xray v0.15 releases: A powerful security assessment tool
xray
A powerful security assessment tool.
Detection module
We are working hard for new detection modules
- xssXSS Vulnerabilities Scan
- sqldetSupport error based, boolean based and time-based sql injection detection
- cmd_injectionDetect common shell command injection, PHP code execution, and template injection, etc
- dirscanSupport about ten kinds of the sensitive path and file type, including backup file, temp file, debug page, config file, etc
- path_traversalSupport command platform and encoding
- xxeSupport echo based detection and can work with reverse server
- phantasmCommon poc inside, user can add your own poc and run it. Document: https://chaitin.github.io/xray/#/guide/poc
- uploadSupport common backend languages
- brute_forceThe community version can detect weak password in http basic auth and simple form, common username and password dict inside
- jsonpDetect jsonp api with sensitive data which can be called across origins
- ssrfSupport common bypass tech and can work with reverse server
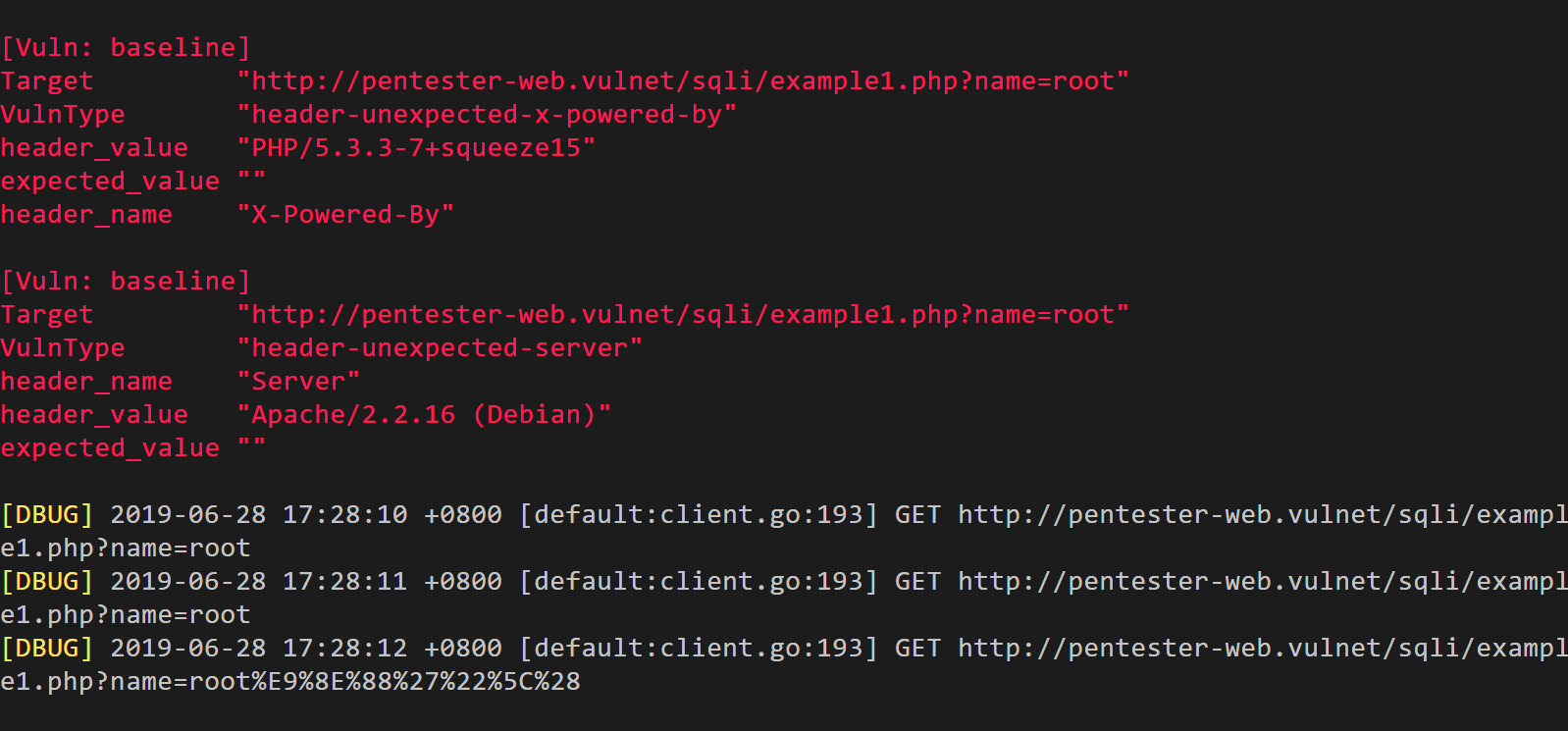
- baselineDetect outdated SSL version, missing or incorrect http headers, etc
- redirectDetect arbitrary redirection from HTML meta and 30x response, etc
- crlf_injectionDetect CRLF injection in HTTP header, support parameters from query and body, etc
Changelog v0.15
Feature
-
Support configuration plug-in concurrency (max_parallel, default performance is 10 times higher than before)
- Advanced version adds subdomain scan command, supports dictionary blast, API acquisition, domain transfer, and collects subdomains in three ways.
- Add OA htmlofficeservlet remote code execution: POC poc-go-seeyon-htmlofficeservlet-rce
- Add pan-micro OA DB information disclosure: POC poc-go-ecology-db-config-info-leak
-
The command-line arguments –json-output and –html-output add variables __timestamp__ and __datetime__, automatically replaced with timestamps or date-times, avoiding errors when outputting to the same file
Bugfixes:
-
Fix an underreport of the premium version of the thinkphp plugin
-
Fix some problems with anti-connection platform processing ipv6
-
Fix multiple exploit issues for the same vulnerability caused by filter competition issues
Use
- Use basic crawler to scan a website
xray webscan --basic-crawler http://example.com --html-output crawler.html
- Run as an HTTP proxy to scan passively
xray webscan --listen 127.0.0.1:7777 --html-output proxy.html
Configure the browser to use http proxy http://127.0.0.1:7777, then the proxy traffic can be automatically analyzed and scanned。
If need to scan https traffic,please read capture https trafic section in this document.
- Scan a single url
xray webscan --url http://example.com/?a=b --html-output single-url.html - Specify the plugins to run manually
By default, all built-in plugins are enabled, and the following commands can be used to enable specific plugins for this scan.
xray webscan --plugins cmd_injection,sqldet --url http://example.com
xray webscan --plugins cmd_injection,sqldet --listen 127.0.0.1:7777
- Specify plugin output pathYou can specify the output path of the vulnerability information:
xray webscan --url http://example.com/?a=b \ --text-output result.txt --json-output result.json --html-output report.html
Source: https://github.com/chaitin/