Image: DreyAnd
A new critical vulnerability has been discovered in CyberPanel, a popular open-source web hosting control panel, by security researcher DreyAnd. The flaw, a zero-click pre-authentication root remote code execution (RCE), remains unpatched in the latest version (2.3.6) of CyberPanel, leaving potentially thousands of instances exposed to a serious security threat.
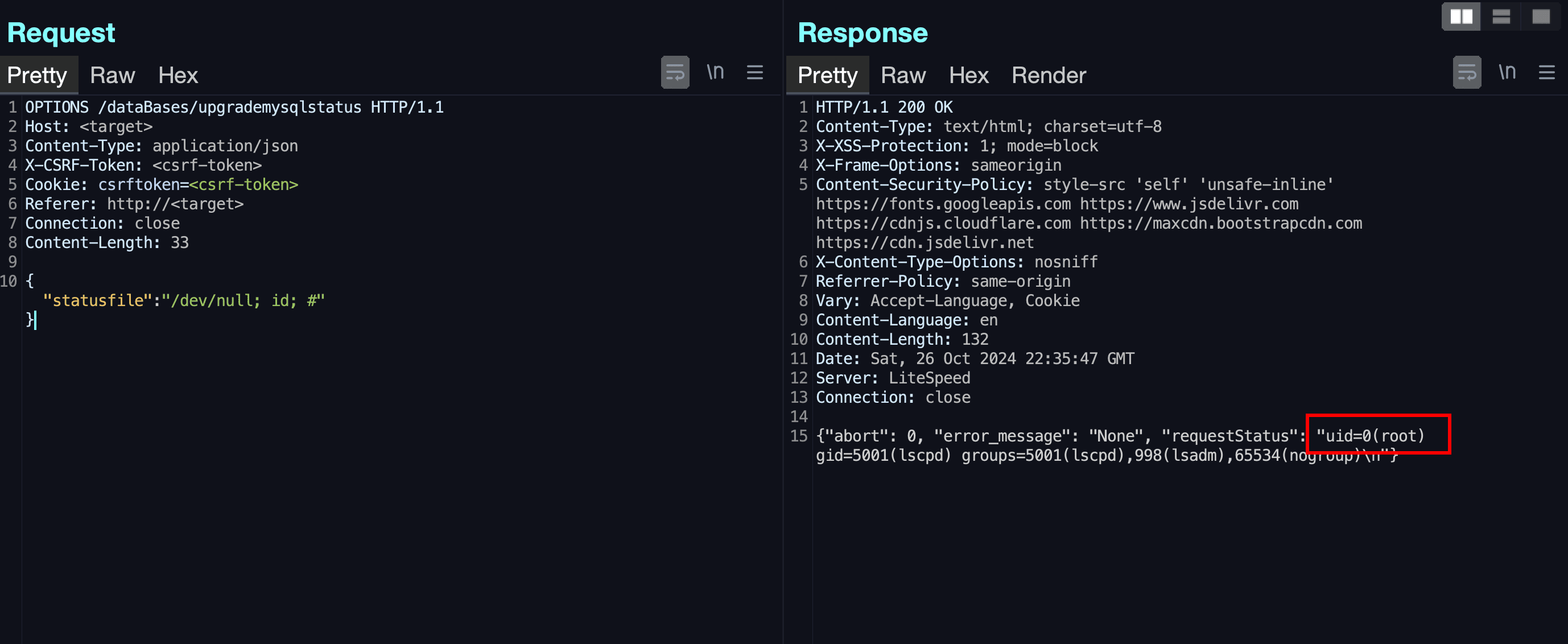
According to DreyAnd, “This led to a 0-click pre-auth root RCE on the latest version (2.3.6 as of now). It’s currently still ‘unpatched’, as in, the maintainers have been notified, a patch has been done but still waiting for the CVE & for the fix to make it to the main release.” The vulnerability resides within CyberPanel’s code structure, which uses Django and is attributed to inconsistent authentication practices across various routes.
The analysis details the improper implementation of authentication checks within the application: “Something that I saw right off the bat is that they were applying authentication checks for every route one-by-one… If I was to write code like this I’d definitely miss checking auth on a couple of routes – and yes, that’s exactly what happened here”. This oversight allows attackers to exploit unchecked routes to gain unauthorized access.
One of the most dangerous aspects of this vulnerability lies in how the software handles subprocesses. As described by DreyAnd, the system “loves piping things to subprocess,” which allows for command injection attacks. The uploaded analysis demonstrates how an attacker could exploit the flaw by manipulating file paths using a vulnerable method called ProcessUtilities.outputExecutioner(), effectively gaining root-level control over the affected server.
What makes the situation even more concerning is the ability to bypass existing security middleware entirely. DreyAnd points out, “The security middleware… does the command injection checks only if the request method is POST… Which means, that we can just do an OPTIONS/PUT/PATCH… and bypass the security middleware completely LOL?“. This gap in security measures makes it all too easy for attackers to execute their exploits.
DreyAnd has provided a proof-of-concept exploit, which he mentions is available on his GitHub repository. According to leak_ix, over 22,000 vulnerable instances have been identified.
— LeakIX (@leak_ix) October 28, 2024
Users are advised to stay vigilant and consider implementing additional access restrictions to prevent exploitation until an official fix is released. You can find the patch commit here.
Related Posts:
- Hackers use Cisco Router flaws to attack Iran, 3,500 routers hacked
- Zero-Click Calendar Invite: Critical macOS Vulnerability Chain Uncovered
- Zerodium increases Outlook zero-click bug bounty to $400,000
- NSO Group Exploits iOS 15 and iOS 16 with Zero-Click Attacks on Civil Society Targets