
AiCEF
AiCEF is a tool implementing the accompanying framework [1] in order to harness the intelligence that is available from online resources, as well as threat groups’ activities, arsenal (eg. MITRE), to create relevant and timely cybersecurity exercise content. This way, we abstract the events from the reports in a machine-readable form. The produced graphs can be infused with additional intelligence, e.g. the threat actor profile from MITRE, also mapped in our ontology. While this may fill gaps that would be missing from a report, one can also manipulate the graph to create custom and unique models. Finally, we exploit transformer-based language models like GPT to convert the graph into text that can serve as the scenario of a cybersecurity exercise. We have tested and validated AiCEF with a group of experts in cybersecurity exercises, and the results clearly show that AiCEF significantly augments the capabilities in creating timely and relevant cybersecurity exercises in terms of both quality and time.
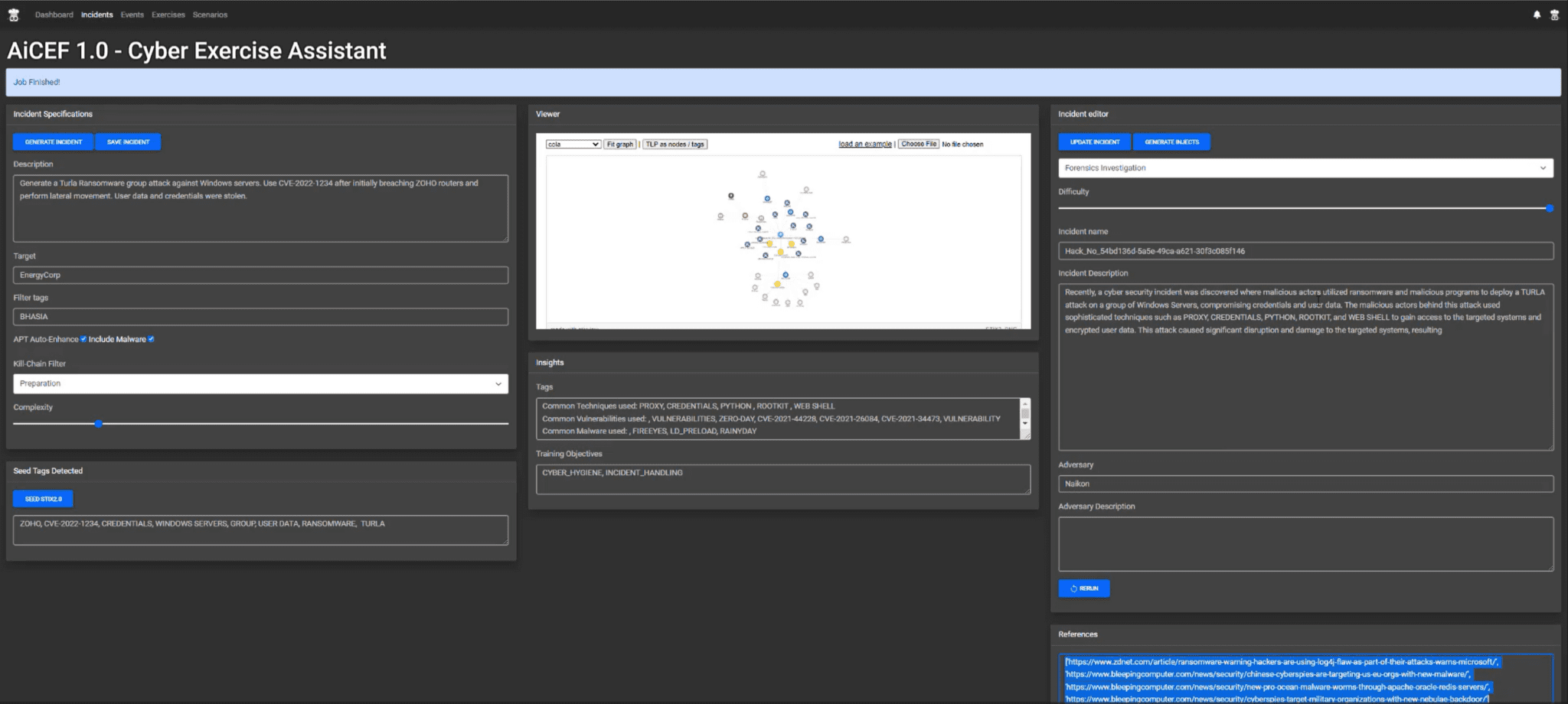
We used Python to create a machine-learning-powered Exercise Generation Framework and developed a set of tools to perform a set of individual tasks which would help an exercise planner (EP) to create a timely and targeted Cybersecurity Exercise Scenario, regardless of her experience.
Problems an Exercise Planner faces:
- Constant table-top research to have fresh content
- Realistic CSE scenario creation can be difficult and time-consuming
- Meeting objectives but also keeping it appealing for the target audience
- Is the relevance and timeliness aspects considered?
- Can all the above be automated?
Our Main Objective: Build an AI-powered tool that can generate relevant and up-to-date Cyber Exercise Content in a few steps with little technical expertise from the user.

Features
- An AI-powered Cyber Exercise Generation Framework
- Developed in Python & EEL (https://github.com/python-eel/Eel)
- Open source library Stixview (https://github.com/traut/stixview)
- Stores data in MYSQL
- API to Text Synthesis Models (ex. GPT-3.5)
- Can create incidents based on TTPs of 125 known APT actors
- Models Cyber Exercise Content in machine-readable STIX2.1 [2] (.json) and human-readable format (.pdf)