Image Credit: Group-IB
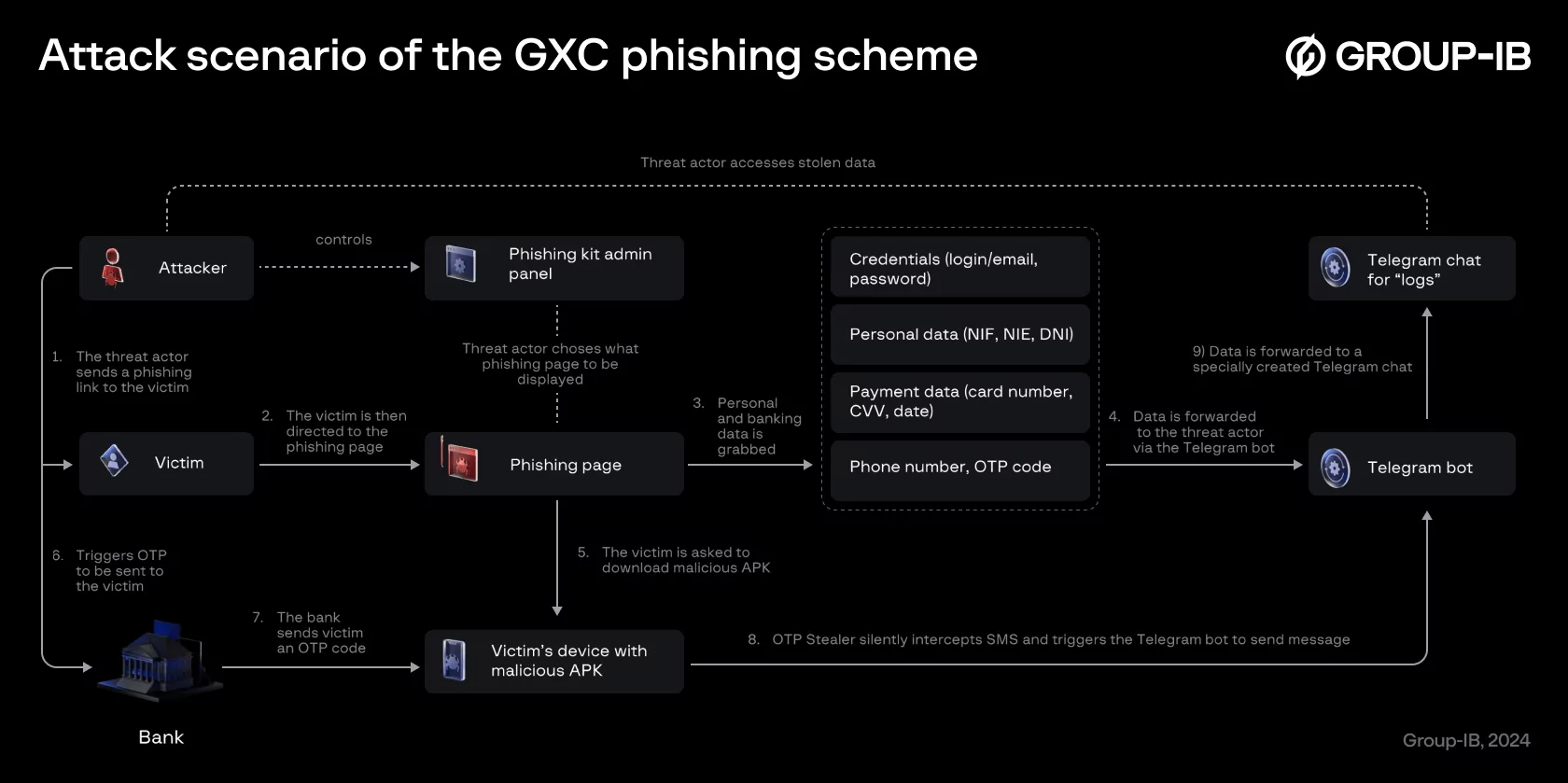
Group-IB reports on the activities of the Spanish-speaking cyber group GXC Team, which uses phishing kits with malicious Android applications. The cybercriminals offer comprehensive MaaS solutions, significantly enhancing the effectiveness of their attacks.
Group-IB has been monitoring the group’s activities since January 2023 and describes the hackers’ solution as a high-tech phishing-as-a-service platform, driven by artificial intelligence. The PhaaS platform targets users of over 36 Spanish banks, government institutions, and 30 organizations worldwide.
The phishing kit is sold for prices ranging from $150 to $900 per month, while the package including the phishing kit and Android malware is priced at $500 per month. Victims of the campaign include users of financial institutions in Spain, as well as tax and government services, e-commerce, banks, and cryptocurrency exchanges in the USA, UK, Slovakia, and Brazil. In total, 288 phishing domains have been identified.
