“Mirror, mirror, on the wall, who is the most insecure of them all?”
The first time I read this quote, I laughed a lot. As a developer, it seemed funny to me in more ways than one. I can imagine a digital-age fairy tale where the evil queen pronounces these words, programs in Python, and steals tons of data. And instead of trying to murder Snow White, she keeps escaping the GDPR. Sounds fun, doesn’t it?
Well, like the Snow White of our fairy tale would eventually teach you, the moral of the story would be to make sure you are always ready for an attack and always ensuring protection. This is true of our fairy tale and digital security in real life.
The following are 4 key pieces of advice that will help you protect your systems against attacks.
#1 Never Stop Learning
Nowadays, we can get a lot of content almost instantly and for a meager price (or even free). This enables us to do a lot—stay informed and study. So the key principle is always to think ahead and be prepared for any scenario. Your hackers and their tools are always evolving, so you need to evolve and stay constantly updated too. There are a lot of ways to do it.
A good place to start is with books. You can take a looks at titles like:
- The Hacker Playbook—It’s a series of 3 books that handles many different aspects of the internet and hacking.
- Blue Team Handbook: Incident Response Edition—It strongly focuses on the blue team side. It provides useful aspects about how to prevent or handle an incident.
- Red Team Field Manual or Blue Team Field Manual—These are two must-haves if you already know how to juggle between terminals and CLI commands.
You can also get great eBooks for meager prices on websites like Humble Bundle. If you still prefer the paper sheet version, you can seek books on used websites like eBay or look in libraries.
If you prefer staying on a lower budget, you can always seek other materials on this Github Repository or Udemy. You must never stop learning. The more you know, the more you can see!
#2 Backup
Backups are the things you wish you had done before the accident occurred. Backups are fundamental. However, just having a backup isn’t enough. You must have a backup and a restore strategy and policy. A backup strategy involves picking:
