Hijacking the AC of an already running process
Kurosh Dabbagh Escalante, a Red Team Operator at BlackArrow, has introduced Eclipse, a proof-of-concept (PoC) tool designed to exploit Activation Context hijacking. By leveraging a technique known as Activation Context hijacking, Eclipse allows attackers to load and execute arbitrary DLLs within a target process. Escalante describes the tool as a “more flexible alternative to DLL Sideloading + DLL proxying,” with broad applications in injecting arbitrary code into trusted processes.
Activation contexts are data structures in memory that the system uses to manage the loading of DLLs, COM objects, and other system resources. They play a critical role in ensuring that applications load the correct version of a library or component. As Escalante explains in the PoC documentation, “Activation Contexts are ‘data structures in memory containing information that the system can use to redirect an application to load a particular DLL version.'”
Each process has a “main Activation Context,” which is initialized at process creation by parsing the binary’s manifest. The Operating System (OS) maps this context into memory and uses it to determine where DLLs are loaded from. Threads can also create and activate custom Activation Contexts (ACs) at runtime, which can override the main context temporarily.
This hierarchy, with main ACs stored in the Process Environment Block (PEB) and custom ACs managed in the Thread Environment Block (TEB), creates an opportunity for attackers to hijack these contexts. Eclipse capitalizes on this by manipulating these structures to redirect DLL loading paths.
The tool offers two primary modes of operation:
- Process Spawning with Hijacked AC: Eclipse spawns a new process in a suspended state, then hijacks its main Activation Context stored in the PEB. This allows the attacker to set a malicious AC that redirects the process to load their DLL instead of the legitimate one. As Escalante notes, “This will redirect the application to load your DLL instead of the legitimate DLL that would be loaded normally when the process execution is resumed.”
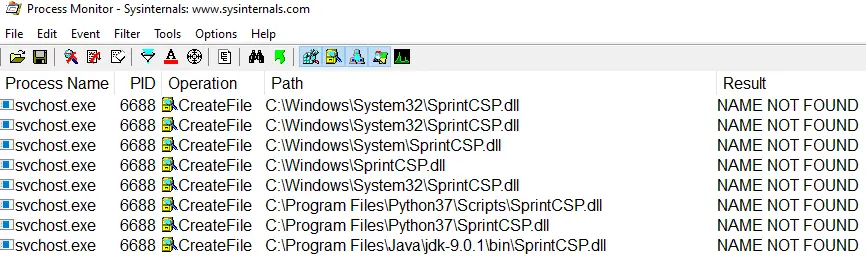
- Hijacking the Active AC of a Running Process: In this mode, Eclipse targets an already running process. If the main thread has an active custom AC, Eclipse hijacks the AC stack located in the TEB. If no custom AC is active, it defaults to hijacking the main AC from the PEB. Regardless of the scenario, the outcome is the same: the malicious DLL is loaded instead of the legitimate one when the hijacked AC is referenced.
Initially designed as an alternative to DLL Sideloading and proxying, Eclipse’s use cases extend beyond code injection into trusted processes. The ability to dynamically redirect DLL loading paths could enable:
- Evasion of Detection Mechanisms: By executing malicious code within trusted processes, attackers can bypass security tools that monitor untrusted binaries.
- Targeted Exploitation: Eclipse provides fine-grained control over the injection process, allowing attackers to tailor their approach for specific processes or scenarios.
- Red Team Training: For cybersecurity professionals, Eclipse serves as a powerful tool for understanding and defending against Activation Context-based attacks.
The PoC code and a detailed tutorial are available on Kurosh Dabbagh Escalante’s GitHub repository, making Eclipse accessible to both red teamers and defenders looking to study and mitigate such techniques. As Escalante remarks, “The memory address of the main AC of a process is obtained from the PEB, while custom ACs activated by a thread are obtained from an AC stack located in the TEB.”