Zergeca Botnet Exposed: Advanced Capabilities Beyond DDoS
Cybersecurity researchers at XLab have uncovered a sophisticated new botnet dubbed “Zergeca.” Discovered in May 2024, this Golang-based threat exhibits advanced features beyond typical DDoS capabilities, including proxying, scanning, self-upgrades, persistence mechanisms, and exfiltration of sensitive device information.
Zergeca stands out due to its unique network communication tactics, prioritizing DNS over HTTPS (DoH) for covert command-and-control (C2) communication and employing the uncommon Smux library for encrypted data exchange.
Zergeca’s offensive capabilities are alarming. Its developers have equipped it with seven distinct DDoS attack vectors, enabling it to launch a variety of disruptive assaults. Furthermore, XLab’s analysis reveals that the botnet is under active development, with new commands and features being added regularly. This adaptability suggests that Zergeca’s creators are committed to keeping their creation ahead of the curve, posing a persistent and evolving threat.
Researchers have drawn intriguing connections between Zergeca and the notorious Mirai botnet. The tactics and techniques employed by Zergeca’s creator suggest that they may have gained experience operating Mirai botnets, utilizing that knowledge to craft a more refined and evasive threat.
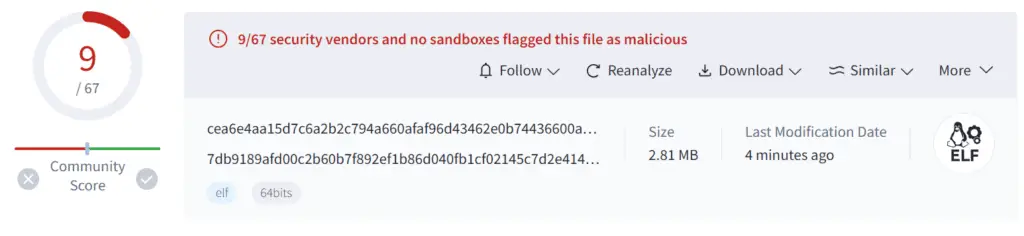
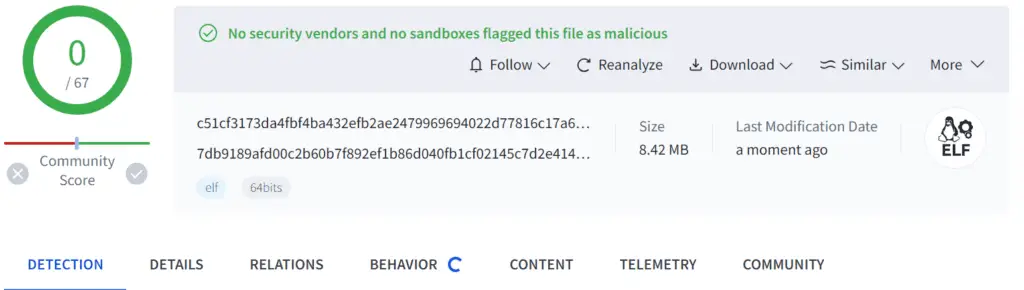
One of the most concerning aspects of Zergeca is its current low detection rate. A combination of modified packing techniques and the use of DoH for C2 communication has allowed it to fly under the radar of many security solutions. This low visibility makes it a particularly dangerous threat, as it can amass a significant network of infected devices before being detected, potentially leading to large-scale DDoS attacks with severe consequences. Researchers captured a total of five Zergeca samples. Despite their nearly identical functions, there is a significant discrepancy in their detection rates.
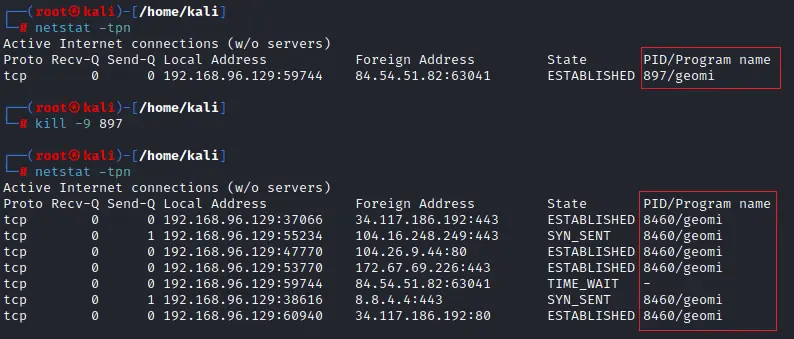
The two C2 servers of Zergeca point to the same IP address, 84.54.51.82. This IP has been in use since September 2023, serving various roles:
- Scanner: From September 18, 2023, scanning activities targeted protocols such as Telnet, HTTP, and socks4, with main ports scanned including 23, 8080, 3128, 80, and 8888.
- Mirai Downloader & C2: From September and October 2023 to April 2024, 84.54.51.82 was primarily used as the Loader IP and Downloader IP for the Mirai botnet.
- Zergeca C2: Since April 29, 2024, 84.54.51.82 has been used as the C2 server for Zergeca.
The primary methods used by 84.54.51.82 to propagate samples include Telnet weak passwords and certain known vulnerabilities:
- CVE-2022-35733
- CVE-2018-10562
- CVE-2018-10561
- CVE-2017-17215
- CVE-2016-20016
From early to mid-June 2024, the Zergeca botnet primarily targeted regions such as Canada, the United States, and Germany, with the main type of attack being ackFlood. Victims were distributed across multiple countries and different ASNs.
The four Zergeca samples observed are designed for the x86-64 CPU architecture, targeting the Linux platform. The presence of strings like “android,” “darwin,” and “windows,” along with Golang’s inherent cross-platform capabilities, suggests that the author may eventually aim for full platform support.

Zergeca achieves persistence on compromised devices by adding a system service geomi.service, ensuring the sample automatically generates a new geomi process if the device restarts or the process is terminated.
To monopolize the device, Zergeca includes a list of competitor threats, covering miners, backdoor trojans, botnets, and more. It continuously monitors the system and terminates any process matching the list, deleting the corresponding binary files.
Zergeca resolves the C2 IP address using the geomi_common_utils_Resolve function, which supports four resolvers: Public DNS, Local DNS, DoH (DNS over HTTPS), and OpenNIC. It reports sensitive device information to the C2 and awaits commands, supporting various functionalities including six types of DDoS attacks, scanning, and reverse shell.
Zergeca uses XOR encryption for many sensitive strings. Using IDA, we identified the XOR key used across various functions. Automating the decryption process revealed the decryption pattern, allowing us to efficiently restore all encrypted strings.
The emergence of Zergeca underscores the constantly changing nature of the cyber threat landscape. As attackers continue to develop new and more sophisticated tools, defenders must remain vigilant and proactive in their efforts to protect digital assets.