afl_ghidra_emu: fuzz exotic architecture using AFL++ and Ghidra emulation
afl_ghidra_emu
afl_ghidra_emu allows to fuzz exotic architecture using AFL++ and Ghidra emulation with code coverage functionality.
For more information, read this article.
How does it work?
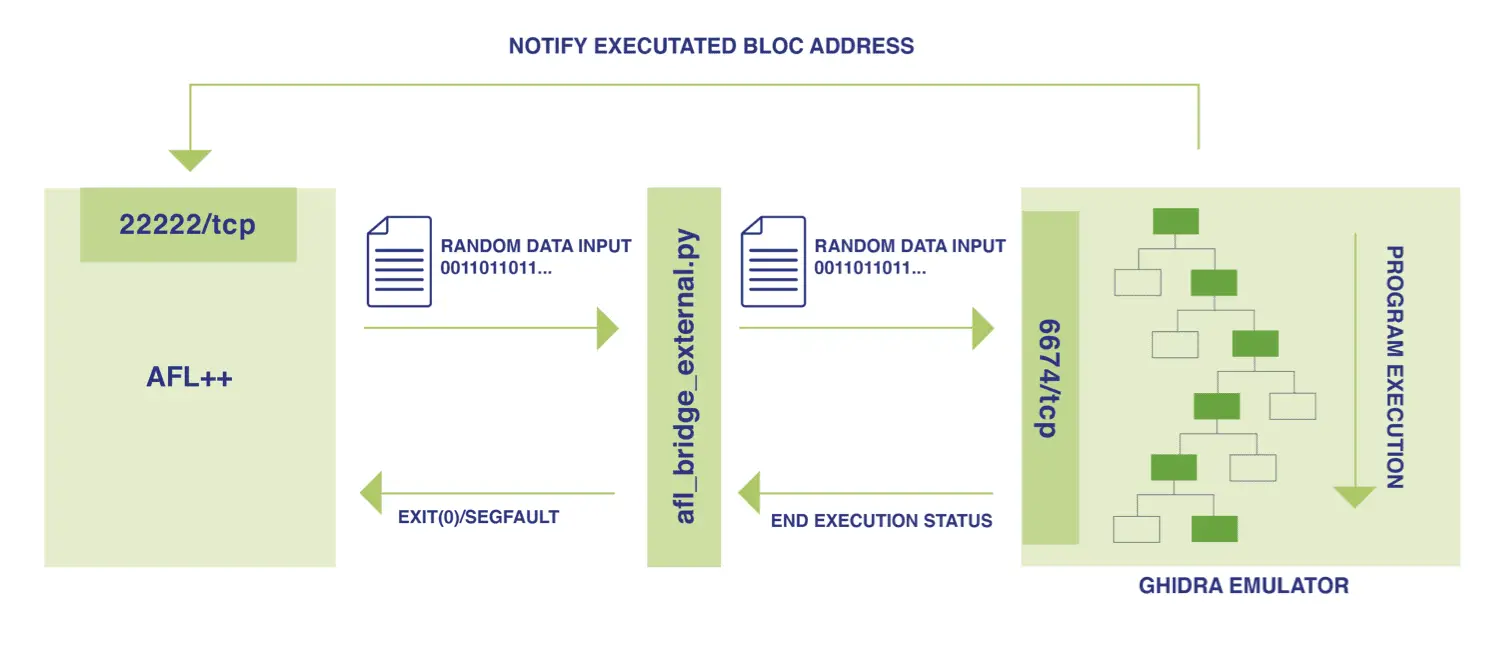
First, AFL++ listens on TCP socket (Ex: 22222/tcp) to get notified about the sample’s code execution path.
Then AFL++ runs a trampoline script (afl_bridge_external.py) which is in charge of forwarding samples and maintaining the AFL++ configuration to Ghidra emulation via a TCP socket (Ex: 127.0.0.1:6674/tcp)
Finally, a python script in Ghidra (fuzz_xtensa_check_serial.py) is responsible of emulating code execution. It listens on a TCP socket (127.0.0.1:6674/tcp) and waits for input data coming from the trampoline script. As soon as the script receives input data, the emulation will be started. During the execution, the executed path addresses are sent to AFL++ using its socket (127.0.0.1:22222).
The emulation engine reports the final execution status (Ex: got crash or not) to the trampoline script (afl_bridge_external.py). If a state crash is reported, the trampoline script exits with a segfault signal that AFL++ caches.
Install
Clone AFLplusplus-socket-mode directory.
git clone https://github.com/airbus-cyber/AFLplusplus-socket-mode
Compile AFLplusplus (read AFLplusplus-socket-mode/README.md for more options)
cd AFLplusplus-socket-mode
make
Get AFL Ghidra emulator scripts and library
cd AFLplusplus-socket-mode/utils/socket_mode
sh get_afl_ghidra_emulator.sh
Copy afl_ghidra_emu files to your ghidra script directory
cp –r afl_ghidra_emu/* $USER_HOME/ghidra_scripts/
Example: Fuzzing Xtensa binary code keygenme_xtensa.elf
./examples/xtensa/bin/keygenme_xtensa.elf is a keygenMe compiled for Xtensa (ex: esp32) architecture. Xtensa is not officially supported in Ghidra yet. So, you need first to install it by following this instruction
Load in Ghidra
- Create a new project in Ghidra;
- Import file ./bin/keygenme_xtensa.elf (arch: Xtensa:LE:32);
- Open it in CodeBrowser and execute auto-analyze;
- Open Script Manager in “Window” submenu;
- Run script fuzz_xtensa_check_serial.py;
Start Fuzz
Make AFL workspace directories
mkdir input output
Add the first sample
echo -n "BBBBBBBB" > input/sample1.bin
Start AFL++ with trampoline script.
afl-fuzz -p explore -D -Y 22222 -i input -o output -t 90000 /usr/bin/python2 afl_bridge_external.py -H 127.0.0.1 -P 6674 -a 127.0.0.1 -p 22222 -i @@
Stop Ghidra emulation
./afl_bridge_external.py -H 127.0.0.1 -P 6674 -s
Example: Fuzzing PPC binary code keygenme_ppc.elf
./examples/ppc/bin/keygenme_ppc.elf is also a keygenMe compiled for PowerPC architecture.
Follow the same steps above with PowerPC:BE:32:default architecture in Ghidra and run the script fuzz_ppc_check_serial.py.
Copyright (C) 2021





