XPhase Clipper: The Global Crypto Scam Unveiled by CRIL
Cyble Research and Intelligence Labs (CRIL) has uncovered a sophisticated malware campaign, ingeniously dubbed “XPhase Clipper,” targeting cryptocurrency enthusiasts with a precision that sends shivers down the spine. This campaign utilizes a cunning blend of deceptive websites, mimicking legitimate cryptocurrency applications, to ensnare its victims. Among the targeted are users of MetaMask, WazirX, Lunoapp, and CryptoNotify, all lured into a trap that could cost them.
The modus operandi of the XPhase Clipper is as ingenious as it is nefarious. By intercepting and altering the data exchanged between a user and a legitimate service, this clipper malware replaces cryptocurrency wallet addresses copied by users with those controlled by attackers. This devious switcheroo ensures that funds meant for one destination end up in the coffers of the attackers.
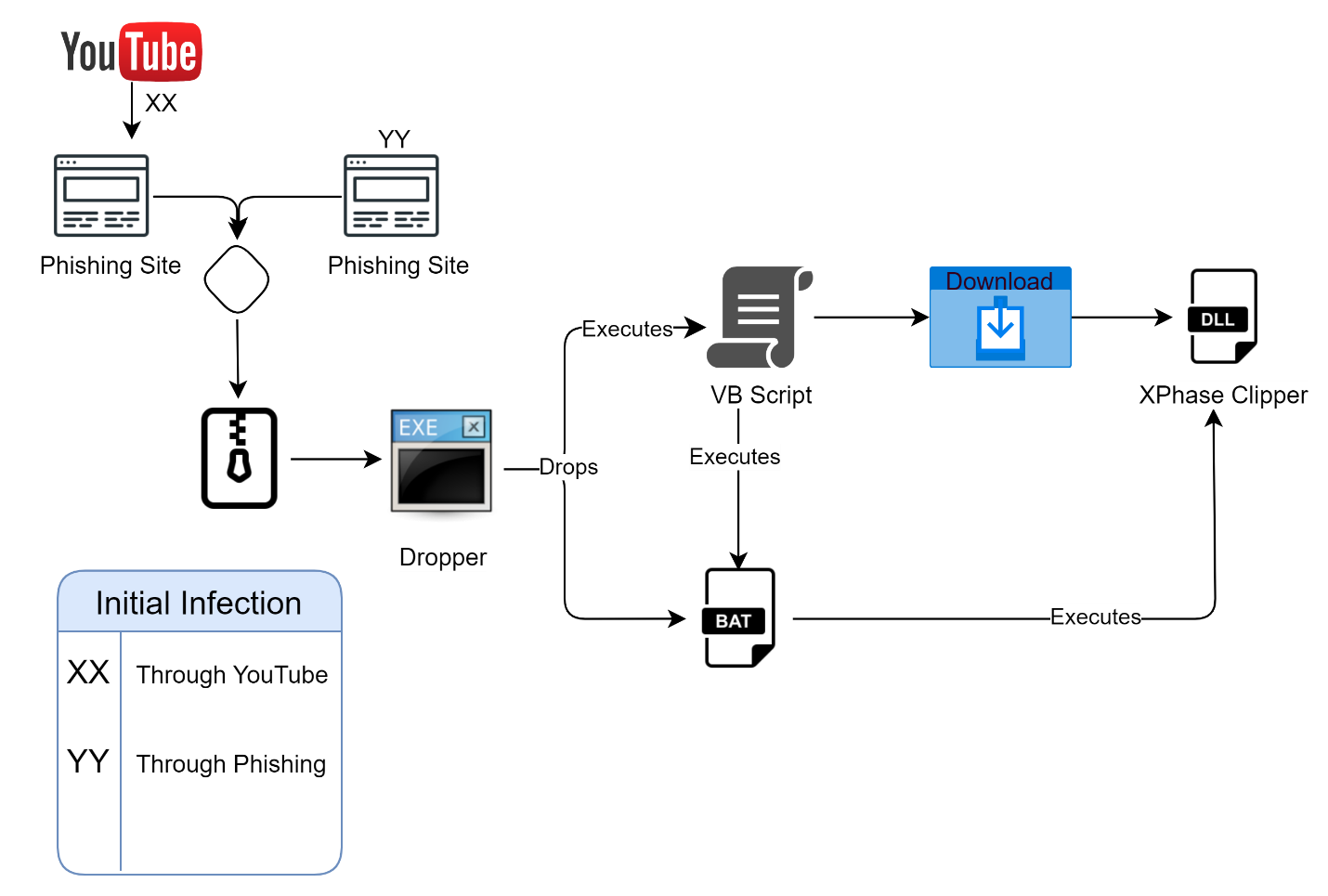
The infection chain reveals a meticulously planned attack. It begins with a seemingly innocent download from these phishing sites, which delivers a zip file containing the malicious executable, a Trojan horse laying in wait. What follows is a cascade of scripts and payloads, culminating in the clipper payload, a DLL file, being executed, establishing persistence, and beginning its silent watch over clipboard content.

Infection Chain | Image: CRIL
Further investigation into the campaign’s infrastructure exposed several domains, all linked to an IP address managed by Reg.Ru Hosting in Russia, indicating a possibly centralized operation with a global reach. The use of cloned content from reputable sources, such as a popular YouTube channel, highlights the attackers’ sophistication in leveraging social engineering to broaden their net.
The ramifications of falling victim to the XPhase Clipper campaign are dire, with users facing the prospect of substantial financial losses. By intercepting and manipulating cryptocurrency wallet addresses, threat actors jeopardize the integrity of transactions, siphoning funds into their own coffers. Moreover, the campaign’s targeted approach towards specific cryptocurrency platforms underscores the sophistication and regional focus of the threat actors involved.
This campaign is a stark reminder of the perpetual arms race between cybercriminals and the cybersecurity community. It underscores not just the ingenuity of threat actors but also the critical importance of vigilance and cybersecurity hygiene among users. In response, Cyble Research and Intelligence Labs recommends a series of best practices, including skepticism towards downloads from unknown sources, the employment of endpoint detection and response solutions, and the monitoring of network traffic for signs of suspicious activity.