- the count of backups to keep
- the periodicity of your backups
- the location and medium
- the backup strategy (incremental/copy everything/encryption)
A good backup policy is to store at least 3 short-distance backups (weekly as an example) of your data in different locations. Two backups must be in place: one physically in the same “room” as your original data, one inside the same department. The third must be in a completely different location (to avoid natural disaster hits). It can be a physical copy (like a NAS or series of disks) or stored in a replicated cloud.
A backup strategy is a difficult pick. You can use some specialized software or build your own. If you know bash scripting, you’ve probably used tools like tar, find, or rsync at least once, so you probably know how powerful they are. I’ll embed under here a sample bash backup script, but stay alert using it. It’s just a sample for demonstrative purposes.
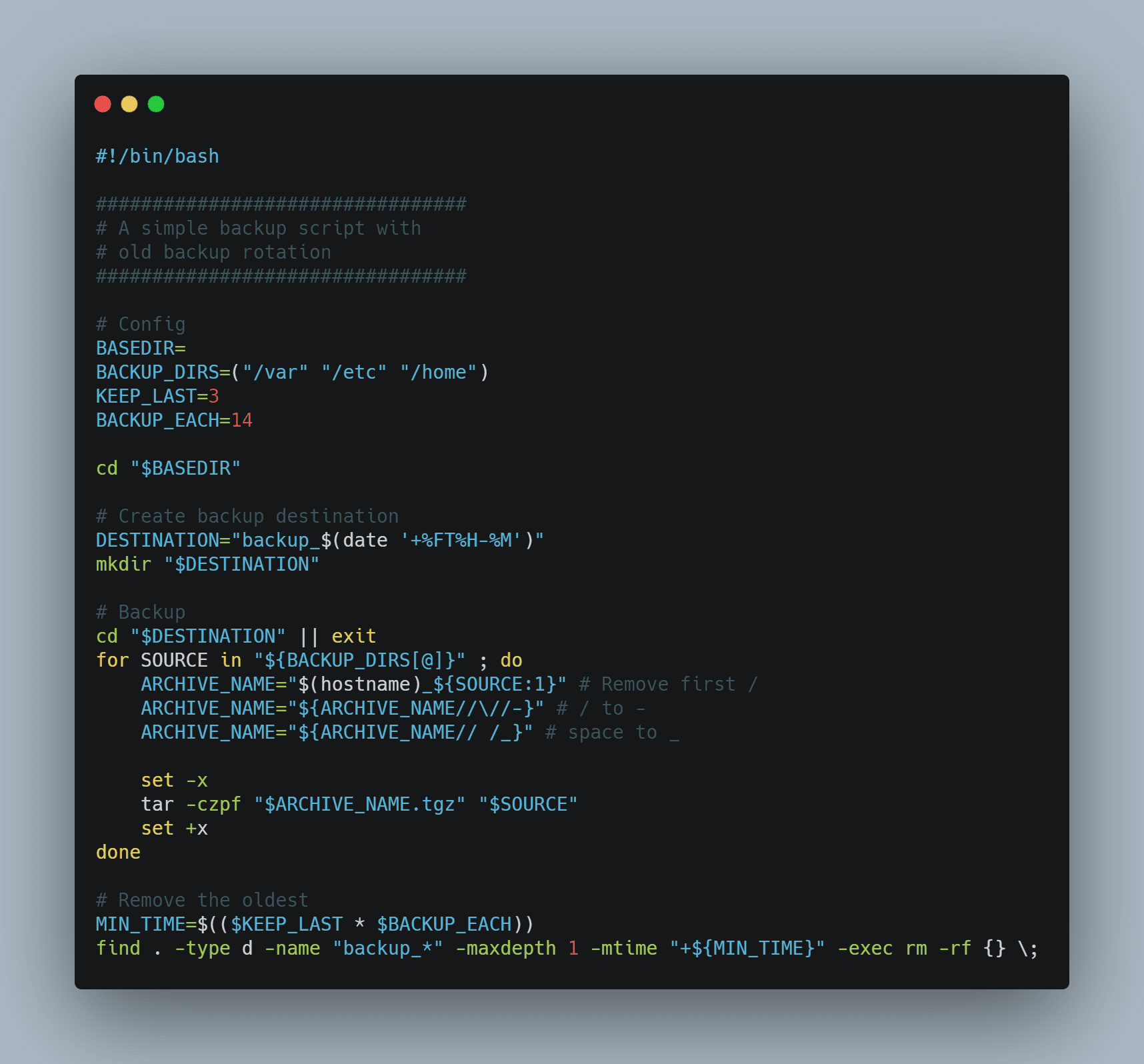
Now pick a backup strategy, set a recurring event on your calendar, and backup your data before it’s too late.
#3 Active Testing
If you already have your data backed up, you should keep an eye on your active installations. Active testing tools continuously show you how everything is working. Using a testing platform, you can check your network and devices for common and known attacks.
The testing tool I’ll talk about here is called Cymulate, an active testing platform.
Cymulate allows you to perform cyber attacks on your target machines and check how they react. You can test your targets against different kinds of vectors and test your incident response procedures.
After setting up your environment, you can use Cymulate by registering an account (new users get a 14-day free trial) and setting up your targets. The setup consists of installing the Cymulate agent and registering it via the authentication token they provide. The authentication token will let the agent register your machine on the Cymulate backend as “ready for injection”.
Thereafter, you can launch attacks from the Cymulate dashboard and check how your target responds. The Cymulate dashboard has a lot of vectors you can perform- I have tested two attack vectors so far.
