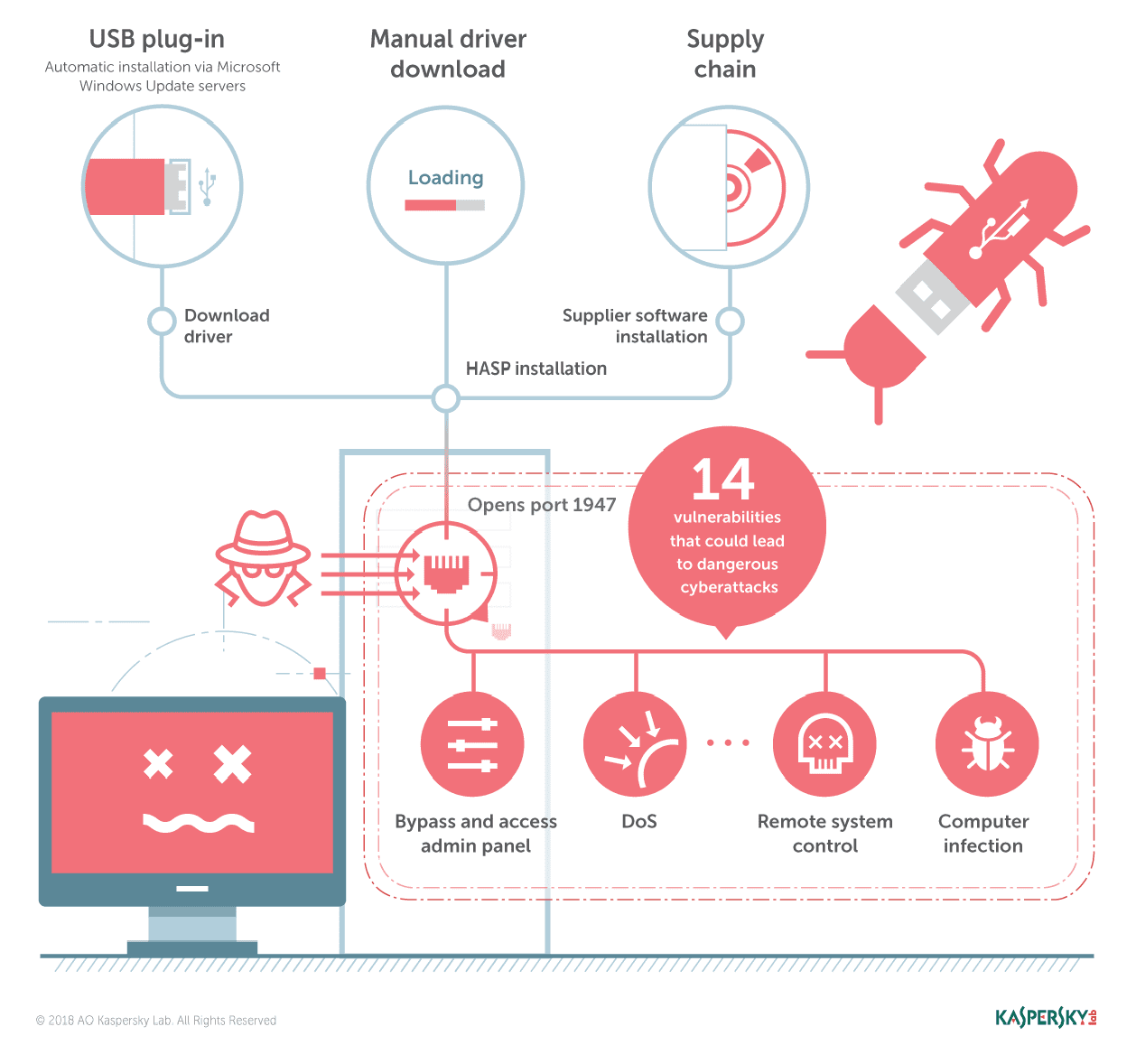
Researchers at Kaspersky Lab found that 14 vulnerabilities exist in Sentinel LDK, a software licensing solution for Gemalto, the Dutch SIM card maker, leaving a large number of industrial and enterprise systems vulnerable to remote attack.
Sentinel LDK is a Gemalto software licensing solution that addresses the full spectrum of issues in the software licensing lifecycle, including software intellectual property protection, preventing unauthorized use, bundling of product features, licensing upgrades, and update management. Effectively improve the software security, license management transparency and many other troubled software developers. Many businesses around the world use this solution in business and ICS networks. In addition to the software components, Sentinel LDK also offers software-based protection, specifically the SafeNet Sentinel USB token, such as a USB dongle that allows users to connect to a PC or server to activate a product.
The researchers found that when the SafeNet Sentinel USB token was connected to the device, the necessary drivers (either downloaded by Windows or provided by third-party software) were installed and port 1947 was added to the Windows Firewall exception list. When unplugged USB token, this port is still open, allowing remote access to the system.
