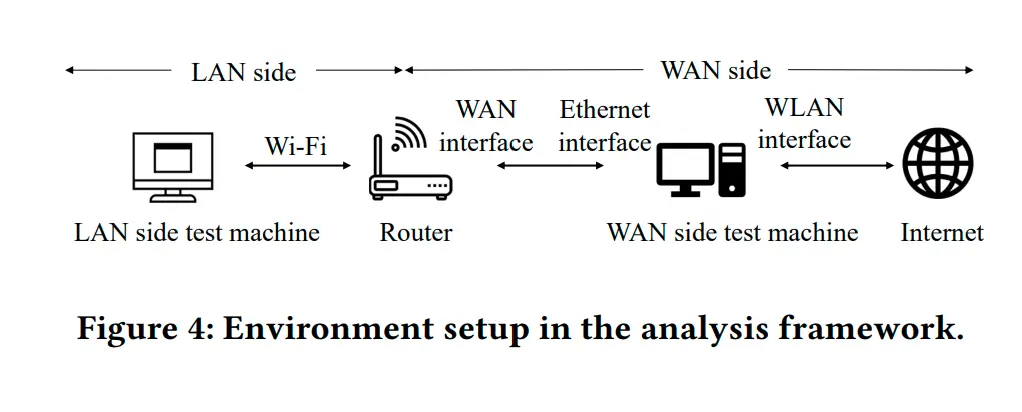
A study titled “Exposed by Default: A Security Analysis of Home Router Default Settings” has shed light on the pervasive vulnerabilities present in home routers, highlighting significant risks associated with their factory default configurations. Conducted by a team of researchers from Nanjing University of Posts and Telecommunications, The Hong Kong Polytechnic University, Carleton University, and Vrije Universiteit Amsterdam, the study scrutinized 40 commercially available routers across 14 brands, uncovering numerous exploitable flaws that compromise both user security and privacy.
The research identified 30 exploitable vulnerabilities, ranging from weak Wi-Fi security protocols to unencrypted firmware updates, posing threats to millions of users globally. The study’s focus was twofold: it analyzed both the initial default settings and what the authors termed deep default settings, which come into effect only after specific features are enabled.
One of the standout discoveries was the exposure of IPv6 local devices due to the lack of firewall protection, allowing adversaries to bypass traditional safeguards and target devices directly. Moreover, many routers continued to support outdated and vulnerable Wi-Fi security protocols such as WPA, and some even retained support for the deprecated TKIP encryption, making them susceptible to replay and packet forgery attacks.
The analysis also found that a significant number of routers used weak admin passwords, lacked proper encryption for firmware updates, and still supported insecure WPS (Wi-Fi Protected Setup) PIN authentication, a well-known vulnerability that attackers can exploit to gain unauthorized access to the network.
In addition to the obvious risks associated with the initial configuration, the researchers highlighted the dangers of deep default settings—features that are disabled by default but often activated by users with minimal scrutiny. For example, guest networks, commonly enabled to provide temporary access for visitors, were found to default to insecure configurations, with no encryption protocols in place. Similarly, remote web access and Telnet/SSH services were found to be vulnerable when enabled, exposing routers to external attacks.
The study stresses that the responsibility for securing home routers must be shared between manufacturers and consumers. While end-users often leave routers in their default state due to convenience or lack of technical expertise, manufacturers are urged to strengthen default configurations, enforce stricter password policies, and implement robust encryption mechanisms for critical communications.
“We found a total of 46 potential vulnerabilities, out of which, we have confirmed 30 to be exploitable in the latest version and reported them to manufacturers or CNVD/CVE,” the researchers noted.
This research serves as a stark reminder of the critical role home routers play in modern digital infrastructure—and the risks posed by lax security practices. As the research highlights, even seemingly benign default settings can leave users exposed to cyber threats. In an era of increasing reliance on home networks, the security of these devices must be prioritized, urging both manufacturers and users to take proactive measures to mitigate potential risks.
Related Posts:
- Multiple Critical Vulnerabilities Found in D-Link WiFi Routers: Immediate Firmware Updates Advised
- D-Link Won’t Fix 4 RCE Vulnerabilities in DIR-846W Router
- CVE-2024-42815 (CVSS 9.8): Buffer Overflow Flaw in TP-Link Routers Opens Door to RCE
- Facebook has been exposed to provide user privacy to Apple, Samsung and dozens of other device makers