The cyber group also sells stolen banking credentials and offers custom software development services to other cybercriminal groups targeting banking, financial, and cryptocurrency companies.
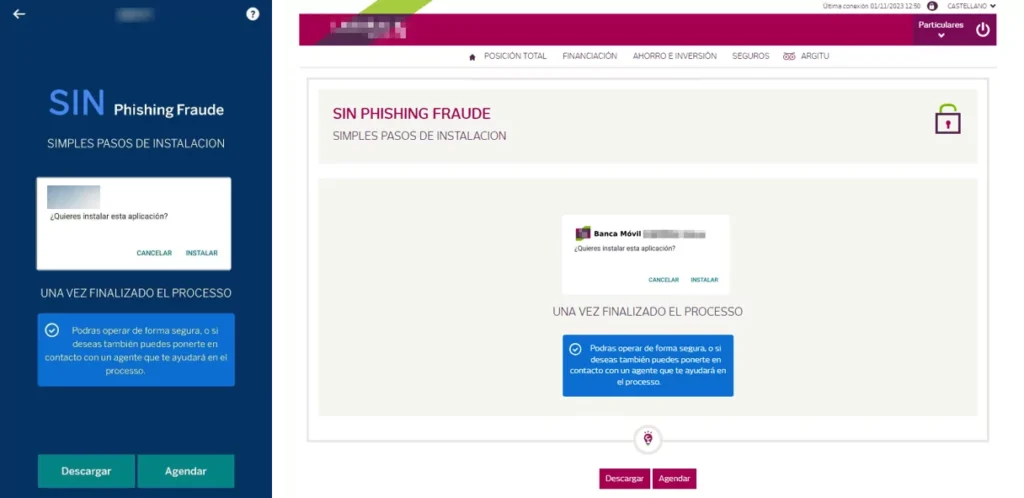
A distinctive feature of the GXC Team is their combination of phishing kits with malware designed to steal one-time passwords (OTPs) via SMS. Instead of using phishing pages to capture credentials, the attackers prompt victims to download a banking app for Android, ostensibly to prevent phishing attacks. Phishing pages are spread through various means, including smishing.
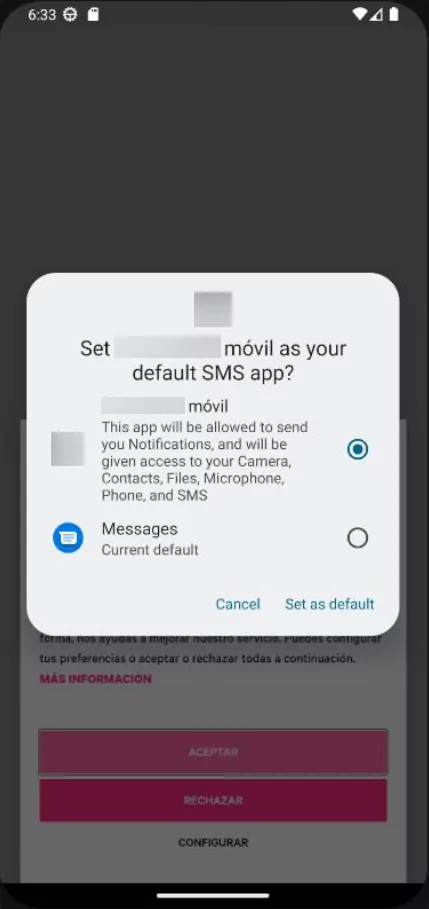
After installation, the app requests permission to set itself as the default SMS application, allowing it to intercept OTPs and other messages and send them to the operators’ Telegram bot. In the final stage, the app opens the legitimate bank website in WebView, enabling users to interact with the site as usual.
Along with the contents of SMS messages, additional information is sent to the attacker, including the device manufacturer and model, firmware version, current IP address, sender’s phone number, and SMS content.
Additionally, in a dedicated Telegram channel, the cybercriminals advertise tools for generating AI-powered voice calls, allowing clients to make voice calls to potential victims based on a series of prompts directly from the phishing kit. The calls are typically disguised as calls from a bank, urging victims to provide two-factor authentication (2FA) codes, install malicious applications, or perform other malicious actions.
The discovery of GXC Team reveals a new cyber threat specifically targeting clients of Spanish banks. The group has a well-established criminal enterprise and effective phishing tools, making GXC Team a significant threat to the region. Special attention is given to the unusual combination of the phishing kit and Android malware for stealing OTPs, making the tool much more versatile for criminals and far more dangerous for unsuspecting users.
Related Posts:
- The Rise of AI Scams: GXC Team’s New Tool for BEC and Wire Fraud
- Microsoft announces new AI-powered data types to Excel
- Facebook have been collecting call logs and SMS metadata for several years