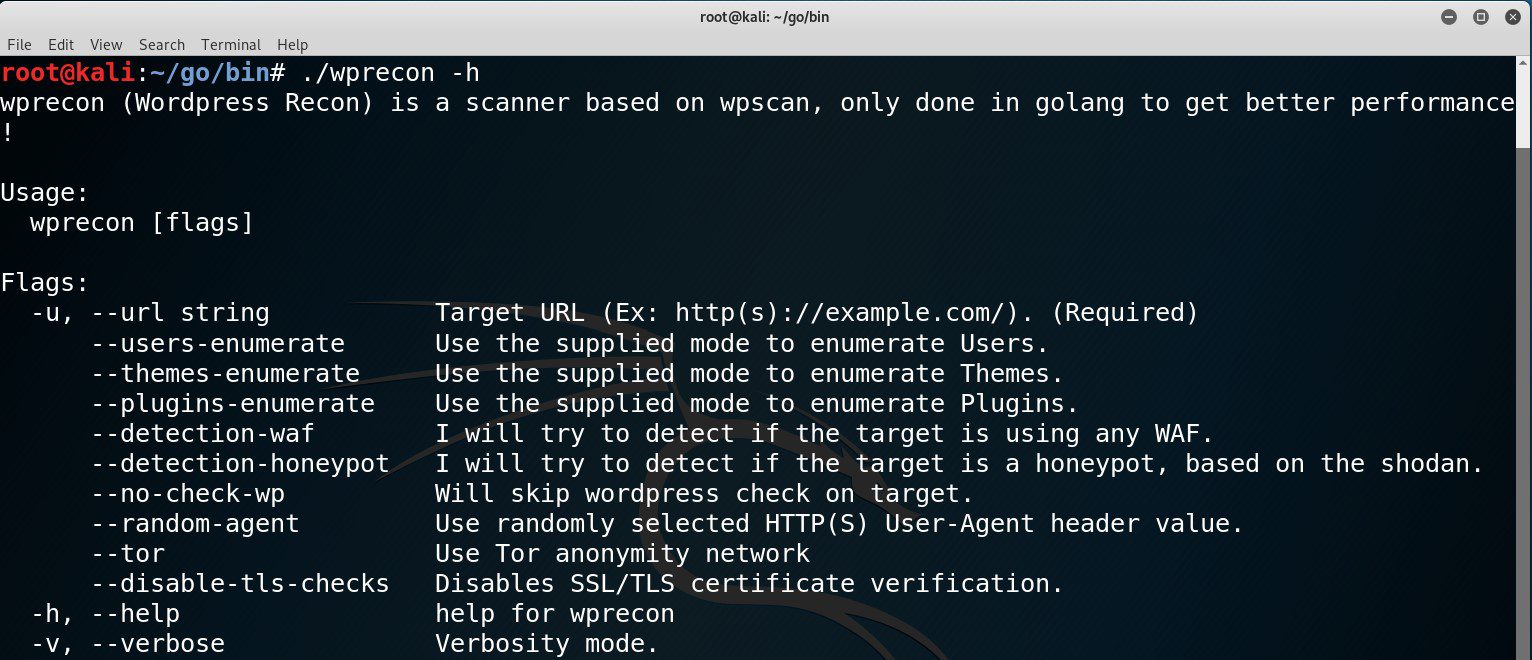
| Flag(s) | Description |
|---|---|
| -u, –url string | Target URL (Ex: http(s)://example.com/). (Required) |
| –users-enumerate | Use the supplied mode to enumerate Users. |
| –themes-enumerate | Use the supplied mode to enumerate Themes. |
| –plugins-enumerate | Use the supplied mode to enumerate Plugins. |
| –detection-waf | I will try to detect if the target is using any WAF. |
| –detection-honeypot | I will try to detect if the target is a honeypot, based on the shodan. |
| –no-check-wp | Will skip wordpress check on target. |
| –random-agent | Use randomly selected HTTP(S) User-Agent header value. |
| –tor | Use the Tor anonymity network. |
| –disable-tls-checks | Disables SSL/TLS certificate verification. |
| -h, –help | help for wprecon. |
| -v, –verbose | Verbosity mode. |
Changelog v2.4.4
- ♻️ Code refactoring
- 🌟 A start to Windows compatibility
Install
go get github.com/blackcrw/wprecon
cd $(go env GOPATH)/src/github.com/blackcrw/wprecon
make build
make install
Copyright (C) 2020 blackcrw





