Overview of ONNX store in EclecticIQ Threat Intelligence Platform
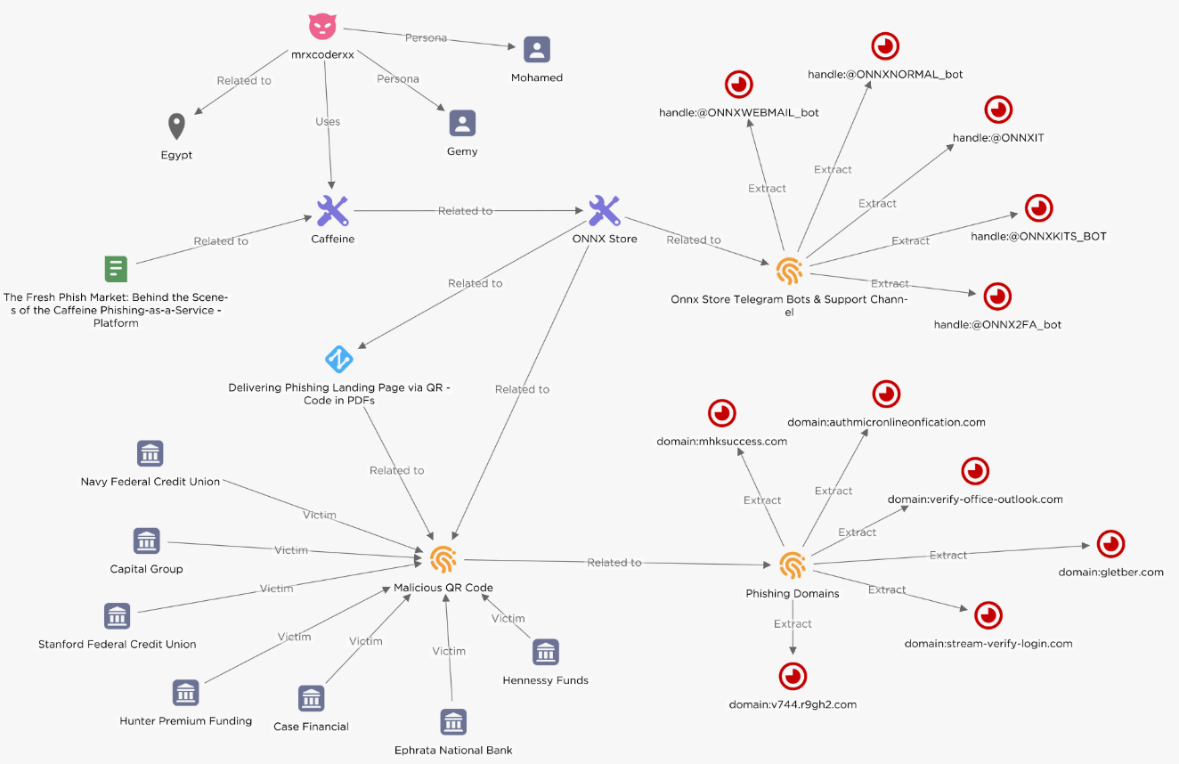
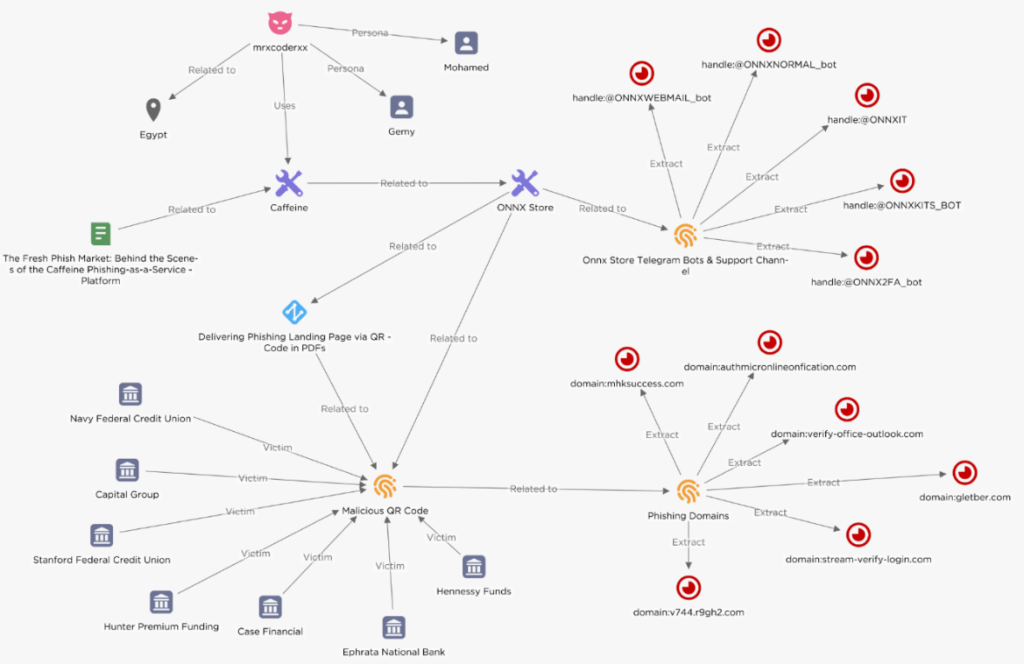
EclecticIQ analysts have recently discovered a sophisticated phishing-as-a-service (PhaaS) platform called ONNX Store, targeting financial institutions worldwide. This platform, believed to be a rebranded version of the infamous Caffeine phishing kit, enables cybercriminals to launch highly effective phishing campaigns with features like 2FA bypass mechanisms and realistic phishing pages.
EclecticIQ Threat Intelligence Platform
EclecticIQ analysts assert with high confidence that ONNX Store is a rebranded version of the Caffeine phishing kit, first discovered by Mandiant in 2022. The similarities in infrastructure and Telegram channel advertising support this assessment. The Arabic-speaking threat actor MRxC0DER (also known as mrxcoderxx) is believed to be the developer and maintainer of the Caffeine kit, based on video demonstrations where Arabic language settings were the default in the browser.
ONNX Store’s rebranding includes improved operational security (OPSEC). Unlike Caffeine, which used a single shared web server, ONNX Store allows threat actors to manage operations through Telegram bots and support channels. Key Telegram bots include:
- @ONNXIT: Manages client support.
- @ONNX2FA_bot: Provides 2FA codes from successful phishing operations.
- @ONNXNORMAL_bot: Delivers Microsoft Office 365 login credentials.
- @ONNXWEBMAIL_bot: Controls a Webmail server for sending phishing emails.
- @ONNXKITS_BOT: Handles payments and order tracking.
ONNX Store uses Cloudflare to delay the takedown of phishing domains. Cloudflare’s anti-bot CAPTCHA and IP proxying features are exploited by threat actors to evade detection and protect their malicious services. CAPTCHA helps evade phishing website scanners, while IP proxying conceals the original hosting provider, complicating the takedown process.
