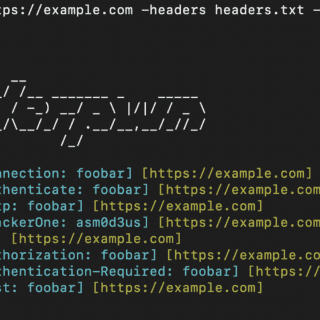
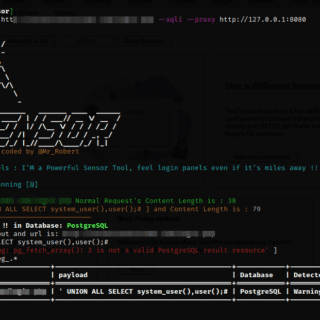
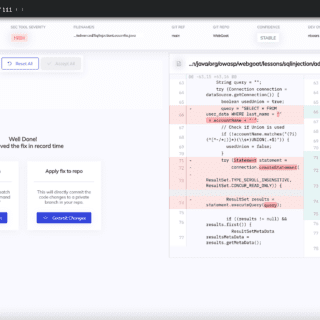
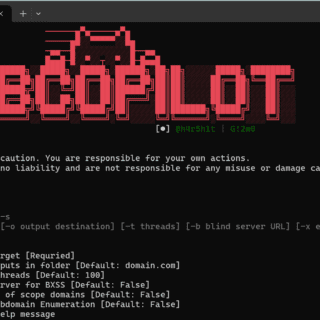
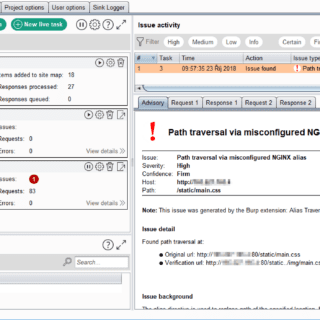
403-bypass: comprehensive suite of Bash scripts for probing 403 bypasses in web security
403-bypass Are you interested in web security and want to test your skills against potential 403 bypasses? If so, you’ve come to the right place! This project is a comprehensive suite of Bash scripts,...