Inside a Python Infostealer: How Attackers Abuse Legitimate Platforms for Credential Theft
A Cybereason Security Services analysis uncovers a sophisticated infostealer campaign that leverages GitHub, GitLab, Telegram, and common social engineering tactics to compromise victims.
Attackers are becoming increasingly adept at weaponizing trusted resources and services, as seen in a recent Python-based infostealer campaign investigated by the Cybereason Security Services Team. These infostealers leverage legitimate code repositories (GitHub, GitLab) and popular messaging apps (Telegram, Discord) for stealthy credential harvesting and data exfiltration.
The Infection Process
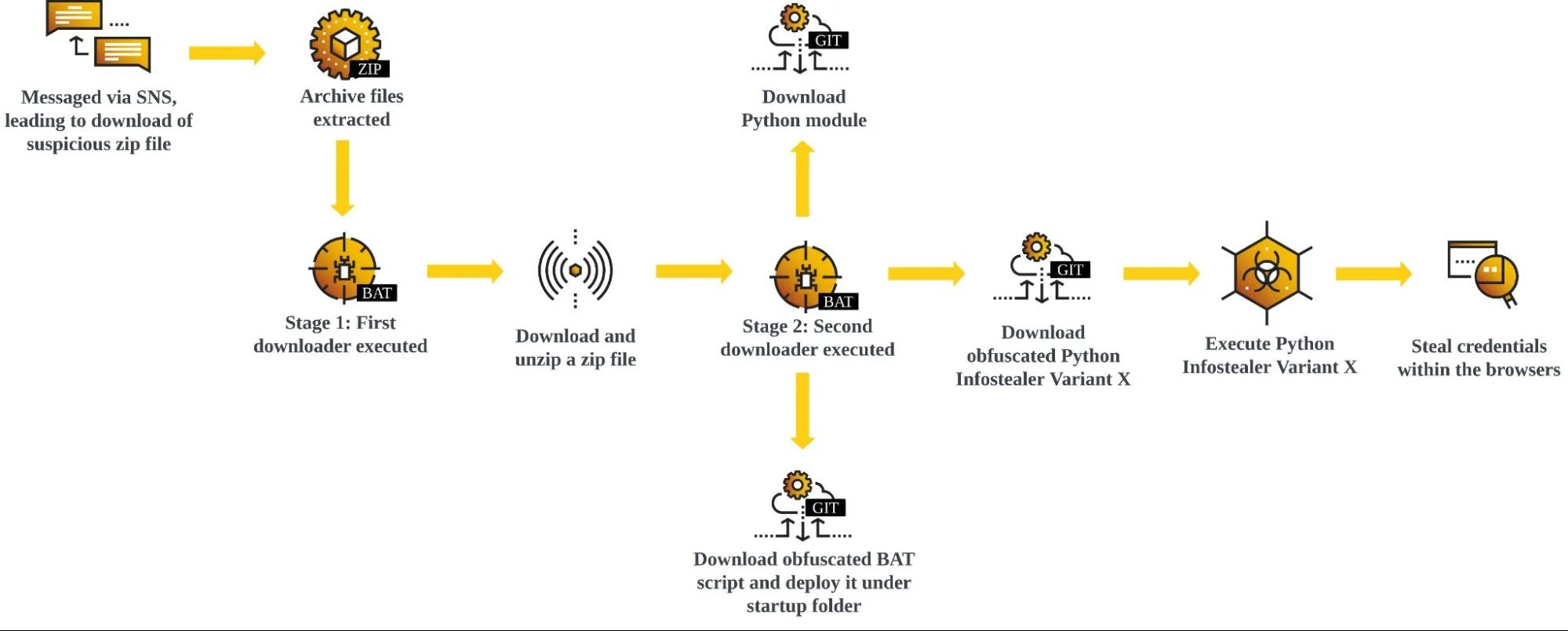
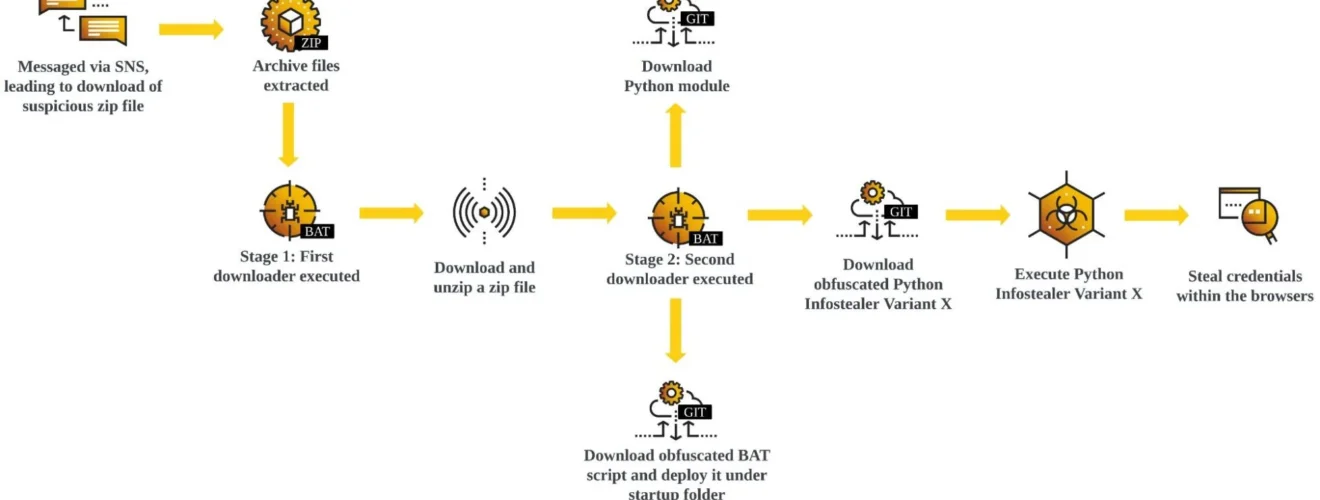
Python Credential Harvester’s Chain Of Infection | Image: Cybereason Security Services Team
- Social Engineering Lure: Victims are often targeted on Facebook Messenger with links to seemingly innocuous ZIP or RAR archives.
- Payload Delivery: The archive contains scripts (usually BAT or CMD) that initiate a multi-stage download process, frequently fetching files from GitLab or GitHub.
- Persistence Established: A BAT script is placed in the Startup folder to ensure the infostealer runs each time the victim logs in.
- Python Steals the Show: The final Python component targets browser data for theft. Credentials, cookies, and other sensitive information are the prime targets.
Campaign Evolution & Adaptability
- Shape-Shifting Malware: At least three primary infostealer variants exist – regular Python scripts, PyInstaller executables, and potentially others. This diversity reveals the attacker’s willingness to adapt and evade detection.