EclecticIQ analysts observed the use of QR codes in phishing campaigns targeting financial institutions. These QR codes, embedded in PDF documents, direct victims to phishing landing pages upon scanning. This technique, called “quishing,” exploits the lack of mobile device monitoring in many organizations, making it a stealthy method to bypass endpoint detection.
ONNX Store’s phishing kit uses encrypted JavaScript to evade detection. The decryption process involves Base64 decoding and XOR operations, complicating analysis. The decrypted JavaScript captures and relays 2FA tokens, allowing attackers to bypass 2FA security measures and gain unauthorized access to victims’ accounts in real-time.
ONNX Store offers bulletproof hosting services, advertised with slogans like “Everything is allowed” and “Ignore all abuse reports.” These services support a range of illegal activities, providing high-performance features and continuous availability, making them attractive to cybercriminals.
Phishing toolkits like ONNX Store enable cybercriminals to easily launch sophisticated phishing campaigns, increasing the prevalence of credential theft and ransomware attacks. Stolen credentials are often sold on underground forums, providing initial access vectors for ransomware groups, highlighting the broader impact of these platforms on the cybersecurity landscape.
Security professionals and financial institutions are urged to remain vigilant and take proactive measures to protect themselves against this evolving threat. This includes implementing robust email security solutions, educating employees about phishing tactics, and regularly updating security protocols to address emerging threats.