
In a recent report by Kaspersky Labs, the notorious Grandoreiro banking trojan has once again made headlines, evolving into a significant global financial threat. Originating in Brazil, this trojan, which has been active since at least 2016, is part of the Tetrade malware family and is designed to steal banking credentials and bypass security measures. Despite law enforcement efforts to disrupt its operations, including arrests in Spain, Brazil, and Argentina, Grandoreiro remains a potent force in the world of cybercrime.
Initially targeting Latin American banks, Grandoreiro’s operators have significantly expanded their reach over the years. By 2024, the malware was found to be targeting 1,700 banks and 276 cryptocurrency wallets across 45 countries, making it a truly global threat. According to Kaspersky’s report, “Asia and Africa have finally joined the list of its targets, making it a truly global financial threat.” This marks a significant evolution from its earlier focus on Latin America.
Spain, in particular, has been hard hit by Grandoreiro’s fraudulent activities, with conservative estimates placing the malware’s financial impact at 3.5 million euros. However, the report notes that several failed attempts could have led to profits exceeding 110 million euros for the criminal organization.
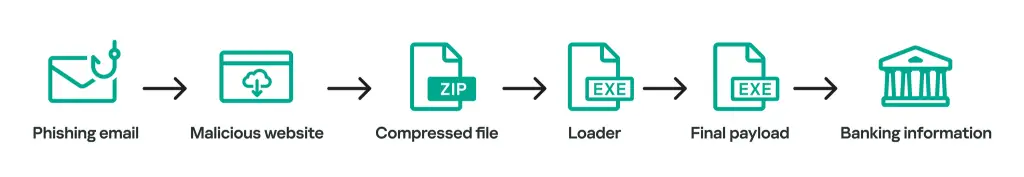
Grandoreiro is not just about scale; it has continuously evolved its tactics to stay one step ahead of law enforcement and cybersecurity measures. One of the most recent innovations involves using domain generation algorithms (DGAs) to create new command-and-control (C2) servers, complicating domain-based blocking strategies. The malware also employs ciphertext stealing encryption (CTS), a sophisticated encryption mode that adds another layer of complexity for analysts attempting to decrypt and analyze its code.
Moreover, Grandoreiro has adopted new sandbox evasion techniques, such as tracking mouse movements to mimic legitimate user interactions. As noted in the report, the malware now records “the client’s average mouse speed for 5 seconds,” a tactic aimed at fooling machine learning-based anti-fraud systems.
Grandoreiro’s evolution over time has made it a particularly challenging adversary for cybersecurity professionals. The malware’s modular nature allows for multiple operators to create fragmented versions, each tailored to specific regions or financial institutions. Since 2022, Kaspersky has observed the creation of smaller, lighter versions of the trojan, which are focused on fewer targets—particularly in Mexico.
The report emphasizes that “Grandoreiro generally operates as Malware-as-a-Service,” although its distribution is more controlled than other banking trojans, with access to its source code limited to trusted partners.
Kaspersky has worked closely with INTERPOL and other law enforcement agencies to share tactics, techniques, and procedures (TTPs) used by the malware, but the fight is far from over.
The report concludes that while law enforcement efforts have made some progress, Grandoreiro’s operators are continuing to develop new malware variants and establish new infrastructures. With over 150,000 infection attempts blocked by Kaspersky in 2024 alone, it is clear that Grandoreiro’s ambition shows no sign of slowing down.
Related Posts:
- Brazilian Banking Malware Targets Spain: An Emerging Cyber Threat Landscape
- Cybercriminals Target LatAm Banks: Mekotio, BBTok Lead the Charge
- Kaspersky Report: Criminals earning millions through mining malware
- Operation Cronos: Notorious LockBit Ransomware Disrupted
- Kaspersky Highlights Key Trends in Financial Cybersecurity for 2024