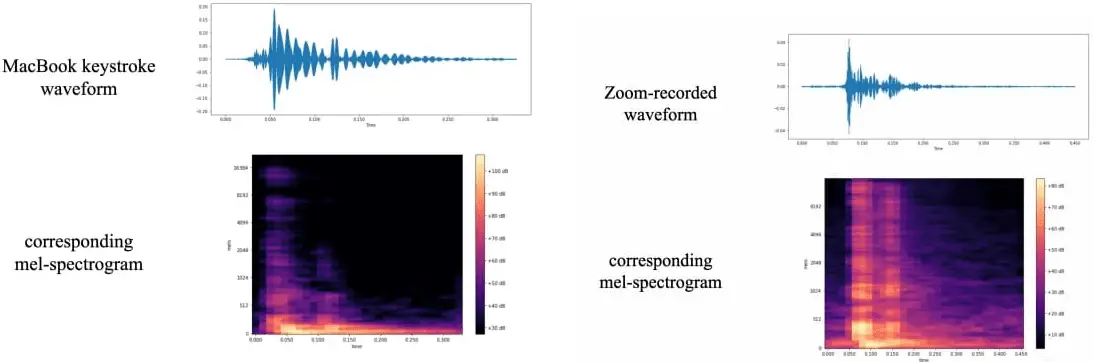
Recently, a research team composed of members from several top British universities conducted a study on acoustic side-channel attacks. In their related paper, they asserted that data could be stolen through the recording of keyboard keystrokes using a microphone, with an accuracy rate reaching 95%.
Side-Channel Attacks (SCA) involve collecting and interpreting signals emitted by a device, such as electromagnetic waves, power consumption, mobile sensors, and sound, among others. While it is well-known that the electromagnetic radiation emitted by wireless keyboards can be detected and read, there exists a more prevalent type of radiation that is largely overlooked by many: the sound of keypresses. Moreover, because of its ubiquity, it is not only easily obtainable but also likely to be met with lower vigilance by potential victims. For example, while typing a password, people generally ensure that it is not visually observed, but they almost never conceal the sound of the keyboard.

In the past, the related technology was far from mature, so acoustic side-channel attacks did not cause significant harm. However, with the latest advancements in microphone and deep learning model performance, attackers have begun to consider the feasibility of such assaults. Unlike other side-channel attacks that require specific conditions and are limited by data rates and distance, acoustic attacks have become increasingly simple due to the proliferation of microphone-equipped devices, allowing for high-quality audio capture.
One can easily conceive of a potential attack scenario where a phone or computer is infected with malicious software, and granted permission to record through the microphone. Furthermore, even if the device itself is secure, there remain many risky scenarios in reality. For instance, collecting keyboard sounds in public areas such as libraries or coffee shops is not challenging; when using conference chat software, the other party could also record the sound of keyboard strikes. Additionally, laptops of the same model often possess identical keyboards, which means that if a popular laptop model is susceptible to an acoustic side-channel attack, a significant portion of people could be at risk.
As such attacks become more refined, they could potentially have serious implications for data security, with sensitive information such as passwords, chat messages, and work documents potentially being leaked to malicious third parties.
The paper also points out that even for very quiet keyboards, the attack model has proven highly effective, so adding dampeners to mechanical keyboards or switching to membrane keyboards is unlikely to be of assistance. To mitigate the risks of these acoustic side-channel attacks, the paper finally offers some applicable precautionary measures, including:
- Utilizing password managers to avoid manual input of sensitive information.
- Deliberately altering typing styles when entering sensitive content.
- Employing white noise or key frequency filters.