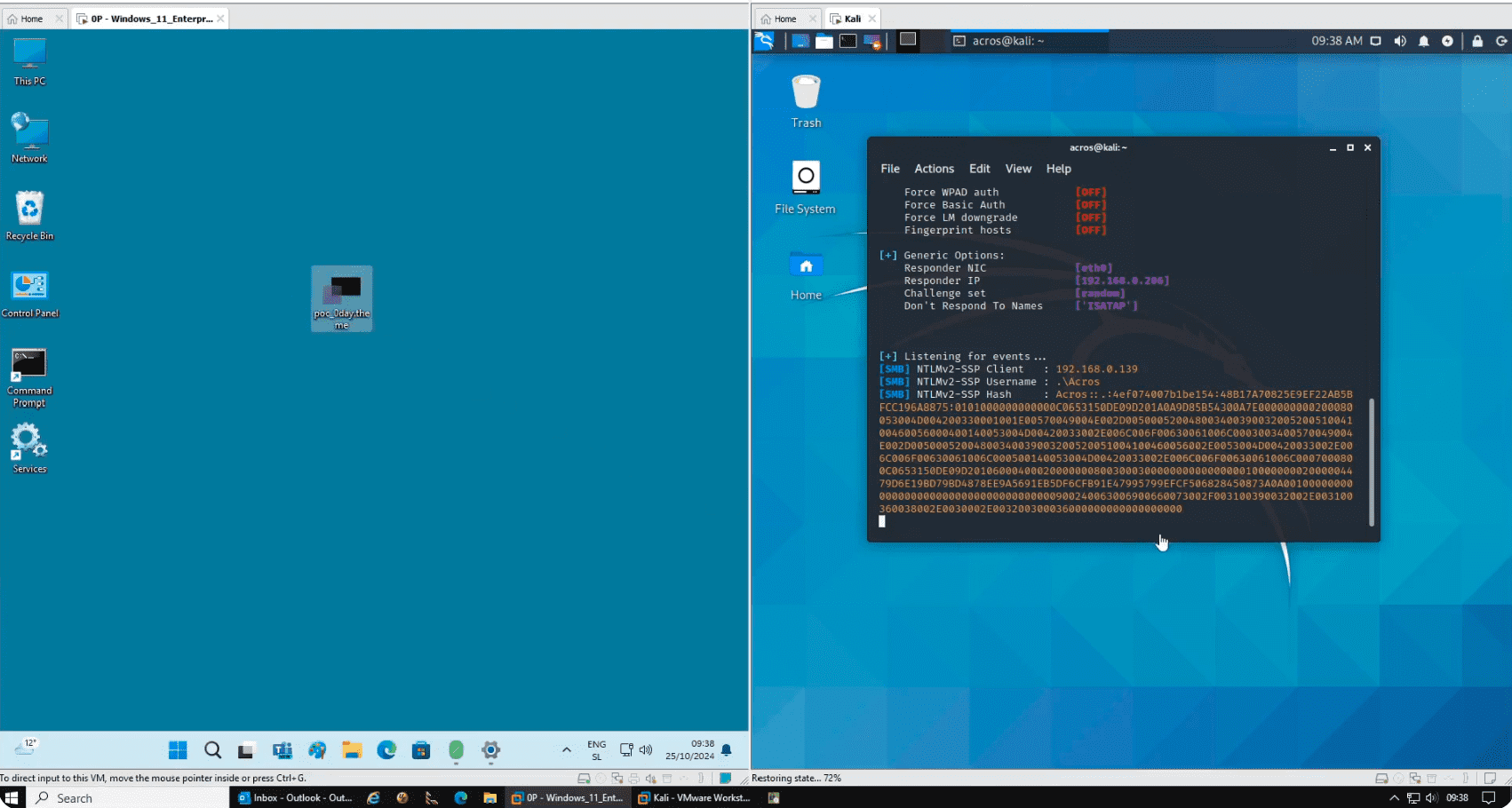
Security researchers at 0patch have discovered a new zero-day vulnerability in Microsoft Windows, exposing users to potential credential theft. This revelation comes on the heels of Microsoft’s attempts to patch a similar flaw, CVE-2024-21320, initially reported by Akamai researcher Tomer Peled. The new vulnerability, yet to receive a CVE identifier, allows attackers to leak user credentials simply by having the user view a malicious theme file.
This vulnerability is a variation of the original flaw, which exploited Windows’ handling of network file paths in theme files. As 0patch explains, “When a theme file specified a network file path for some of the theme properties (specifically BrandImage and Wallpaper), Windows would automatically send authenticated network requests to remote hosts, including user’s NTLM credentials when such theme file would be viewed in Windows Explorer.”
While Microsoft believed they had addressed the issue with their patch for CVE-2024-21320, and subsequently CVE-2024-38030, 0patch researchers discovered that “an additional instance of the very same problem still present on all fully updated Windows versions, up to currently the latest Windows 11 24H2.”
This discovery raises questions about Microsoft’s vulnerability analysis process, specifically their “Hacking for Variations” (HfV) stage, which aims to identify and mitigate similar vulnerabilities. 0patch points out that “looking for bug variations seems like something every software vendor should be doing when learning about a security issue in their product.”
In the meantime, 0patch has taken proactive measures to protect its users. They have developed a micropatch that addresses the new vulnerability, providing immediate protection for users of both legacy and currently supported Windows versions. The micropatch is being offered for free until Microsoft releases an official fix.
“Vulnerabilities like these get discovered on a regular basis, and attackers know about them all,” warns 0patch. “If you’re using Windows that aren’t receiving official security updates anymore, 0patch will make sure these vulnerabilities won’t be exploited on your computers.”
Related Posts:
- CISA & Microsoft Warn of 6 Actively Exploited Zero-Day Vulnerabilities
- Mozilla releases emergency update to fix two exploited zero-day vulnerabilities in Firefox
- Zero-Day Vulnerability: 18 Years of Exploiting the ‘0.0.0.0’ Flaw
- Microsoft April Patch Tuesday includes mitigate Spectre Variant 2 for AMD processors