
The Abyss Locker ransomware’s wallpaper
The Abyss Locker ransomware is a sophisticated threat that targets both Linux and Windows operating systems. Based on the HelloKitty ransomware source code, its earliest samples were detected in July 2023, with subsequent variants specifically targeting Windows systems emerging in early January 2024, FortiGuard Labs reported.
For Windows systems, Abyss Locker version 1 executes a series of actions aimed at disabling a wide range of services and terminating numerous processes. The services targeted for stopping include various Microsoft SQL Server services, Exchange services, SharePoint services, QuickBooks services, and more. This list encompasses critical infrastructure components such as databases, email, and collaboration tools, which are essential for the day-to-day operations of many organizations. By stopping these services, the ransomware aims to cripple the victim’s IT environment, making it more difficult to recover from the attack without paying the ransom.
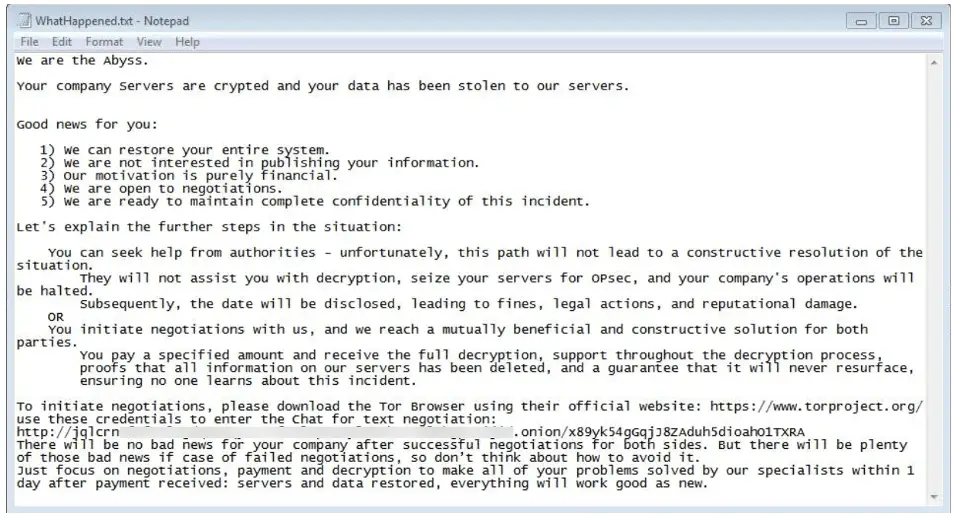
Additionally, Abyss Locker terminates a plethora of processes related to security, productivity, and system management software. This includes processes associated with antivirus programs, system monitoring tools, and applications such as Adobe products, Autodesk, Microsoft Office applications, and web browsers. The termination of these processes can help the ransomware evade detection and removal, ensuring that its encryption routines can proceed with minimal interference.

The ransomware’s capability to delete Volume Shadow Copies and system backups further complicates recovery efforts, as these are often relied upon for restoring encrypted or lost data. The comprehensive approach taken by Abyss Locker, from disabling essential services to terminating security and productivity-related processes, demonstrates the ransomware’s focus on maximizing impact and complicating recovery, thereby increasing the likelihood that victims will pay the ransom to regain access to their encrypted files.
This overview underscores the comprehensive strategy employed by Abyss Locker to maximize its impact on infected systems. By stopping services and terminating processes, it not only ensures the effectiveness of its encryption but also complicates any immediate response or recovery efforts, highlighting the importance of proactive security measures and timely detection to mitigate such threats.