Experts found a total of 14 vulnerabilities in the Sentinel component, some of which allow DoS attacks, arbitrary code execution, and capturing NTLM hashes. Because port 1947 allows access to the system, remote attackers can exploit these vulnerabilities. Some of the loopholes listed:
- CVE-2017-11496 – Remote Code Execution
- CVE-2017-11497 – Remote Code Execution
- CVE-2017-11498 – Denial of service
- CVE-2017-12818 – Denial of service
- CVE-2017-12819 – NTLM hash capture
- CVE-2017-12820 – Denial of service
- CVE-2017-12821 – Remote Code Execution
- CVE-2017-12822 – Remote configuration using profiles
Kaspersky’s ICS CERT team encountered this issue during its penetration testing mission and decided to analyze the product. A malicious person can scan port 1947 for remote access by finding a remotely accessible device or by physically accessing the target device to connect a USB token (even if the computer is locked).
Gemalto This product also includes APIs that enable and disable the administrator interface remotely and change settings, including obtaining proxy settings for language packs. Changing the proxy will allow an attacker to obtain the NTLM hash of the account used to run the licensed software process.
In addition to installing the latest version of Sentinel drivers, Kaspersky recommends that users close port 1947 if unconventional operations are necessary.
Kaspersky Lab found 11 vulnerabilities in late 2016 and early 2017, and three other vulnerabilities were discovered in June 2017. After the extension has been notified Jinya in version 7. To repair a flaw in the 6, but was not satisfied with Kaspersky expressed their treatment. Gemalto solved the first vulnerabilities in June 2017 and Gemalto did not adequately inform consumers about the risks of the vulnerabilities. Several software developers who use the solution say to Kaspersky that they are not aware of security breaches and are still using vulnerable versions.
Kaspersky predicts the product may have millions, but the exact number of devices is not yet known. According to a 2011 study released by Forst & Sullivan, SafeNet Sentinel has a high share of North American licensing control solutions 40%, accounting for 60% of the European market.
This software is also used by several large enterprises, including ABB, General Electric, Hewlett-Packard, Siemens, Cadac Group and Zemax.
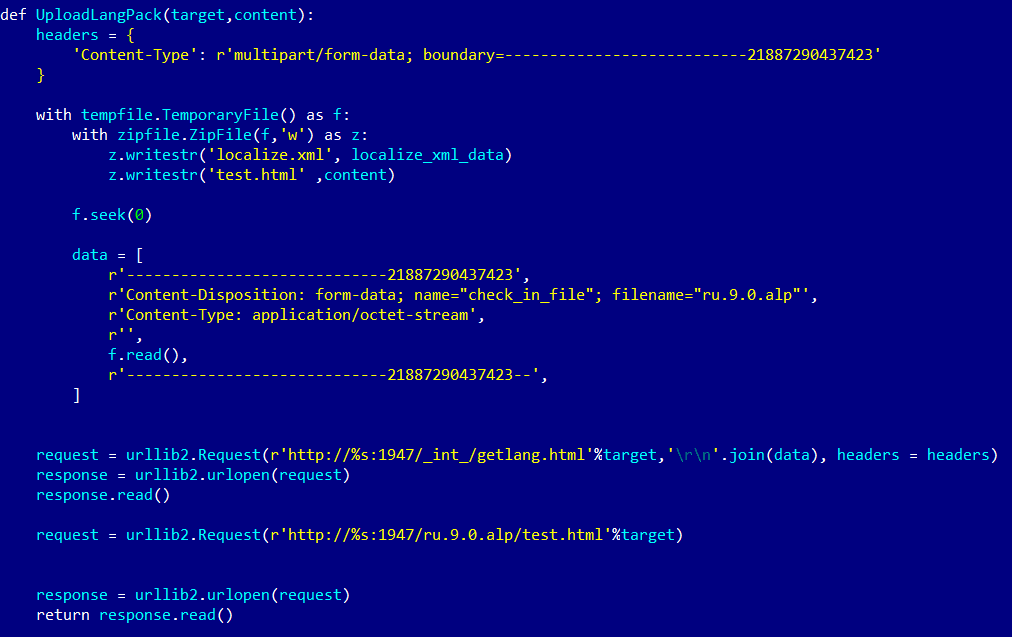
Not long ago, ICS-CERT and Siemens warned in the US that more than a dozen SIMATIC WinCC extensions were affected by three high-risk vulnerabilities due to the use of Gemalto software. Siemens said two of the vulnerabilities were related to the way the language packs were handled, allowing attackers to launch DoS and arbitrary code execution attacks. The release of SIMATIC WinCC by Siemens 2015 and earlier was affected by the vulnerability.
Vladimir Danishchenk, head of Kaspersky’s ICS-CERT vulnerability research group, said Sentinel LDK is widely used and its vulnerabilities can have very serious consequences as the tokens are not only used in traditional enterprise environments but also Used in critical facilities with strict remote access rules. The latter may easily collapse as a result, placing critical networks at risk.
Source: Kaspersky