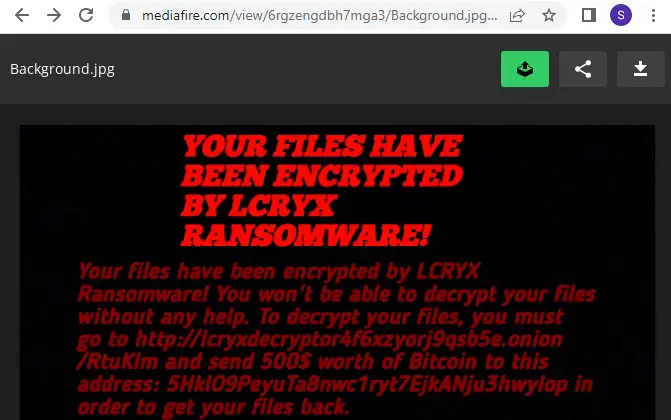
LCRYX ransom note | Image: K7 Security Labs
Ransomware attacks remain a formidable threat to individuals and organizations alike, with LCRYX ransomware making an unwelcome return in February 2025. Originally discovered in November 2024, this VBScript-based malware encrypts victims’ files using a combination of Caesar cipher and XOR encryption, demanding a $500 ransom in Bitcoin for decryption.
According to a recent report by K7 Security Labs, LCRYX has resurfaced with an updated arsenal of evasive techniques and persistence mechanisms, making it a particularly dangerous strain.
Unlike more sophisticated ransomware variants written in compiled languages like C++ or Go, LCRYX relies on VBScript, a relatively simple scripting language that still proves effective in bypassing traditional security mechanisms.
One of its first actions upon execution is escalating privileges: “The script begins by checking whether it is running with administrative privileges. If not, it relaunches itself with the necessary privileges for the next steps.”
Once it gains elevated permissions, LCRYX systematically disables key Windows security controls and forensic tools to block user intervention:
- Disables Task Manager, Command Prompt, and Registry Editor
- Blocks access to System Settings and the Control Panel
- Turns off User Account Control (UAC)
- Prevents execution of system diagnostic tools like msconfig.exe and Autoruns.exe
By crippling these system defenses, the ransomware ensures that users cannot manually stop its execution.
LCRYX employs a variety of persistence techniques that make removal difficult. The malware modifies Windows Registry settings to ensure that its script executes at every login. Additionally, it hijacks system functionalities to sustain control: “The code sets the malicious script as the default shell, causing it to run at login, and also configures it as the debugger for cmd.exe, making sure the script executes every time command prompt is opened.”
Furthermore, LCRYX reconfigures the system’s keyboard and mouse settings, making it even harder for victims to navigate their computers and mitigate the infection.
Once inside a system, LCRYX iterates through key directories and encrypts files using a custom encryption method:
- Applies Caesar cipher and XOR encryption
- Renames files with a .lcryx extension
- Deletes the original files after encryption
As a final blow, LCRYX erases backup files and shadow copies to prevent easy recovery: “It uses vssadmin to delete shadow copies and wbadmin to clear the backup catalog, effectively erasing backup traces from the system.”
After encrypting data, the ransomware displays a ransom note demanding Bitcoin payment for decryption, urging victims to visit a designated dark web payment portal.
LCRYX takes a unique psychological approach to manipulating victims. The malware creates a pop-up message claiming that files have been encrypted, and it asks: “Do you want to decrypt your files?”
If the user clicks “Yes”, the ransomware opens a YouTube video and displays the user’s IP address, creating an unsettling experience. Additionally, the malware runs a script that repeatedly shuts down essential processes every 5 seconds, targeting:
- Task Manager
- PowerShell
- Antivirus programs
This ensures that victims struggle to regain control over their systems.
Perhaps the most devastating feature of LCRYX is its ability to overwrite the Master Boot Record (MBR) with a custom image, effectively rendering the system unbootable: “It runs a PowerShell command that reads an image file and overwrites the MBR of disk drives with its content.”
This tactic mirrors destructive ransomware strains like NotPetya, where the goal is not just extortion but complete system sabotage.
Related Posts:
- Let’s Encrypt Root gains the trust of all major root programs
- Bitdefender released GandCrab Ransomware decryption tool
- Google is strengthening Android security and encourages vendors to strongly encrypt devices