Category: Maintaining Access
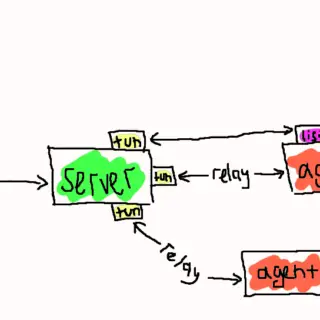
Ligolo-mp Ligolo-mp is a more specialized version of Ligolo-ng, with client-server architecture, enabling pentesters to play with multiple concurrent tunnels collaboratively. Also, with a sprinkle of less important bells and whistles. Features Everything that you...
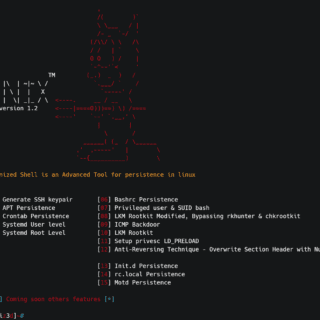
D3m0n1z3dShell Demonized Shell is an Advanced Tool for persistence in Linux. Demonized Features Auto Generate SSH keypair for all users APT Persistence Crontab Persistence Systemd User level Systemd Root Level Bashrc Persistence Privileged user...
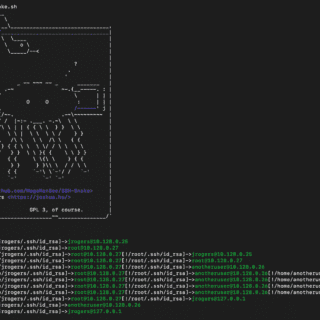
SSH-Snake: Automated SSH-Based Network Traversal SSH-Snake is a powerful tool designed to perform automatic network traversal using SSH private keys discovered on systems, to create a comprehensive map of a network and its dependencies,...
DynastyPersist A CTF Tool for Linux persistence (KOTH, Battlegrounds) A powerful and versatile Linux persistence script designed for various security assessment and testing scenarios. This script provides a collection of features that demonstrate different...
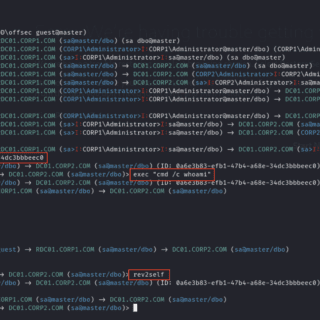
MSSqlPwner MSSqlPwner is an advanced and versatile pentesting tool designed to seamlessly interact and pwn MSSQL servers. That tool is based on impacket, which allows attackers to authenticate to databases using clear-text passwords NTLM...
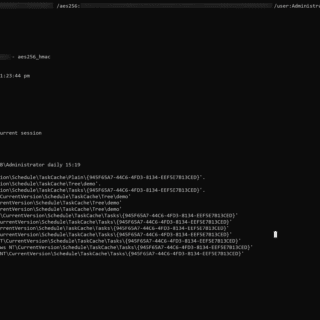
Ghost Scheduled Task While using scheduled tasks as a means of persistence is not a novel approach, threat actors have employed various techniques to conceal their malicious tasks. A notable method involves removing the SD...
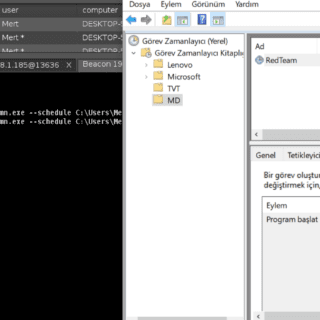
RedPersist RedPersist is a Windows Persistence tool written in C# Usage You can use it with execute-assembly or standalone executable RedPersist.exe –method C:\Path\to\executable.exe RedPersist.exe –help Available Methods –help/-h : Help Menu RedPersist.exe –help –eventviewer : Persistence...
WMIexec Set of Python scripts which perform different ways of command execution via WMI protocol. Blog Post https://whiteknightlabs.com/2023/06/26/navigating-stealthy-wmi-lateral-movement/ Download git clone https://github.com/WKL-Sec/WMIExec.git Use wmiexec_scheduledjob.py Is a Python script which authenticates to a remote WMI...
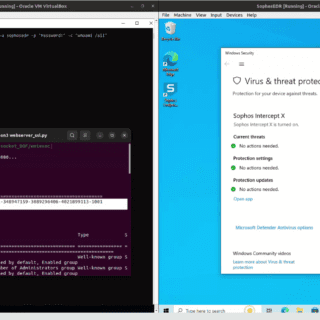
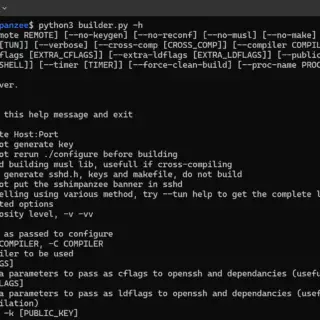
Sshimpanzee Sshimpanzee allows you to build a static reverse ssh server. Instead of listening on a port and waiting for connections, the ssh server will initiate a reverse connection to the attacker’s ip, just like a regular reverse...
KittyStager KittyStager is a stage 0 C2 comprising an API, client, and malware. The API is responsible for delivering basic tasks and shellcodes to be injected into memory by the malware. The client also...
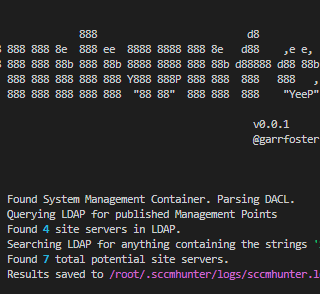
SCCMHunter SCCMHunter is a post-ex tool built to streamline identifying, profiling, and attacking SCCM related assets in an Active Directory domain. The basic function of the tool is to query LDAP with the find...
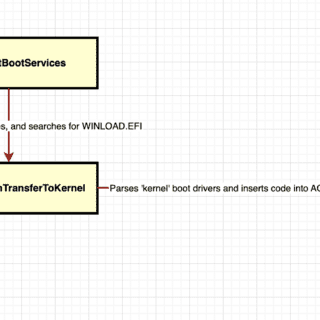
bootlicker bootlicker is a legacy, extensible UEFI firmware rootkit targeting vmware hypervisor virtual machines. It is designed to achieve initial code execution within the context of the windows kernel, regardless of the security settings...
Nidhogg Nidhogg is a multi-functional rootkit for red teams. The goal of Nidhogg is to provide an all-in-one and easy-to-use rootkit with multiple helpful functionalities for red team engagements that can be integrated with...
Kraken – a modular multi-language webshell coded by @secu_x11 Support On the one hand, Kraken is supported by different technologies and versions. The following is a list of where Kraken agents are supported: PHP...
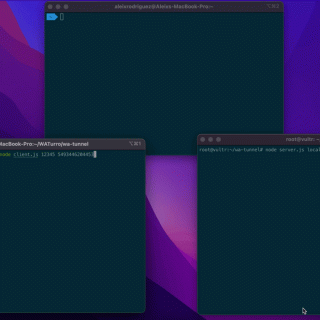
wa-tunnel – TCP Tunneling through Whatsapp This is a Baileys based piece of code that lets you tunnel TCP data through two Whatsapp accounts. This can be usable in different situations, for example, network carriers that...