Xeon Sender Abuses SaaS APIs for Massive SMS Attacks
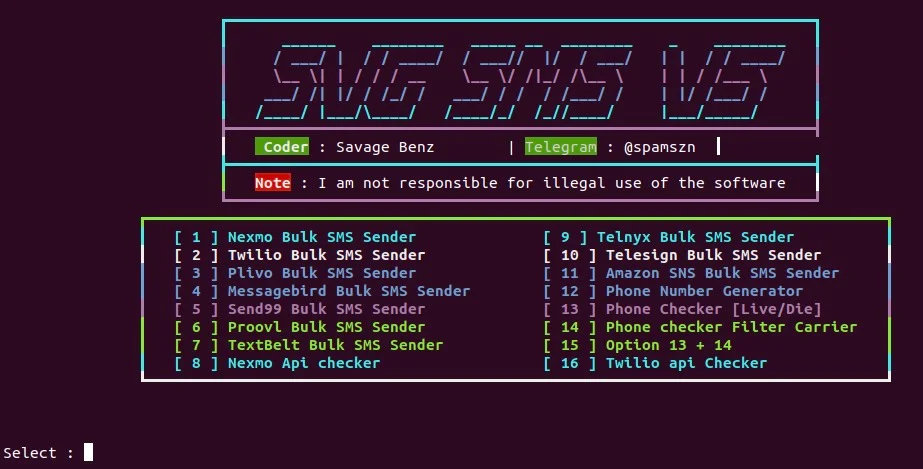
Security researchers at SentinelOne have uncovered a new cloud-based attack tool called Xeon Sender (aka XeonV5, SVG Sender) that enables threat actors to conduct large-scale SMS spam and phishing campaigns. The tool leverages valid credentials for a variety of software-as-a-service (SaaS) providers, including Amazon Simple Notification Service (SNS), Nexmo, Twilio, and others, to send bulk SMS messages.
The origins of Xeon Sender trace back to at least 2022, with the earliest known version attributed to a user handle @darkworld47. Over time, as is common with successful hacktools, various actors have added their own monikers to the tool, leading to multiple versions circulating online. Despite these variations, the core functionality of Xeon Sender remains unchanged, with each iteration continuing to enable effective and large-scale SMS spam operations.
Xeon Sender is predominantly distributed through Telegram, a popular platform for cybercrime tool dissemination, as well as through smaller hacking forums. Its proliferation on these platforms underscores its appeal to a wide range of threat actors, from seasoned cybercriminals to lower-skilled operators.
At its core, Xeon Sender provides a straightforward command-line interface (CLI) for attackers to interact with targeted service provider backends. The tool’s simplicity belies its effectiveness, requiring only a few key pieces of information from the operator, including API keys, sender IDs, and a list of recipient phone numbers. These details allow Xeon Sender to craft API requests to the service providers, facilitating the dispatch of spam messages with remarkable ease.
One of the distinguishing features of Xeon Sender is its inclusion of various utilities designed to enhance its usability. These include account checker tools for validating credentials on platforms like Twilio and Nexmo, a phone number generator, and a phone checker that verifies the validity of numbers using the APILayer.com Number Verification API.
However, Xeon Sender is not without its limitations. The tool lacks the refinement of more professional applications, with limited error handling and ambiguous variable names that complicate debugging. Despite these shortcomings, its effectiveness in enabling large-scale SMS spam campaigns remains undisputed.
Detecting the abuse of services by Xeon Sender presents unique challenges for security teams. The tool’s reliance on provider-specific Python libraries for crafting API requests means that detection efforts must be tailored to the logs and activities of each individual provider. This complexity is further compounded by the legitimate nature of the API calls, which can make it difficult to distinguish between normal and malicious activity.
Organizations should monitor activity related to evaluating or modifying SMS sending permissions or anomalous changes to distribution lists. For organizations using AWS, this includes monitoring calls to the GetSMSAttributes AWS API or changes to existing permissions using calls to SetSMSAttributes.