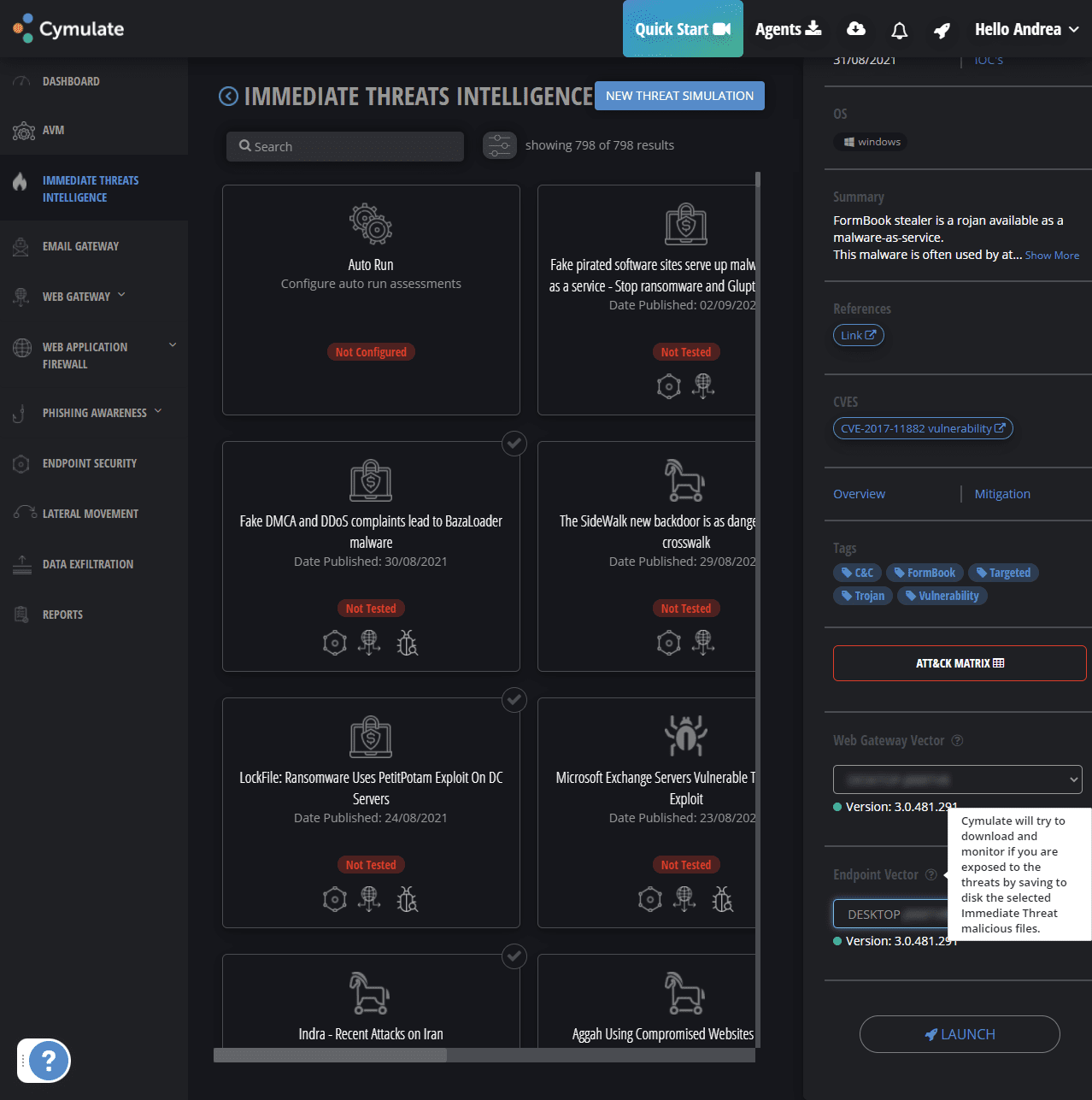
After selecting an attack, you can see how it works in detail by expanding the attack matrix.
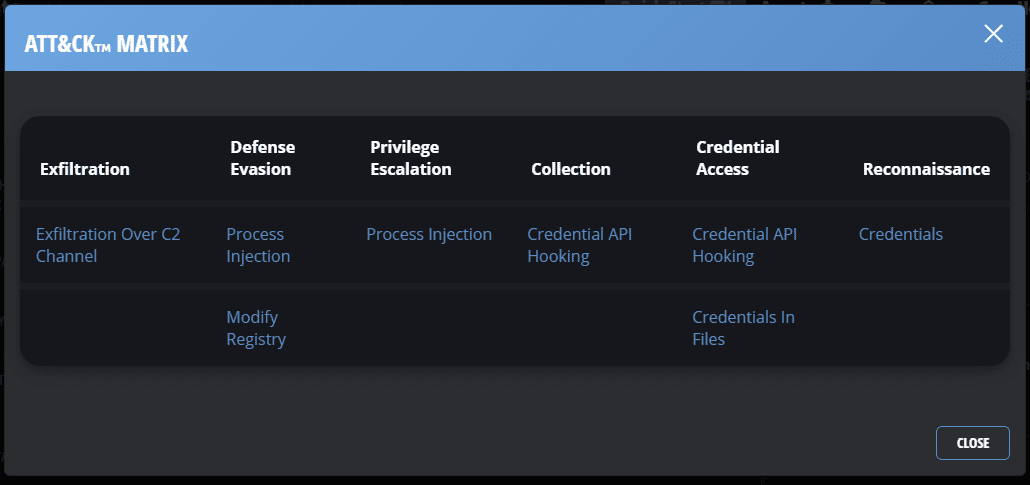
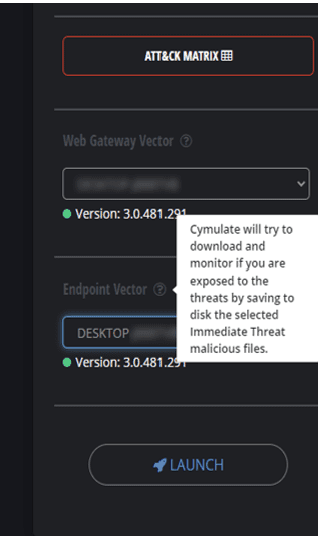
In my case, I tried the “FormBook” attack. FormBook stealer is a trojan available as a malware-as-a-service. It injected the endpoint and the web gateway.
