A massive, coordinated DDoS attack disrupted Steam services globally and the Perfect World Esports platform in China on the weekend of August 24-26, coinciding with the launch of the highly anticipated game Black Myth: Wukong. XLab’s Cyber Threat Insight Analysis (CTIA) system uncovered the extent of the attack, linking it to the AISURU botnet and suggesting a deliberate attempt to sabotage the game’s release.
Cybersecurity experts at XLab, utilizing their advanced Cyber Threat Insight Analysis (CTIA) system, quickly identified the scale and sophistication of the attack. Unlike typical DDoS incidents, this one involved nearly 60 botnet control nodes—an unprecedented number. These nodes orchestrated a series of assaults, mobilizing thousands of infected bots to target Steam servers across 13 regions worldwide, including major gaming hubs like China, the United States, and Japan.
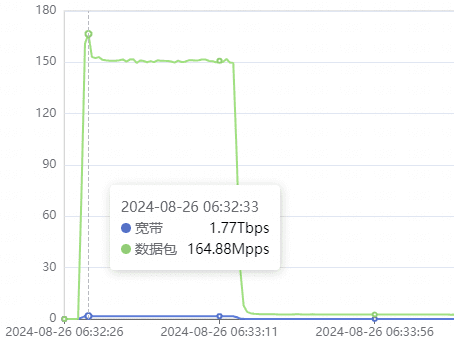
What stood out in this attack was its precision. The attackers launched four distinct waves, each timed to coincide with peak gaming hours in different time zones, thereby maximizing disruption. The targeted servers included those operated by Perfect World in China, suggesting a deliberate focus on undermining the Chinese gaming market while inflicting global chaos on Steam’s operations.
The timing of the attack, coming just after the launch of Black Myth: Wukong, raises questions about the motive behind this onslaught. Before this event, Perfect World’s Steam servers, primarily serving Chinese gamers, had seen few significant attacks. The sudden escalation in both the scale and intensity of this DDoS incident suggests a deliberate attempt to sabotage the release of this highly anticipated Chinese game. The sheer volume of attack instructions—peaking at 250,000—further underscores the attackers’ determination to disrupt this major gaming event.
Central to the attack was the AISURU botnet, a formidable entity boasting over 30,000 bots and an attack capacity of up to 2 terabits per second. AISURU’s tactics bear a striking resemblance to those of the notorious Fodcha botnet, known for its high-profile DDoS campaigns. However, AISURU has distinguished itself with unique innovations, particularly in encryption and network communication.
AISURU first surfaced under the name NAKOTNE, rapidly growing by exploiting over a dozen 0-day vulnerabilities. Its resurgence in May 2024 marked the beginning of its transformation into the formidable AISURU botnet we see today. The botnet’s code structure and infrastructure investments echo Fodcha’s methods, yet AISURU has made its mark with a distinctive style that poses an equally significant threat.
While the exact motives behind the attack remain unclear, the timing and targets suggest an intent to disrupt the launch of Black Myth: Wukong, a significant milestone for the Chinese gaming industry. This incident underscores the increasing sophistication and impact of DDoS attacks, particularly in the gaming industry. It highlights the need for proactive cybersecurity measures and robust defense mechanisms to mitigate the threat of large-scale, coordinated attacks.
Related Posts:
- CVE-2024-5274: Chrome Zero-Day Exploited by APT29, PoC Exploit Published
- PoC Exploit Releases for Unauthenticated XXE Flaw CVE-2024-38653 in Ivanti Avalanche
- Mirai Botnet Exploits Zero-Day Vulnerability CVE-2024-7029 in AVTECH IP Cameras