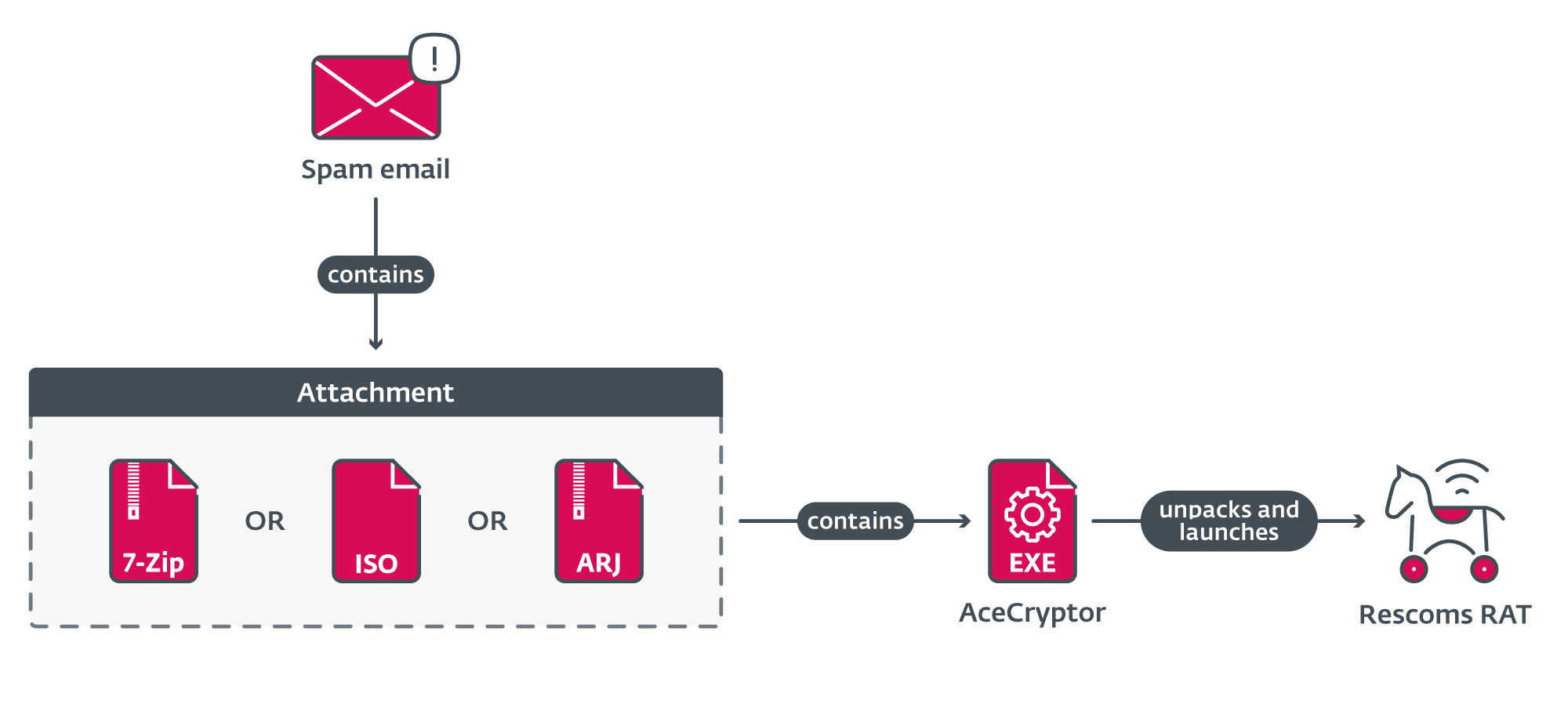
Compromise chain of Rescoms campaigns | Image: ESET
Cybersecurity experts at ESET have sounded the alarm on a significant increase in attacks powered by the AceCryptor platform. Long known as a cryptor-as-a-service (CaaS), enabling criminals to disguise their malware, AceCryptor has recently surged in popularity. This spike corresponds with the integration of the notorious Rescoms RAT (Remote Access Trojan) as the primary attack tool.
Initially identified for its role in encrypting malware to evade detection, AceCryptor’s utility for cybercriminals has been a topic of continuous observation by ESET. Throughout the first half of 2023, trends in its deployment remained stable. However, as the year progressed, ESET’s telemetry captured a twofold increase in attacks leveraging AceCryptor, marking a significant pivot in its usage dynamics. This escalation was predominantly attributed to its adoption by operators of Rescoms Remote Access Trojan (RAT), marking a novel chapter in its operational history.

A Coordinated Campaign
Predominantly targeting European nations such as Poland, Slovakia, Bulgaria, and Serbia, these AceCryptor-packed Rescoms RAT samples have served as the spearhead for numerous spam campaigns. These campaigns meticulously craft emails to imitate legitimate business communications, enticing recipients into downloading the malicious payload. The sophistication of these operations is highlighted by their ability to impersonate legitimate company domains through typosquatting, further underscoring the deceptive prowess of these threat actors.
