ZDI Details Copy2Pwn: Zero-Day CVE-2024-38213 Evades Windows Security Measures
Researchers at Trend Micro’s Zero Day Initiative (ZDI) published the technical details for a vulnerability in Windows, identified as CVE-2024-38213, which has exposed a critical flaw in the operating system’s ability to protect users from remote code execution attacks. This vulnerability, dubbed “Copy2Pwn”, allows threat actors to bypass Windows’ Mark-of-the-Web (MotW) protections, leaving millions of users at risk.
The investigation into CVE-2024-38213 began in March 2024 when ZDI’s Threat Hunting team analyzed a series of malicious campaigns orchestrated by the notorious DarkGate group. These campaigns focused on infecting users through deceptively simple copy-and-paste operations. This new wave of attacks marked an evolution from a previous campaign that exploited another zero-day vulnerability, CVE-2024-21412, disclosed earlier this year.
The DarkGate operators leveraged Web-based Distributed Authoring and Versioning (WebDAV) shares to distribute malicious payloads. WebDAV, an extension of HTTP, allows files to be accessed over the web or through Windows Explorer using UNC paths. However, files copied from these shares were not always properly marked with the MotW, a critical security feature that protects users from untrusted content.
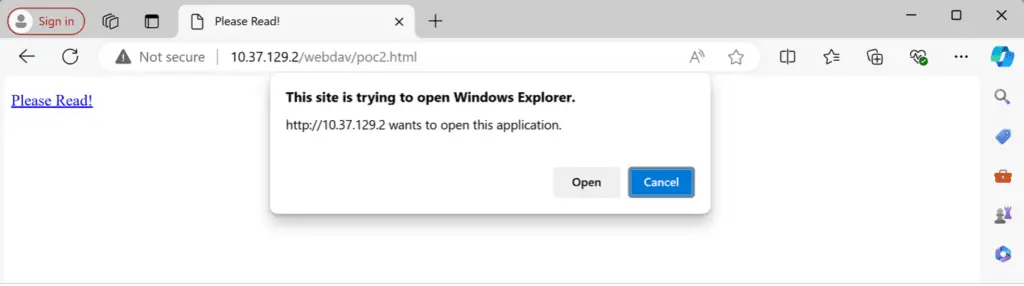
Microsoft Edge prompts users to open the WebDAV share in Windows Explorer | Image: Zero Day Initiative
CVE-2024-38213 is rooted in the way Windows handles files copied from WebDAV shares. When users copy and paste a file from a WebDAV share to their local system, the file should be flagged with the MotW, indicating that it originated from an untrusted source. This flag triggers additional security checks, such as Windows Defender SmartScreen and Microsoft Office Protected View, which are designed to prevent the execution of potentially harmful content.
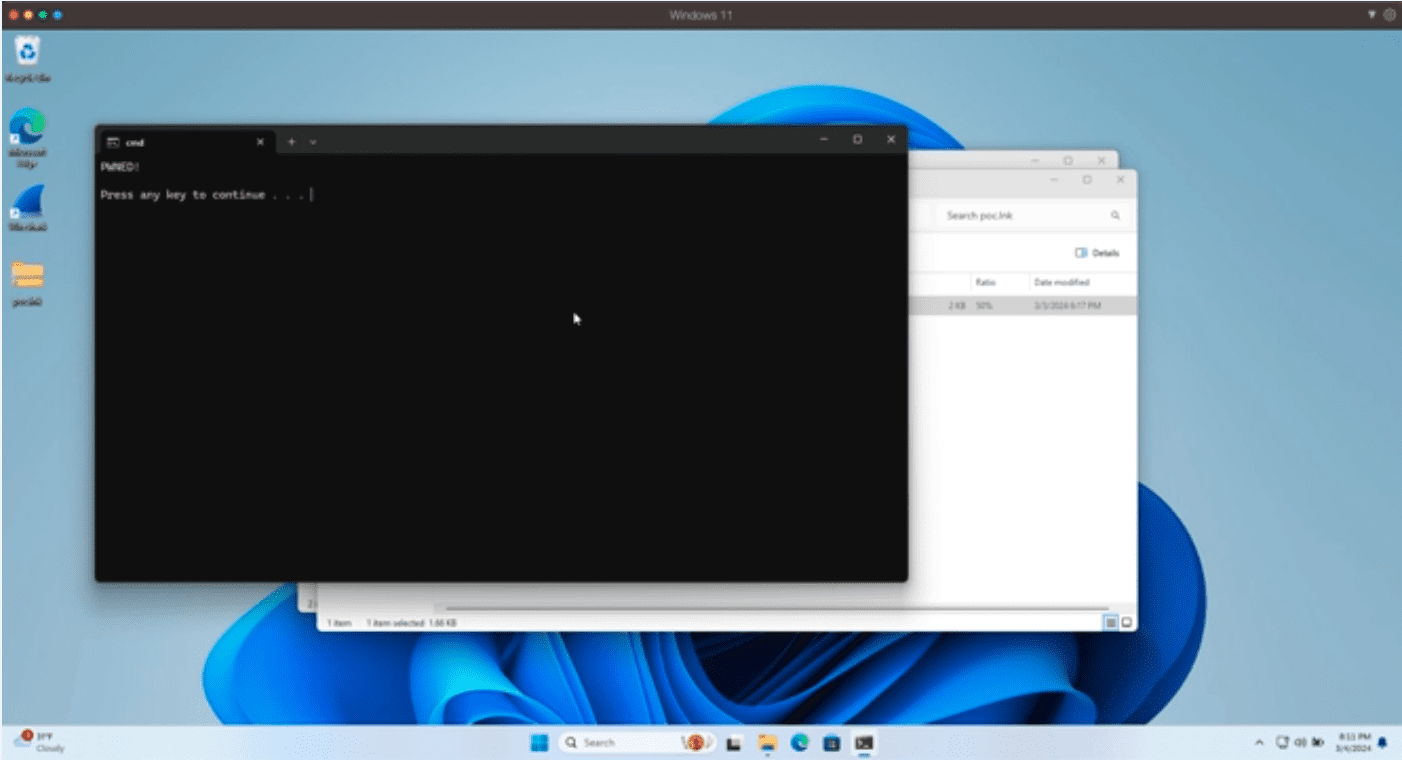
However, ZDI researchers discovered that prior to Microsoft’s June 2024 security patch, files copied in this manner did not receive the necessary MotW designation. As a result, malicious files could be opened without triggering any security warnings or checks, effectively bypassing Windows’ built-in protections. This exploit, termed “Copy2Pwn,” enables threat actors to execute remote code on a victim’s machine with minimal user interaction.
WebDAV shares have recently seen increased use by threat actors as a way to host malicious payloads. This exploit, along with other recent vulnerabilities, highlights the potential dangers of using WebDAV, especially when accessed through Windows Explorer.
MotW is a crucial security feature that adds a layer of protection against malicious files downloaded from untrusted sources. When a file is marked with MotW, it triggers security checks and prompts when opened, reducing the risk of accidental execution of harmful content.
Microsoft addressed CVE-2024-38213 in its June security patch. Windows users need to ensure their systems are fully updated to protect against this exploit and other similar threats.





