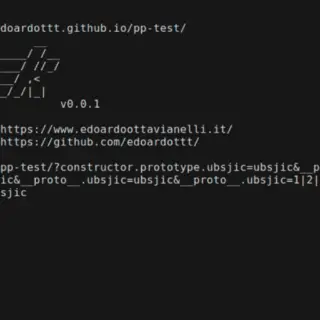
pphack: The Most Advanced Client-Side Prototype Pollution Scanner
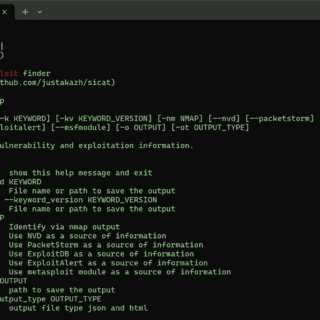
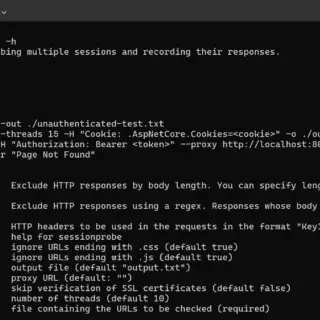
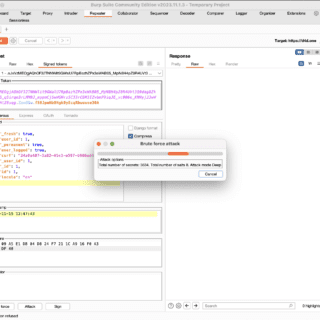
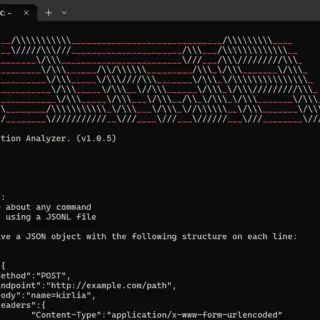
pphack pphack is a CLI tool for scanning websites for client-side prototype pollution vulnerabilities. Feature Fast (concurrent workers) Default payload covers a lot of cases Payload and Javascript customization Proxy-friendly Support output in a...