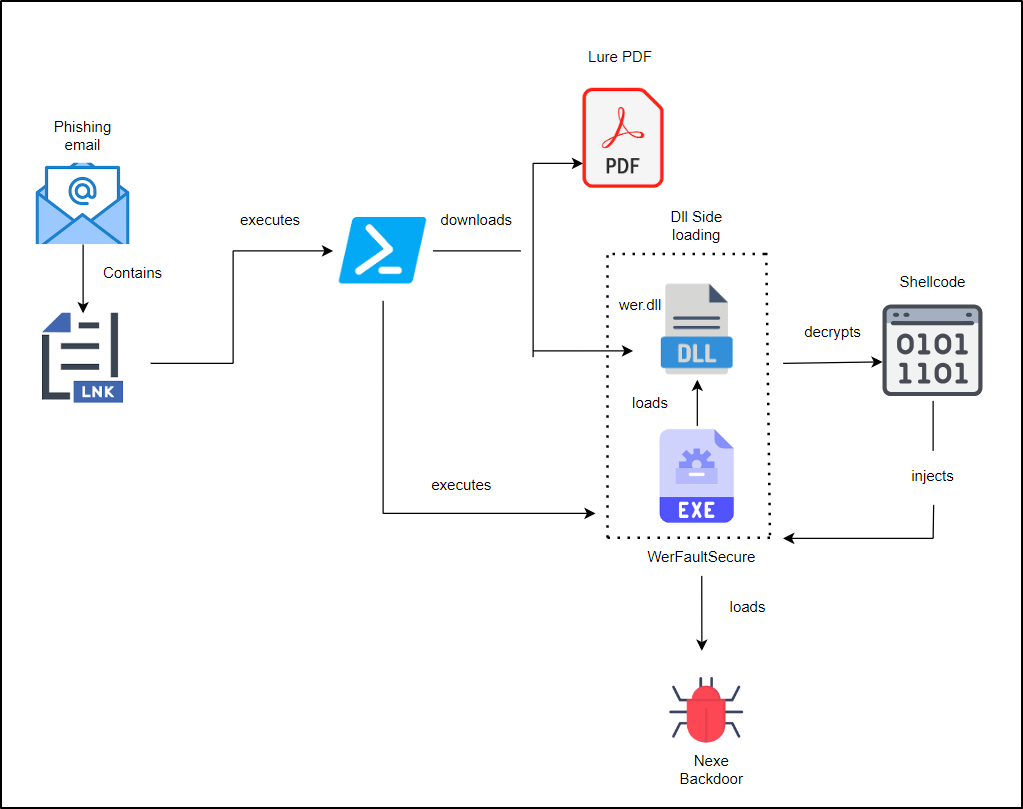
Infection chain | Image: CRIL
In a new report from Cyble Research and Intelligence Labs (CRIL), the notorious Patchwork APT group has once again demonstrated its cyber-espionage prowess with a sophisticated campaign deploying the “Nexe” backdoor. This group, also known as Dropping Elephant, has been active since 2009, focusing on high-profile organizations, including government, defense, and diplomatic entities, particularly in South and Southeast Asia.
The most recent campaign, identified by CRIL in July 2024, appears to target Chinese entities, focusing particularly on aerospace, technology research, and government sectors. This is no surprise, as Patchwork has long been linked to cyber-espionage operations aimed at geopolitical rivals. The campaign centers around the 7th COMAC International Science and Technology Innovation Week, using a malicious LNK file masquerading as a PDF document titled “COMAC_Technology_Innovation.pdf.lnk.” This decoy leverages a high-profile event to deceive victims into executing the malicious payload.
At the heart of the campaign is an LNK file that initiates the infection. Once opened, the file runs a PowerShell script, downloading two components: a legitimate-looking PDF to distract the user and a malicious Dynamic Link Library (DLL) used to carry out the attack. Patchwork employs DLL sideloading, a technique that takes advantage of a legitimate system file, in this case, “WerFaultSecure.exe,” to execute the malicious DLL without raising suspicion.
Once the malicious DLL is loaded, it decrypts and executes hidden shellcode, modifying key APIs such as AMSIscanBuffer and ETWEventWrite to bypass detection systems. This allows the malware to operate covertly within the compromised system, avoiding antivirus and security solutions that would normally flag such behavior.
The purpose of this campaign is the Nexe backdoor, a new variant that showcases the Patchwork group’s continuous evolution. This malware is designed to collect sensitive system information from the victim’s machine, including Process IDs, public and private IP addresses, usernames, and other crucial data. Once the data is harvested, it is encrypted using the Salsa20 algorithm, further obfuscated with Base64 encoding, and then transmitted to the group’s command-and-control (C2) server.
Nexe’s ability to blend into the victim’s system is one of its most dangerous features. By using legitimate system tools and DLL sideloading, the malware is able to operate in the background, stealing data while evading detection. The backdoor also leverages multiple layers of encryption and memory-resident payload execution to ensure persistence and stealth, allowing the attackers to maintain long-term access to the compromised systems.
The Patchwork APT group’s use of memory patching in this campaign is particularly noteworthy. By manipulating the AMSI and ETW APIs, the malware effectively disables Windows’ built-in security mechanisms designed to detect and block malicious scripts and processes. This method ensures that the malware can execute in-memory without being detected by common antivirus programs, allowing Patchwork to maintain its foothold on the victim’s machine for extended periods.
Related Posts:
- Volexity: Indian APT hacker organization Patchwork target US think tanks
- Patchwork Group Expands Cyber Espionage with Advanced Tools
- Palo Alto Networks: Patchwork hacker group is targeting the Indian Subcontinent
- The Hidden Threat: Android Apps with VajraSpy RAT Exposed