Jupyter Infostealer: Malware Masquerade Escalates in Recent Attacks
The VMware Carbon Black team has documented a new surge in attacks by the information-stealing Jupyter infostealer, which has been enhanced with updates that now incorporate PowerShell modifications. It also forges digital signatures to camouflage itself as legitimate files.
Jupyter, also known as Polazert, SolarMarker, or Yellow Cockatoo, was first chronicled in 2020 and is crafted in .NET. It is notorious for its deceptive search engine optimization maneuvers and the deployment of malicious advertisements to ensnare users. Individuals attempting to download mainstream applications are often diverted to counterfeit websites, initiating the infection process.
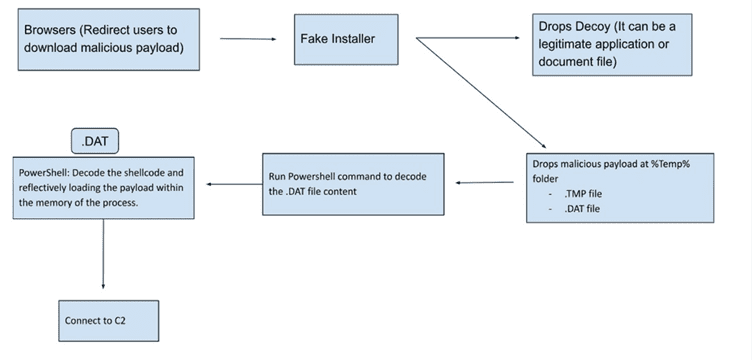
The sophisticated iteration of this software is not only capable of harvesting credentials but also establishes an encrypted connection with a Command and Control (C2) server to purloin data and carry out arbitrary commands. The recent modifications encompass the use of assorted certificates to sign the malicious software, lending it an ostensibly legitimate appearance, while the bogus installers trigger a chain of infection via PowerShell.
“Jupyter Infostealer exhibits a remarkable ability to evolve and adapt. These modifications seem to enhance its evasion capabilities, allowing it to remain inconspicuous. As cyber defenses strengthen, malicious software finds new avenues to breach and infect systems leaving us vulnerable to newer renditions of commonly seen older attacks,” the VMware Carbon Black team concluded.