
Akamai security researcher Tomer Peled has unveiled a novel attack technique exploiting Microsoft’s legacy UI Automation framework, a tool originally designed to enhance computer accessibility. The findings reveal how attackers can weaponize this framework to bypass modern Endpoint Detection and Response (EDR) systems, creating a significant cybersecurity concern.
Microsoft’s UI Automation framework was introduced during the Windows XP era to aid users with disabilities, offering elevated permissions to manipulate user interface (UI) elements. According to Peled, “UI Automation needs permission to manipulate almost any UI element that is present on the screen.” This capability, though beneficial for accessibility, provides attackers a pathway for stealthy operations.
Peled’s research highlights how attackers can abuse UI Automation to:
- Exfiltrate sensitive data such as credit card details.
- Redirect browsers to phishing websites.
- Manipulate chat applications like Slack and WhatsApp to read and write messages.
One of the most alarming aspects of this technique is its invisibility to detection tools. Peled notes, “All EDR technologies we have tested against this technique were unable to find any malicious activity.” This makes it an attractive option for threat actors, especially since it works on all Windows operating systems from XP onward.
The attack leverages the Component Object Model (COM) to manipulate UI elements across applications. By setting up event handlers, attackers can monitor and interact with UI elements, including reading sensitive data from active windows or simulating user input to execute commands.
Peled’s report outlines proof-of-concept (PoC) attacks to demonstrate the severity of the threat. In one example, an attacker sets up handlers to harvest credit card details entered on an online merchant’s website. In another scenario, a browser is redirected to a phishing site using UI Automation, enabling attackers to deploy exploits or steal credentials.
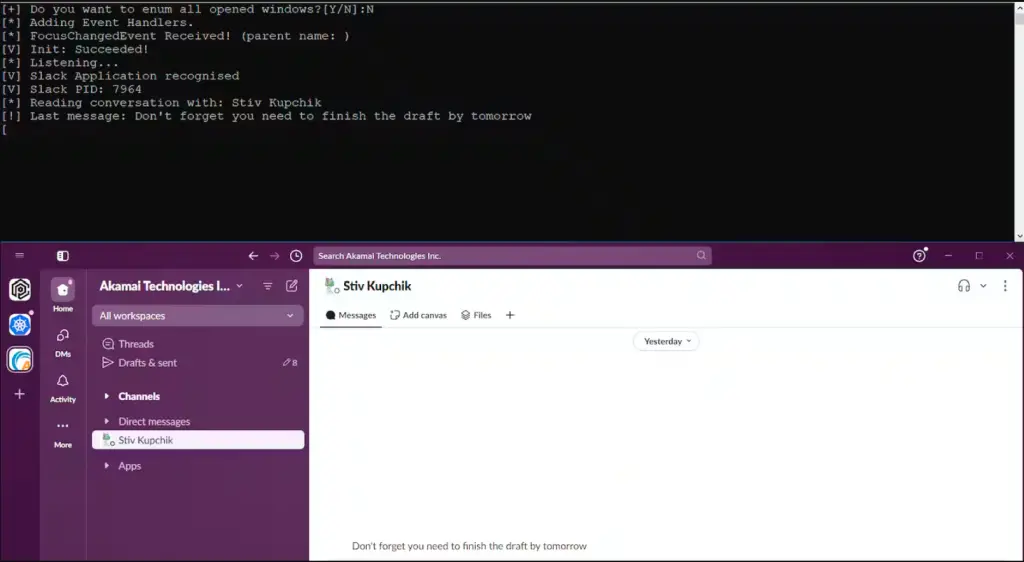
Even messaging applications are not immune. The report details how attackers can use Windows UI Automation to “read the conversation and exfiltrate the data, or set the text box and send messages without it being reflected on the screen.”
The legacy nature of the UI Automation framework poses significant challenges to detection and prevention. To mitigate these threats, Peled recommends monitoring for unusual processes loading the UIAutomationCore.dll and tracking named pipes opened by UI Automation. However, the inherent design of the framework limits comprehensive detection.
While Microsoft has implemented some restrictions, such as limiting UI Automation’s interaction with high-privilege applications, Peled’s findings underscore the potential for skilled attackers to exploit this attack vector. The report concludes, “This analysis is an unfortunate example of how technology created for good can be hijacked for malicious purposes.”
Related Posts:
- Dell Warns of Critical Flaws in Enterprise Products, Including CVE-2024-37143 (CVSS 10)
- PDQ Deploy Vulnerability Exposes Admin Credentials: CERT/CC Issues Advisory