This allows you to test the whole environment. After that, Cymulate will try injecting different payloads on both the target machines and report their responses. If you have a separated web gateway and machine and installed Cymulate on both, you can perform the vector attack by submitting different parts of the attack to both the targets.
I tested both on the same target, a clean windows machine with the default windows defender, no other firewalls. After I started the attack, Defender got triggered and instantly outlined the threat and deleted it.
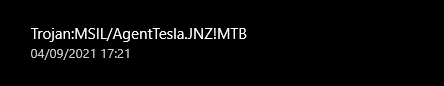
This is only the tip of the iceberg. On Cymulate, I still got a 60% score.
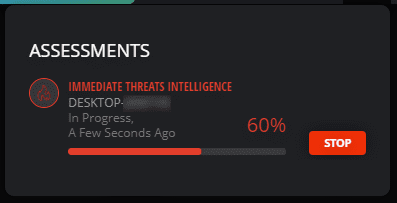
That surprised me, so I looked at the report and saw that executable payloads didn’t get in, but malicious URLs weren’t blocked by the firewall. This doesn’t necessarily mean that you’re vulnerable at 100% but that you may be vulnerable on that side.
While it’s true that it’s unlikely that I would visit that URL and my browser wouldn’t block it, all it takes is one bad site, or one spam mail opened accidentally to compromise your system.
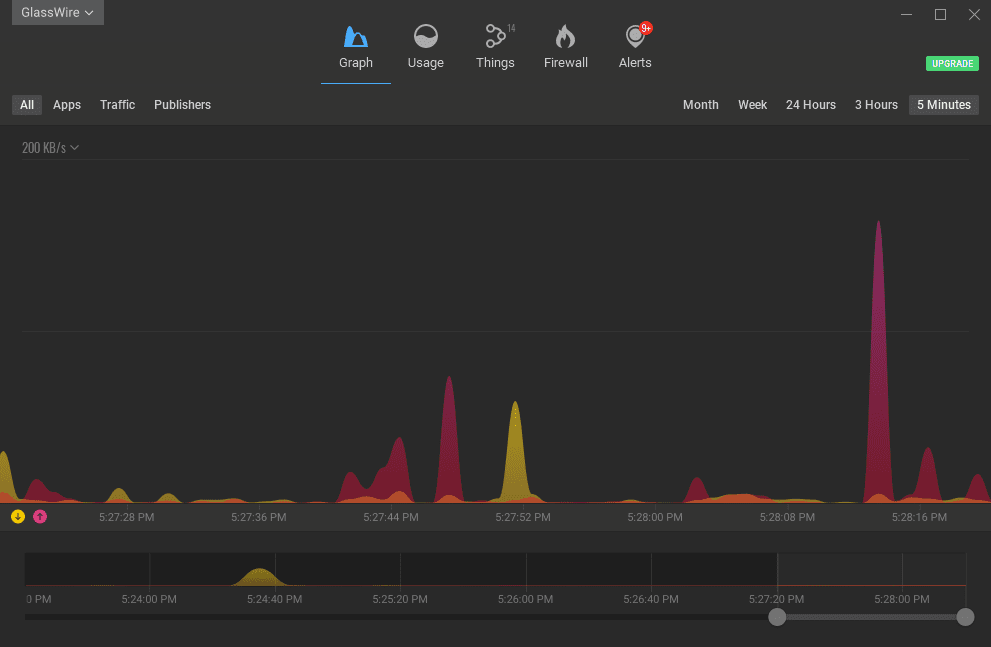
#4 Active Monitoring

Testing is a great way to know if your infrastructure is good. But once you have done that, you need to keep monitoring what’s happening. Monitoring is usually delegated to a firewall that, if you have a budget, is usually hardware. But you can, and should, combine a hardware firewall with a software firewall. A great software Firewall is Glasswire.

