
Security researcher Netsecfish has discovered a command injection vulnerability, tracked as CVE-2024-12987, in the web management interface of popular DrayTek gateway devices. This flaw could enable attackers to execute arbitrary commands remotely, putting over 66,000 Internet-connected devices at risk.
The vulnerability stems from improper input sanitization in the web management interface of the affected devices. Specifically, the /cgi-bin/mainfunction.cgi/apmcfgupload endpoint fails to adequately sanitize the session parameter, enabling attackers to inject malicious commands.
Affected devices include:
- DrayTek Vigor2960
- DrayTek Vigor300B
Both devices running software version 1.5.1.4 are vulnerable.
Netsecfish provided a PoC demonstrating how a simple Python script can exploit the CVE-2024-12987 vulnerability. The script uses raw socket connections to send the malicious request, crafted in hexadecimal format, to the target device. One example included injecting the pwd command to list the current working directory on the device.
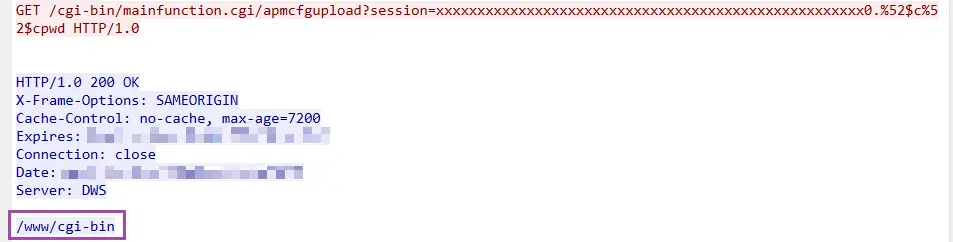
Successful exploitation could lead to unauthorized command execution, enabling attackers to:
- Manipulate configurations.
- Extract sensitive information.
- Launch additional attacks against internal networks.
Given the widespread use of these devices in businesses and homes, this vulnerability poses a significant risk if left unpatched.
DrayTek administrators should take the following immediate actions to protect their devices:
- Apply input validation: Ensure all CGI script parameters undergo strict validation and sanitization.
- Restrict web interface access: Limit access to the management interface by whitelisting trusted IP addresses.
- Update firmware: Monitor for and apply firmware updates from DrayTek once available.
Related Posts:
- CISA Issues Alert: Three Actively Exploited Vulnerabilities Demand Immediate Attention
- Massive Ransomware Campaign Targets DrayTek Routers
- DrayTek Patched Multi Flaws in Routers, Including CVE-2024-41592 (CVSS 10.0)
- CVE-2024-48074: RCE Flaw Discovered in DrayTek Vigor2960 Routers, PoC Published
- DrayTek Router 0day Vulnerability