Category: Vulnerability Analysis
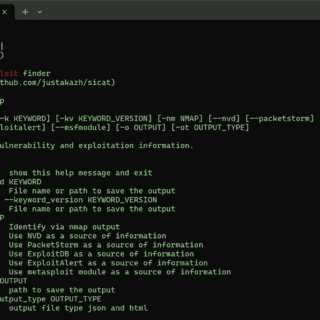
SiCat – The useful exploit finder SiCat is an advanced exploit search tool designed to identify and gather information about exploits from both open sources and local repositories effectively. With a focus on cybersecurity,...
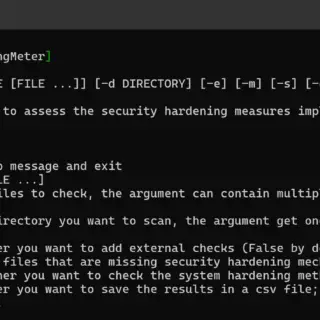
Hardening Meter HardeningMeter is an open-source Python tool carefully designed to comprehensively assess the security hardening of binaries and systems. Its robust capabilities include thorough checks of various binary exploitation protection mechanisms, including Stack...
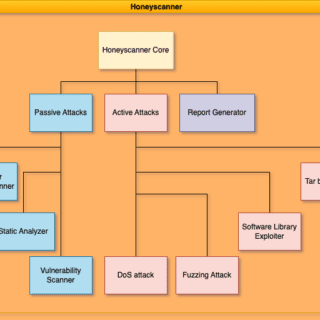
Honeyscanner – A vulnerability analyzer for Honeypots Honeyscanner is a vulnerability analyzer for honeypots designed to automatically attack a given honeypot, in order to determine if the honeypot is vulnerable to specific types of...
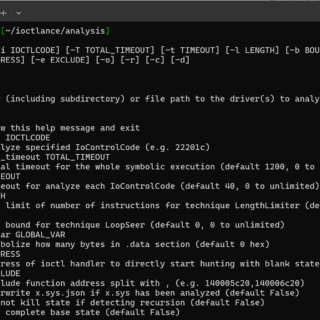
IOCTLance Presented at CODE BLUE 2023, this project titled Enhanced Vulnerability Hunting in WDM Drivers with Symbolic Execution and Taint Analysis introduces IOCTLance, a tool that enhances its capacity to detect various vulnerability types in Windows Driver...
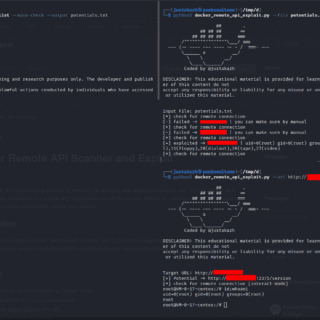
Docker Remote API Scanner and Exploit This repository contains a Docker Remote API Scanner and Exploit tool designed for educational and research purposes. It enables users to perform security assessments and experiments related to...
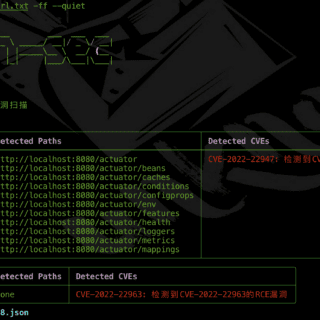
SBSCAN SBSCAN is a penetration testing tool specifically designed for the Spring framework, capable of scanning specified sites for Spring Boot sensitive information and verifying related Spring vulnerabilities. Most Comprehensive Dictionary for Sensitive Paths:...
VulnMapAI VulnMapAI combines the power of Nmap’s detailed network scanning and the advanced natural language processing capabilities of GPT-4 to generate comprehensive and intelligible vulnerability reports. It aims to facilitate the identification and understanding...
GraphGenie GraphGenie is a bug-finding tool to detect logic bugs and performance issues (we also find internal errors) in graph database management systems. Specifically, unlike most existing testing works mutating query predicates, GraphGenie leverages...
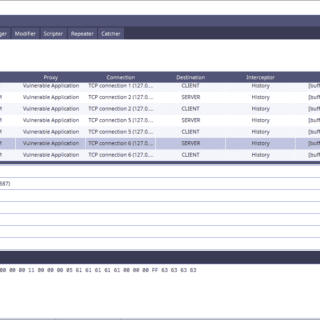
PEnetration TEsting Proxy PETEP (PEnetration TEsting Proxy) is an open-source Java application for creating proxies for traffic analysis & modification. The main goal of PETEP is to provide a useful tool for performing penetration tests...
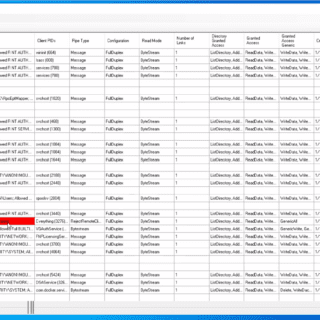
PipeViewer A GUI tool for viewing Windows Named Pipes and searching for insecure permissions. PipeViewer is a GUI tool that allows users to view details about Windows-named pipes and their permissions. It is designed...
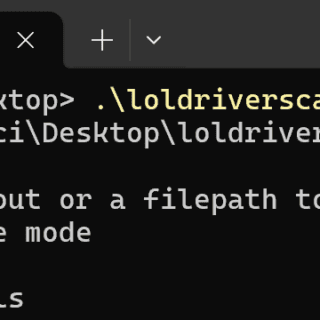
LolDriverScan LolDriverScan is a golang tool that allows users to discover vulnerable drivers on their system. This tool fetches the loldrivers.io list from their APIs and scans the system for any vulnerable drivers This project is...
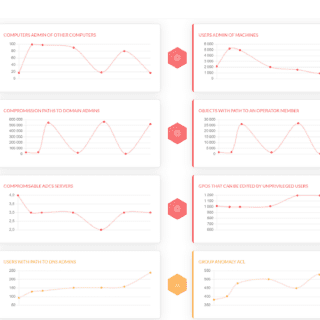
ADMiner ADMiner is an Active Directory audit tool that leverages cypher queries to crunch data from the BloodHound graph database (neo4j) and gives you a global overview of existing weaknesses through a web-based static report, including...
Sekiryu This Ghidra Toolkit is a comprehensive suite of tools designed to streamline and automate various tasks associated with running Ghidra in Headless mode. This toolkit provides a wide range of scripts that can...
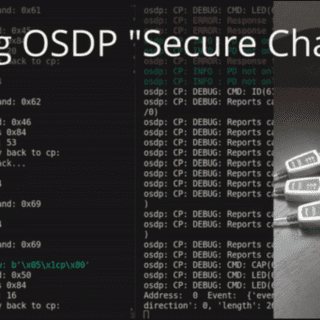
OSDP (Open Supervised Device Protocol) Vulnerabilities Attack #1: Encryption is Optional OSDP supports, but doesn’t strictly require, encryption. So your connection might not even be encrypted at all. Attack #1 is just to passively listen...
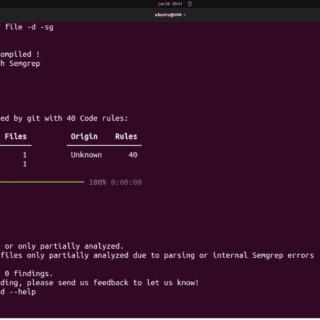
Noir Noir is an attack surface detector from source code. Key Features Automatically identify language and framework from source code. Find API endpoints and web pages through code analysis. Load results quickly through interactions...