365-Stealer: Executing the Illicit Consent Grant Attack
365-Stealer
365-Stealer is a tool written in Python3 which can be used in illicit consent grant attacks. When the victim grants his consent we get their Refresh Token which can be used to request multiple Tokens that can help us in accessing data like Mails, Notes, Files from OneDrive, etc. Doing this manually will take a lot of time so this tool helps in automating the process.
365-Stealer comes with 2 interfaces:
- CLI – The CLI is purely written in python3.
- Web UI – The Web UI is written in PHP and it also leverages python3 for executing commands in the background.
About Illicit Consent Grant Attack
In an illicit consent grant attack, the attacker creates an Azure-registered application that requests access to data such as contact information, email, or documents. The attacker then tricks an end-user into granting consent to the application so that the attacker can gain access to the data that the target user has access to. After the application has been granted consent, it has user account-level access to the data without the need for an organizational account.
In simple words when the victim clicks on that beautiful blue button of “Accept”, Azure AD sends a token to the third party site which belongs to an attacker where the attacker will use the token to perform actions on behalf of the victims like accessing all the Files, Read Mails, Send Mails, etc.
Features
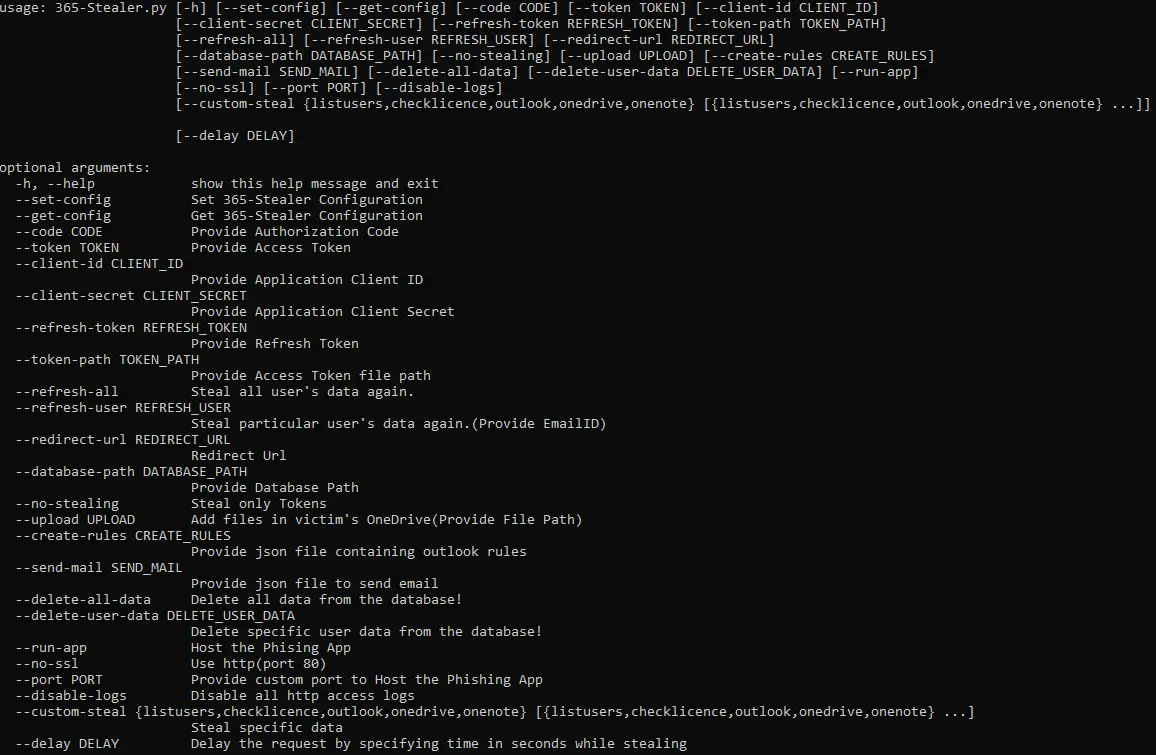
- Steals Refresh Token which can be used to grant new Access Tokens for at least 90 days.
- Can send mails with attachments from the victim user to another user.
- Creates Outlook Rules like forwarding any mail that the victim receives.
- Upload any file in victims OneDrive.
- Steal’s files from OneDrive, OneNote, and dump all the Mails including the attachments.
- 365-Stealer Management portal allows us to manage all the data of the victims.
- Can backdoor .docx file located in OneDrive by injecting macros and replace the file extension with .doc.
- All the data like Refresh Token, Mails, Files, Attachments, list of all the users in the victim’s tenant, and our Configuration are stored in a database.
- Delay the request by specifying time in seconds while stealing the data
- Tool also helps in hosting the dummy application for performing illicit consent grant attack by using –run-app in the terminal or by using 365-Stealer Management.
- By using –no-stealing flag 365-Stealer will only steal token’s that can be leverage to steal data.
- We can also request New Access Tokens for all the user’s or for specific user.
- We can easily get a new access token using –refresh-token, –client-id, –client-secret flag.
- Configuration can be done from 365-Stealer CLI or Management portal.
- The 365-Stealer CLI gives an option to use it in our own way and set up our own Phishing pages.
- Allow us to steal particular data eg, OneDrive, Outlook, etc. by passing a –custom-steal flag.
- All the stolen data are saved in the database.db file which we can share with our team to leverage the existing data, tokens, etc.
- We can search emails with a specific keyword, subject, user’s email address, or by filtering the emails containing attachments from the 365-Stealer Management portal.
- We can dump the user info from the target tenant and export the same to CSV.
Install & Use
Copyright (C) Altered Security Pte Ltd.