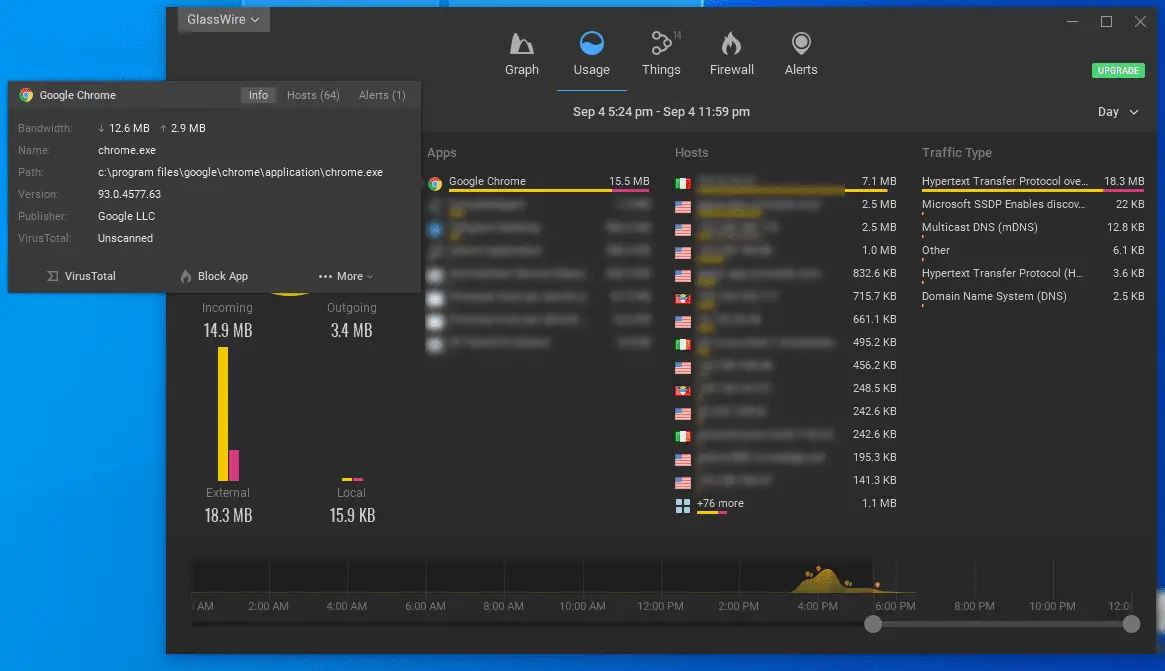
With Glasswire, you can check your current and past network activity and inspect it in detail by analyzing the apps, the hosts, and the traffic type passing by your network card.
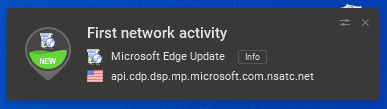
Once an app opens a new connection for the first time, you instantly receive a notification about its activity. And if you pay for the premium version, Glasswire can act as middleware and stop the connection for you.

It can even scan for your network devices by sniffing the traffic passing by your network card and checking their IP and MAC addresses.
Active monitoring of a network can be handy for knowing what’s going on with your network at any point.
Is Your Data Safe?
The cyberworld is always spawning new ways to own you and your data, and having strong strategies and policies may put you in an advantageous position. The blue team (the defenders) is always at a disadvantage compared to the red team. The red team (aka the attackers) always has to find new ways to attack and steal your data.