- A Growing Appetite: Later variants, like Variant One, show a marked increase in the number of targeted browsers, highlighting the attackers’ ambition to expand their data theft operations.
- Evading Defenses: Stolen data is often exfiltrated using mainstream messaging apps. This tactic helps the attack blend in with legitimate traffic, creating an additional hurdle for defenders.
Hiding in Plain Sight
- Abusing Trust: Hosting malicious code on trusted platforms like GitHub and GitLab aims to lower detection rates by blending in with legitimate activity.
- Evasive Exfiltration: Stolen data is often sent through mainstream messaging apps to disguise the data transfer and hinder network monitoring efforts.
Potential Attribution
While attribution is complex, analysis hints at potential links to Vietnamese-speaking individuals. Indicators include:
- Code comments in Vietnamese
- Naming conventions that align with common Vietnamese names
- Targeting of Coc Coc Browser, popular in Vietnam
Key Takeaways & Recommendations
- Think Before You Click: Remain cautious on social media, even with messages from seemingly known contacts. Verify the legitimacy of files before downloading.
- Zero-Trust Mindset: Don’t inherently trust code repositories, even reputable ones. Scrutinize the source and context of any downloaded code.
- Defense in Depth: Utilize robust security solutions that combine endpoint, network, and behavioral analysis to proactively detect suspicious activity.






