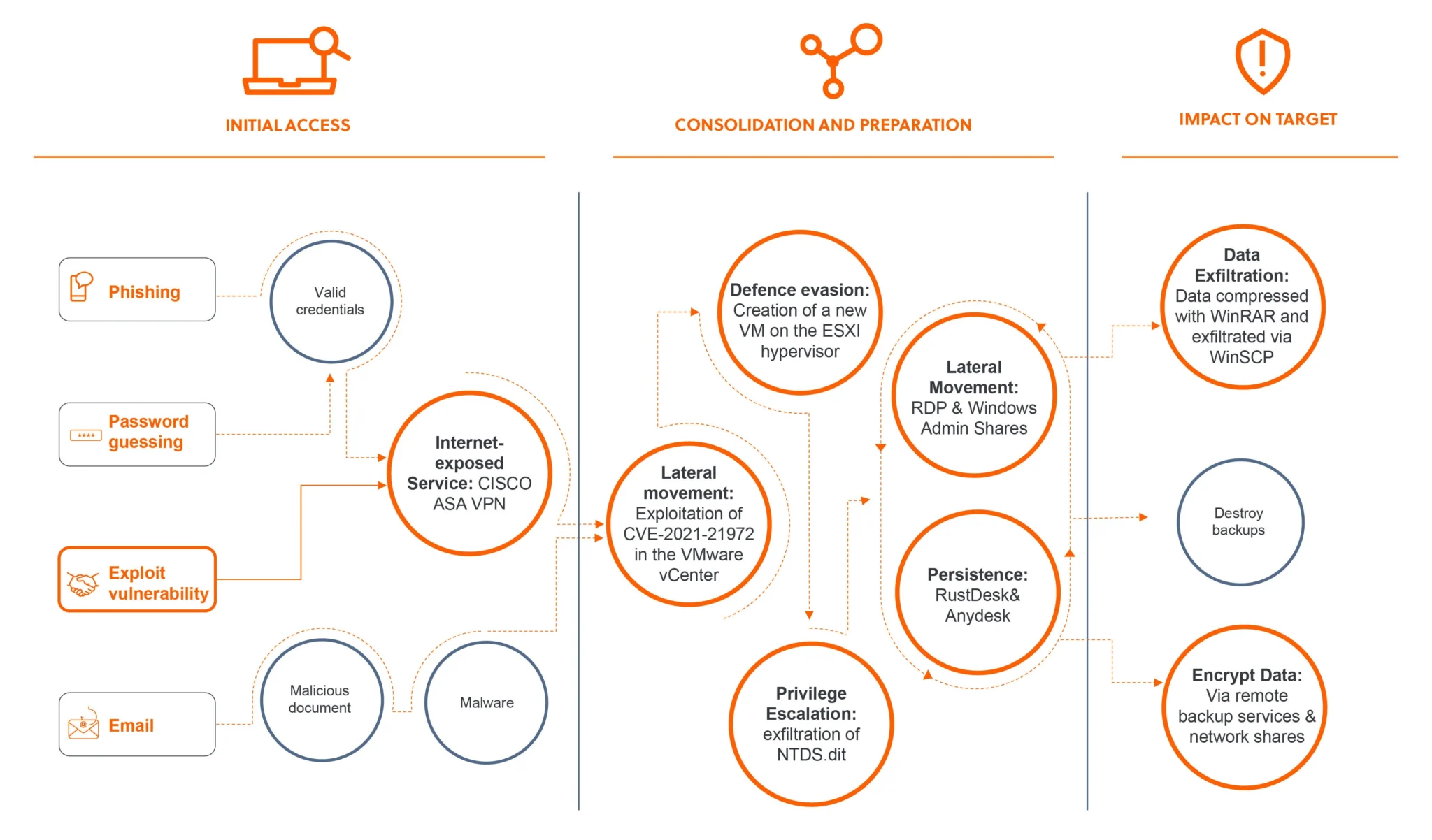
The attack chain
A recent analysis by S-RM, a global cybersecurity consultancy, has shed light on the escalating sophistication of the Akira ransomware group. The group, known for targeting small and medium-sized businesses, has adopted a novel privilege escalation technique commonly associated with Advanced Persistent Threat (APT) groups.
Since emerging in March 2023, the Akira ransomware group has targeted small to medium-sized organizations across North America, Europe, and Australia. Known for infiltrating networks via compromised VPN credentials or software vulnerabilities, Akira has refined its Tactics, Techniques, and Procedures (TTPs) to inflict maximum damage with minimal detection.

In early 2024, S-RM’s Incident Response team was called to investigate a breach at a multinational agriculture company. The breach was traced back to an unpatched, single-factor VPN appliance. This vulnerability served as the entry point for Akira, which then exploited a remote code execution (RCE) vulnerability (CVE-2021-21972) in VMware vCenter Server. This allowed the attackers to implant a reverse shell, granting remote access to the server.
Using a malicious file named ‘healthcheck_beat.jsp’, Akira established a reverse shell connection via the command-line tool NetCat. Once inside the vCenter, the attackers created a new virtual machine on a VMware ESXi hypervisor. This nearly invisible VM allowed them to operate undetected by conventional Endpoint Detection and Response (EDR) tools.
Although Akira initially gained local administrator privileges on the new VM, they sought elevated access for broader control. