Category: Web Maintaining Access
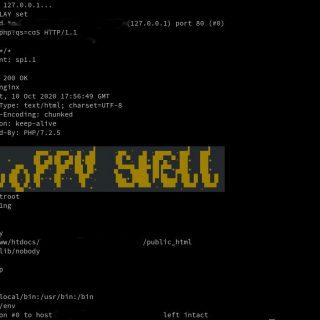
What is Hiphp? The HIPHP BackDoor is an open-source tool that allows for remote control of websites utilizing the PHP programming language via the HTTP/HTTPS protocol. By utilizing the POST/GET method on port 80,...
Kraken – a modular multi-language webshell coded by @secu_x11 Support On the one hand, Kraken is supported by different technologies and versions. The following is a list of where Kraken agents are supported: PHP...
ModSecurity Backdoor This is a proof-of-concept of malicious software running inside of ModSecurity WAF. The software has two main functions: Retrieving the content of files. Running commands and retrieving output (remote shell). Additionally, it...
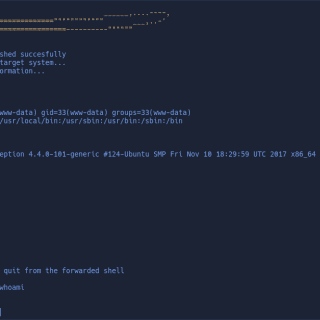
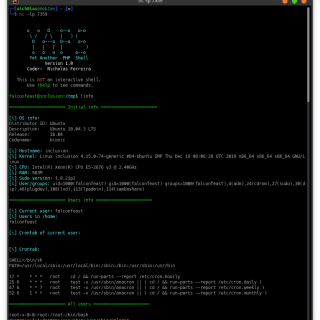
DFShell D3Ext’s Forwarded Shell it’s a python3 script which use mkfifo to simulate a shell into the victim machine. It creates a hidden directory in /dev/shm/.fs/ and there are stored the created fifos. You can...
MSMAP Msmap is a Memory WebShell Generator. Compatible with various Containers, Components, Encoder, WebShell / Proxy / Killer, and Management Clients. Function Dynamic Menu Automatic Compilation Generate Script Lite Mode Graphical Interface Container Java Tomcat7 Tomcat8...
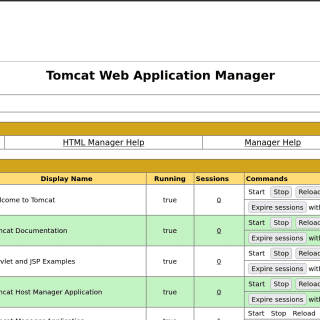
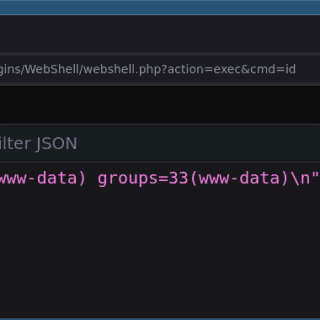
Apache Tomcat webshell application for RCE A webshell application and interactive shell for pentesting Apache Tomcat servers. Features Webshell plugin for Apache Tomcat. Execute system commands via an API with ?action=exec. Download files from the...
WordPress webshell plugin for RCE A webshell plugin and interactive shell for pentesting a WordPress website. Features Webshell plugin for WordPress. Execute system commands via an API with ?action=exec. Download files from the remote system...
presshell – Quick & dirty WordPress Command Execution Shell Execute shell commands on your wordpress server. The uploaded shell will probably be at <your-host>/wp-content/plugins/shell/shell.php Download git clone https://github.com/scheatkode/presshell.git Installation To install the shell, we...
YAPS – Yet Another PHP Shell As the name reveals, this is yet another PHP reverse shell, one more among hundreds available out there. It is a single PHP file containing all its functions and you can control...
Rome WebShell A powerful and delightful PHP WebShell This is a lightweight PHP webshell, using only vanilla JavaScript and CSS, no jQuery/Bootstrap bloat. Features Fully interactive file explorer, browser directories, and download files instantly Upload files directly from...
slopShell php webshell For this shell to work, you need 2 things, a victim that allows php file upload(yourself, in an educational environment) and a way to send http requests to this webshell. How...
Gel4y Mini Shell Backdoor Gel4y Webshell is a backdoor built using the PHP programming language in a stealth mode that can bypass server security. Each function has been converted into hex code so that...
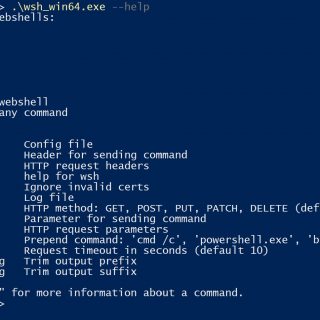
wsh wsh (pronounced woosh) is a web shell generator and command-line interface. This started off as just an http client since interacting with webshells is a pain. There’s a form, to send a command...
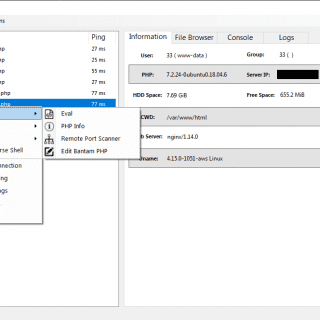
Bantam bantam is an advanced PHP backdoor management tool, with a lightweight server footprint, multi-threaded communication, and an advanced payload generation and obfuscation tool. Features end to end encryption with request unique encryption keys,...
IIS Raid IS Raid is a native IIS module that abuses the extendibility of IIS to backdoor the webserver and carry out custom actions defined by an attacker. Documentation When installed, IIS-Raid will process...