Agent Tesla Loader Evolves: New Evasive Techniques Pose Rising Threat
A newly discovered malware loader is making waves in the cybercrime world, helping the notorious Agent Tesla infostealer expand its reach. This loader isn’t groundbreaking in its tactics, but its careful combination of techniques creates a potent recipe for increased infections and a serious headache for security teams. Detected by SpiderLabs on March 8, 2024, cybersecurity researchers have unveiled a sophisticated cyber-attack mechanism employing a novel loader designed to deploy the notorious Agent Tesla infostealer.
The Phishing Hook

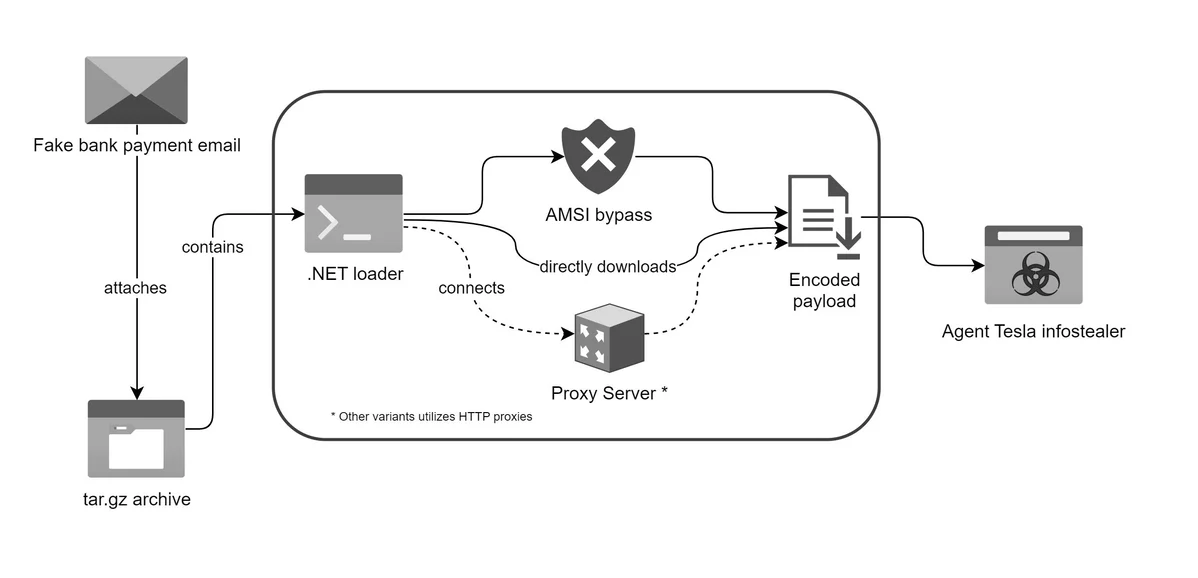
Infection chain: Email delivers loader, which then deploys Agent Tesla infostealer.
It starts with an email. Like many attacks, this one relies on impersonation, mimicking a “Bank Handlowy w Warszawie – dowód wpłaty_pdf.tar.gz” (bank payment receipt) to fool the recipient. Inside the phony receipt lurks not your expected financial details, but a cleverly disguised loader. The attachment, a .tar.gz archive, conceals a .NET compiled loader primed to unleash havoc.
Loader Unleashed: Evasion is Key
At the heart of this cyber onslaught lies the loader – a .NET executable that epitomizes obfuscation and evasion. The loader’s polymorphic nature, manifesting in two observed variants, showcases its capability to dynamically alter its decryption routines, complicating detection efforts. This level of sophistication not only evades antivirus defenses but also crafts a veil of invisibility around the loader’s true intentions.
Each variant of the loader employs a distinct approach to decrypt and activate its malicious payload. From converting hexadecimal keys into byte arrays and leveraging SHA-256 hashes to executing bitwise XOR operations, the loader’s decryption prowess is a testament to the attacker’s ingenuity. Beyond decryption, the loader employs stealth tactics to sidestep Microsoft’s Anti-Malware Scan Interface (AMSI), facilitating a seamless execution of the subsequent payload without raising alarms.
Agent Tesla Deploys: Theft in Memory
The loader’s arsenal includes mechanisms for retrieving the Agent Tesla payload from controlled domains, requiring specific user-agent strings to ensure successful payload delivery. Remarkably, one variant even utilizes an HTTP proxy server, sourced from an open-source list on GitHub, to mask its network footprint, further obfuscating its activities from prying eyes.
Upon successful retrieval, the loader meticulously extracts and decrypts the payload, utilizing XOR encryption – a classic yet effective technique. The execution of Agent Tesla directly in memory underscores the attackers’ preference for leaving no digital footprint, enhancing the malware’s stealth and reducing its detectability.
Once deployed, Agent Tesla embarks on its espionage mission, capturing keystrokes, stealing credentials, and siphoning off sensitive data. Its utilization of KoiVM protector complicates analysis efforts, rendering traditional investigative techniques less effective. This infostealer exfiltrates the harvested data using SMTP, employing compromised email accounts to mask its malicious communications amidst legitimate email traffic.
The Takeaway
This new loader is a reminder that the cyberthreat landscape is constantly shifting. Proactive vigilance, multilayered security measures, and ongoing user education are essential for staying protected.