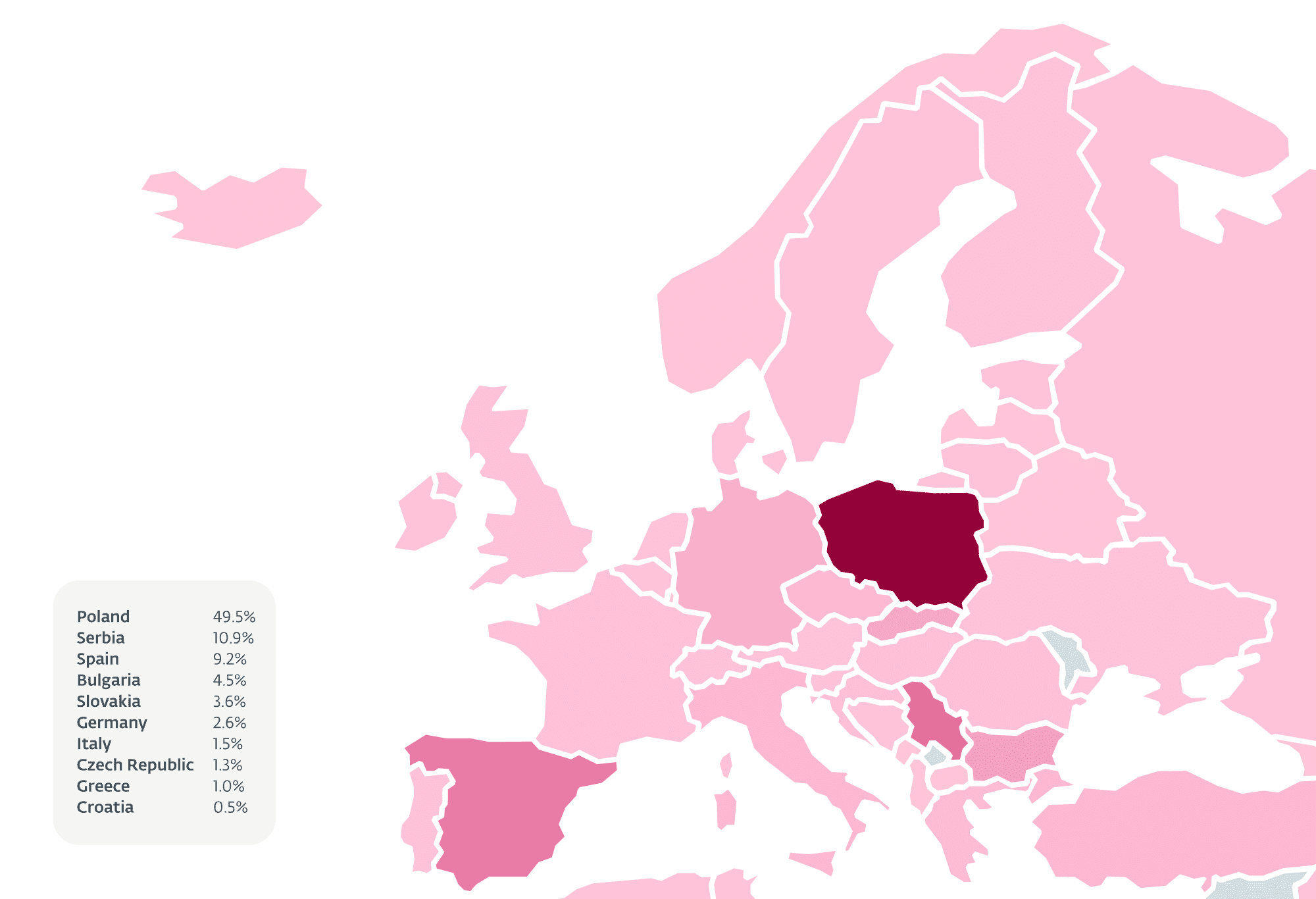
Despite a decrease in the variety of unique malicious samples detected, the consistent use of specific malware files across extensive email campaigns has amplified the reach of these threats. This strategy indicates a shift towards more concentrated and targeted attacks, maximizing the potential impact on selected victim pools.
How the Attacks Work
-
Spear-phishing Emails: Attackers craft highly targeted emails that mimic legitimate business correspondence or offers. These emails are cleverly designed to appear authentic, often including details specific to the target company. They may even originate from compromised business email accounts, further increasing their credibility.
-
Hidden Danger: The emails contain deceptive attachments in the form of archives or ISO files. Unsuspecting users who open these attachments unwittingly unleash the AceCryptor-packed Rescoms RAT onto their systems.
-
Network Invasion: Once executed, the Rescoms RAT gives attackers extensive control over the infected device. They can monitor activity, steal data, and deploy additional malware for further exploitation.
-
Primary Objective: The attackers’ main goal seems to be obtaining sensitive browser and email credentials. This stolen data offers a gateway into company systems, enabling them to launch more devastating attacks or sell the access to other cybercriminals
Why AceCryptor is a Formidable Tool
AceCryptor’s CaaS model provides criminals with a convenient and effective service. It disguises malware, hindering detection by security software. Its widespread use by different threat groups makes it even more dangerous, increasing the reach of potential attacks.
Protecting Your Business: Critical Actions
-
Awareness is Key: Educate employees about the latest phishing tactics. Stress the critical importance of scrutinizing emails, verifying sender identities, and exercising extreme caution with attachments, even seemingly familiar ones.
-
Advanced Security: Deploy endpoint security solutions that utilize multiple layers of detection, including behavioral analysis, to catch stealthy malware like Rescoms.
-
Defense-in-Depth: Go beyond software defenses. Implement network segmentation to limit the spread of an attack, enforce strict access controls, and maintain up-to-date backups for disaster recovery.
-
Stay Informed: Monitor cybersecurity news and vendor updates to stay ahead of evolving threats. Ensure your security software receives regular updates for the latest protection.
The Takeaway
The evolving AceCryptor and Rescoms partnership demonstrates the relentless nature of cyberattacks. Businesses must prioritize a proactive security posture that emphasizes employee training, multi-layered defenses, and constant vigilance. Failure to adapt could result in severe data breaches, financial losses, and reputational damage.