
In a detailed report from Team Axon—led by Alon Klayman and Uri Kornitzer—researchers have revealed on a sophisticated campaign targeting Chrome extension developers. This operation exemplifies the evolving nature of cyber threats, combining phishing, credential theft, and malicious code injection to compromise both developers and end users.
The campaign first came to light on December 24, 2024, when Cyberhaven, a cybersecurity firm specializing in secure browser extensions, disclosed a tampered version of their Chrome extension on the Chrome Web Store. According to Cyberhaven, the breach stemmed from a successful phishing attack that tricked an employee into granting malicious OAuth consent, providing attackers access to the Google Chrome Web Store.
Team Axon’s investigation revealed that the tampered extension contained malicious code enabling command-and-control (C2) communication and credential theft. “Research findings indicate that this threat campaign, targeting Chrome extension developers, has been active for at least seven months and possibly longer,” the report states.
Further analysis uncovered that this was not an isolated incident. The campaign targeted multiple Chrome extension developers using similar phishing methods, leading to the compromise of at least 35 additional extensions, potentially affecting over 2.5 million users. Alarmingly, the attackers registered a new malicious domain as recently as December 28, 2024.
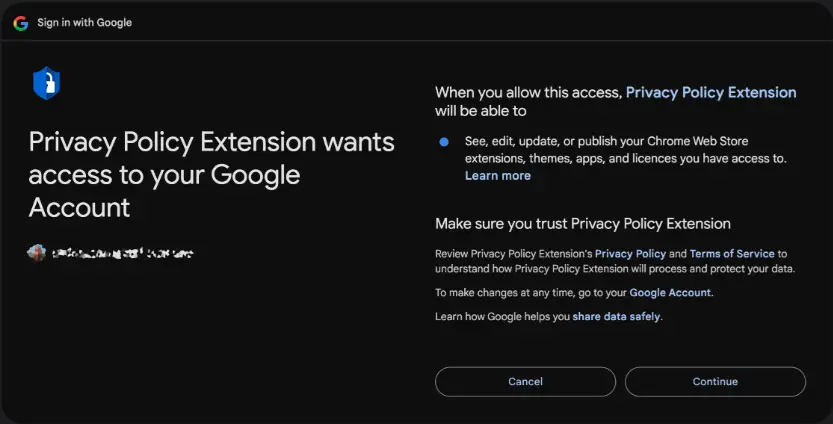
The attack begins with phishing emails purportedly from Google, falsely claiming that the recipient’s extension violates Chrome Web Store policies. Developers are redirected to a fraudulent OAuth consent page, where they are tricked into granting permissions to a malicious application. These permissions allow attackers to tamper with Chrome extensions, injecting malicious code designed to:
- Establish C2 communication.
- Steal sensitive data, including cookies.
“This highly targeted request appeared legitimate, as it focused exclusively on Chrome extension-related activities,” the report explains.
Team Axon identified over 90 malicious domains and 30 IP addresses associated with this campaign. To aid detection and response efforts, the report includes tailored threat-hunting queries and IOCs, empowering security teams to uncover related threats in their infrastructures.
The report concludes with an urgent call for organizations to act quickly. “This highlights the urgency for organizations to act quickly and deploy detection and mitigation measures,” Team Axon warns.
Related Posts:
- VEILDrive: A Novel Attack Exploits Microsoft Services for Command & Control
- Malicious Chrome Extension Infects Over 100,000 Users
- Trojan Malware Infiltrates Browser Extensions, Impacts 300,000 Users
- New Chrome and Firefox malicious extensions prevent user removal to hijack browsers