X.509 certificate abuse, can cause data leakage
Researchers pointed out that cyber-threats actors are actively looking for covert channels to steal data from firewall networks – a move that may include the use of an X.509 certificate to quietly hide and leak data.
X.509 One of the many public key certificate formats. These certificates are used to establish the TLS/SSL connections necessary to support encrypted HTTPS traffic.
But research conducted by Fidelis Cybersecurity’s Jason Reaves in 2017 in 2017 shows that attackers can simply abuse some of the benign factors in these HTTPS negotiations to hide some of the slightest information.
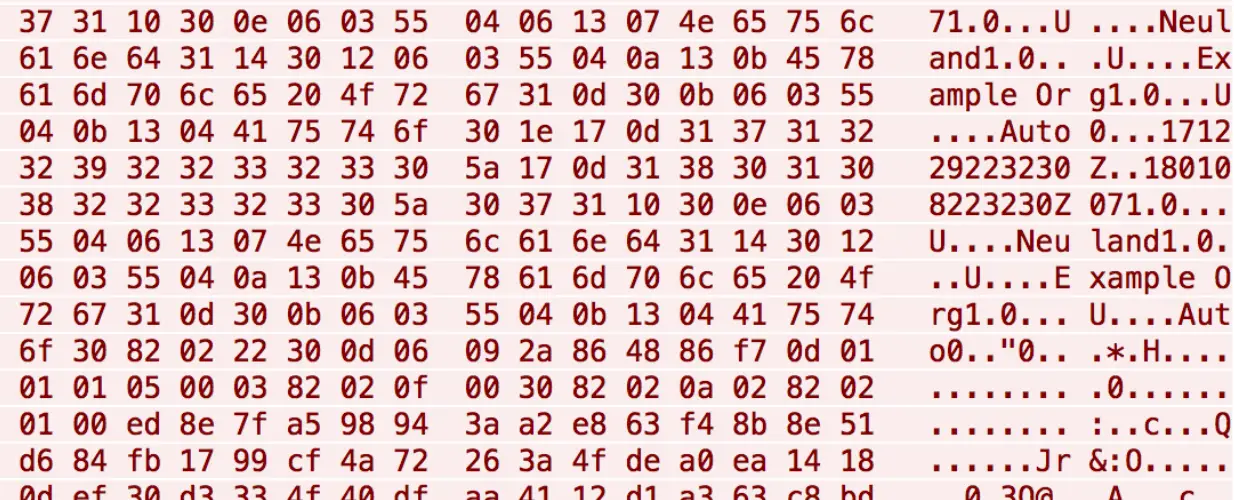
This is possible because some X.509 certificate fields allow an attacker to add some small binary data blocks to it.
Reeves said, “These fields include information such as version, serial number, issuer name, expiration date, etc. In our research, it was discovered that certificate abuse activity is using these fields to conceal data and transmit it.”
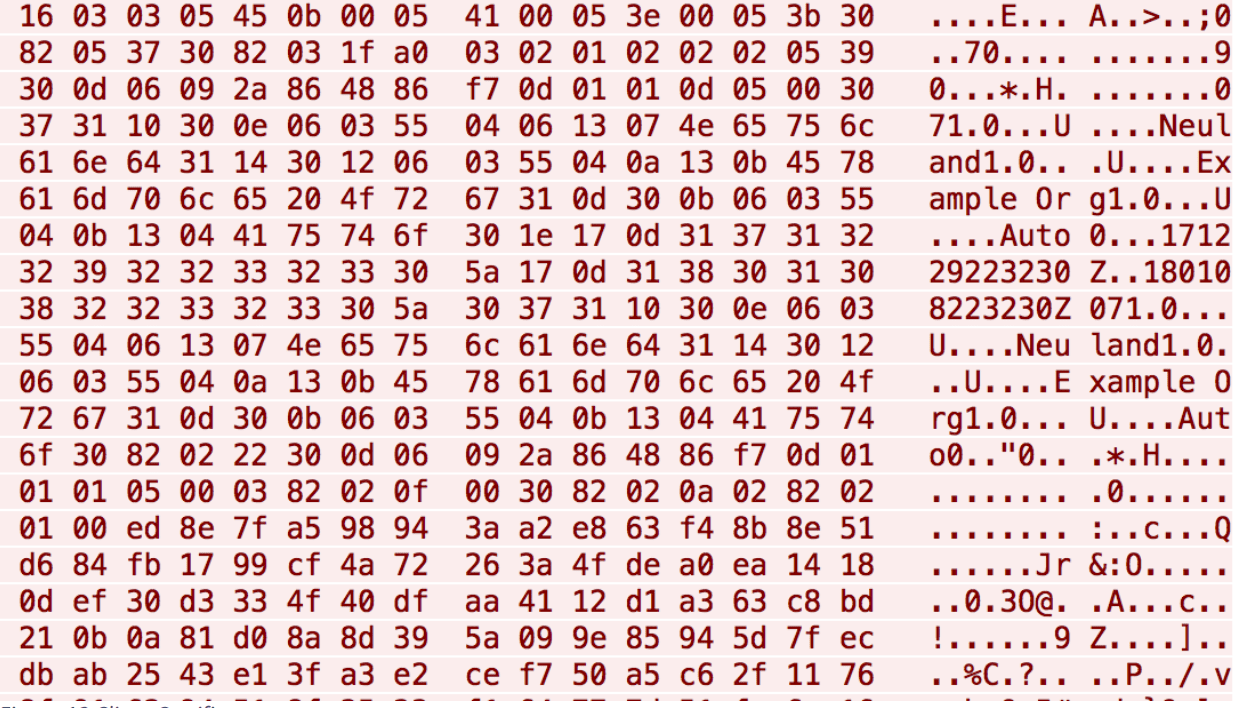
Reeves added that “since the exchange of credentials takes place before the beginning of the TLS session, in spite of the seeming absence of data transmissions, the data has actually been delivered with the exchange of certificate ontologies.” That is why firewalls and even Yes HTTPS MitM cannot detect this technical activity.
As of now, various other types of data leakage channels have been abused by cyber-threats actors, including ICMP, DNS, and steganographic images. Reeves pointed out that he has not found any evidence of the use of X.509 for data leakage in the real world, but this may also be because such activities are hard to detect.
X.509 is used as a covert data channel is nothing new. As early as 2008, the researchers put forward the relevant ideas. Reece’s job is to extend this vision to provide new mechanisms for attacking activities.
Reeves has released Poc code on GitHub, a set of Go frameworks for file transfers through the X.509 certificate metadata fields.
Reuters published X.509 research results can be used for the object-oriented system for file input and output. Interested friends can also click here to see Reeves’s research paper “Covert channel by abusing x509 extensions“.






