PurpleLab: Revolutionizing Cybersecurity Testing with Speed and Simplicity
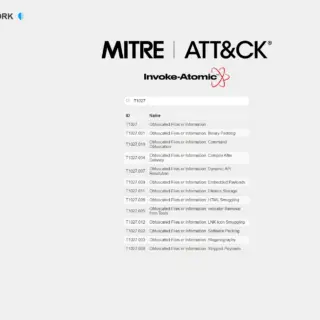
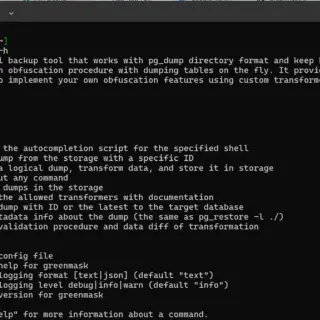
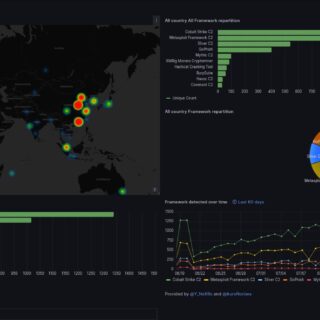
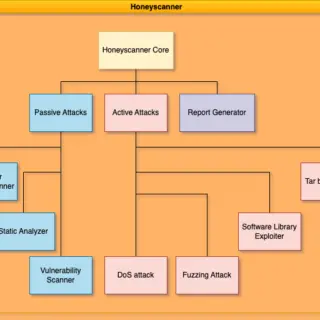
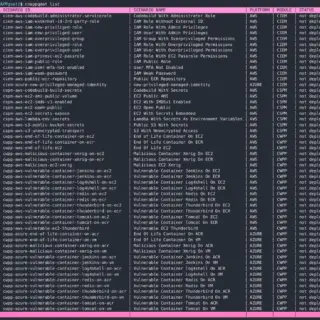
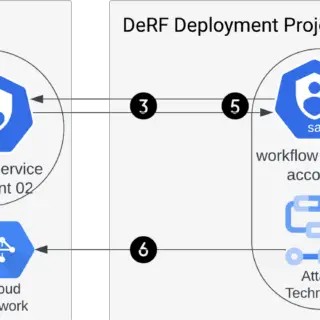
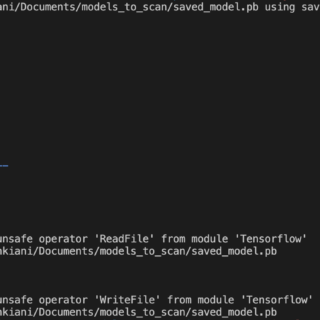
What is PurpleLab? This solution will allow you to easily deploy an entire lab to create/test your detection rules, simulate logs, play tests, download and run malware and mitre attack techniques, restore the sandbox,...