403-bypass: comprehensive suite of Bash scripts for probing 403 bypasses in web security

403-bypass
Are you interested in web security and want to test your skills against potential 403 bypasses? If so, you’ve come to the right place! This project is a comprehensive suite of Bash scripts, meticulously designed for the purpose of probing 403 bypasses in web security. Whether you’re a beginner or an expert, this tool will help you discover new ways to bypass 403 errors and access restricted resources.

Features
- This tool offers four different scripts, each with its own unique functionality and options.
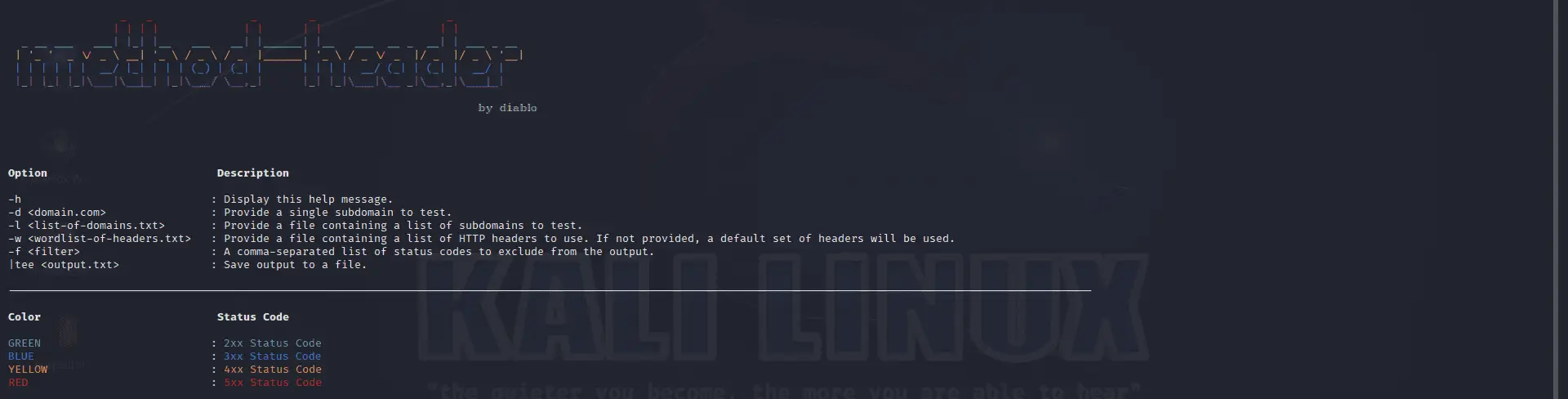
- You can use method-header.sh to test different HTTP methods, headers, HTTP protocol, and HTTP versions work together against the target URL.
- You can use headers.sh to fuzz various headers with different values against a target URL.
- You can use user-agent-fuzz.sh to fuzz the user-agent header with different values against a target URL.
- You can use methods.sh to test different HTTP methods against a target URL.
- For an in-depth understanding of the features offered by this tool, I invite you to visit my Medium website. The link provided will guide you to a wealth of information tailored to enhance your user experience and broaden your knowledge about the tool’s capabilities. Your journey to mastery begins with a single Click.
Installation
To install this tool, simply follow these steps:
- git clone https://github.com/diiablo00/403-bypass
- cd 403-bypass
- chmod +x *.sh
Usage
To use this tool, simply run the desired script with the appropriate options. For example:
- ./method-header.sh -h
- ./headers.sh -h
- ./user-agent-fuzz.sh -h
- ./methods.sh -h
You can also view the help menu of each script by using the -h option.
Source: https://github.com/diiablo00/





