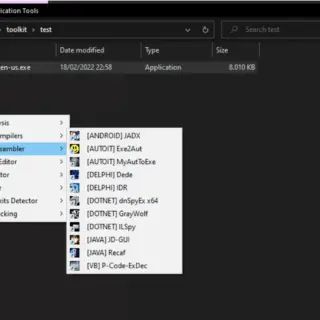
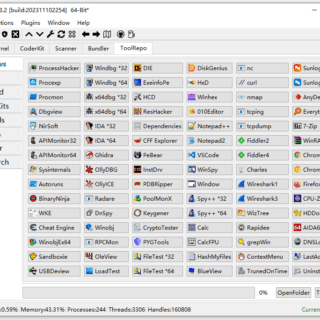
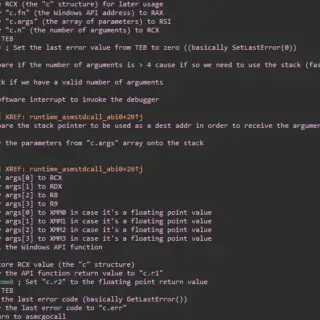
toolkit: The essential toolkit for reversing, malware analysis, and cracking
Indetectables Toolkit This tool compilation is carefully crafted to be useful both for beginners and veterans of the malware analysis world. It has also proven useful for people trying their luck at the cracking...