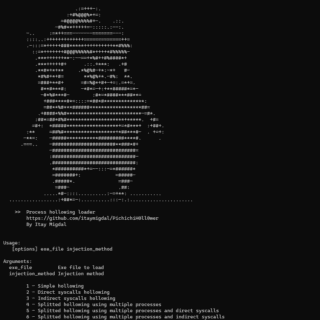
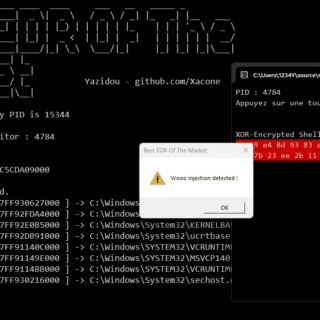
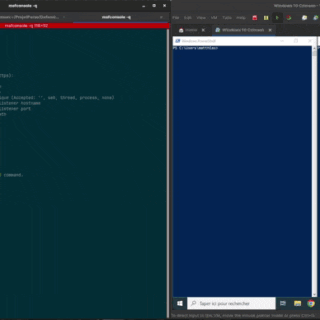
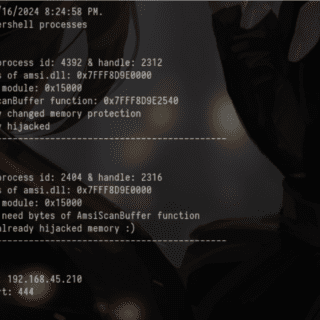
NoArgs: dynamically spoof and conceal process arguments while staying undetected
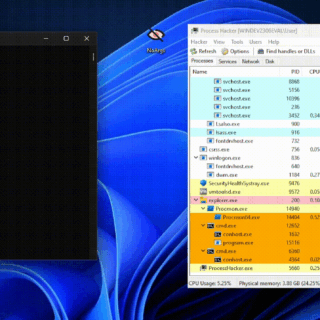
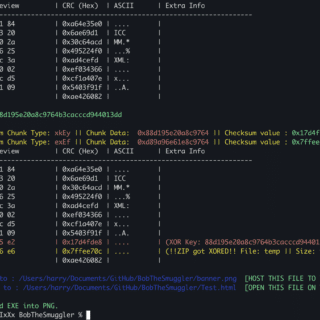
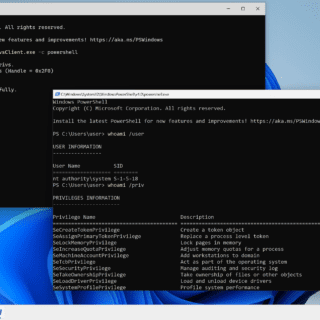
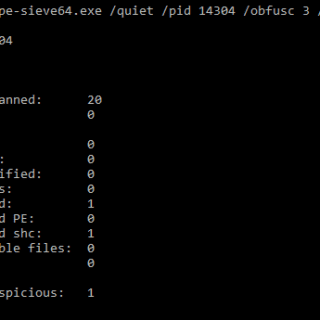
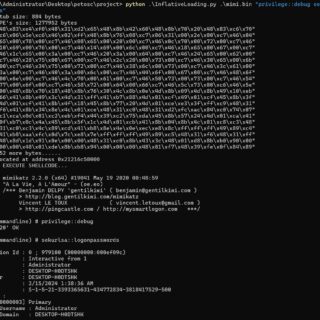
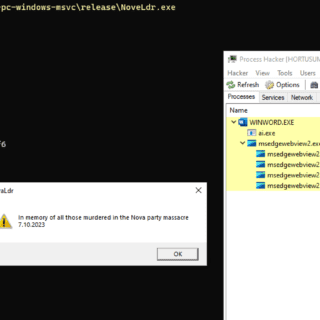
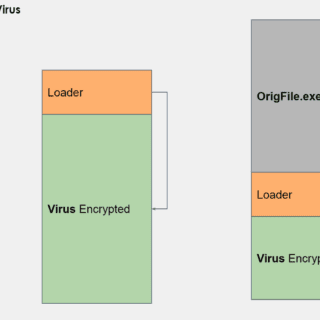
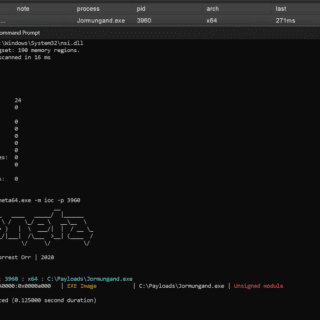
NoArgs: Manipulating and Hiding Process Arguments NoArgs is a tool designed to dynamically spoof and conceal process arguments while staying undetected. It achieves this by hooking into Windows APIs to dynamically manipulate the Windows...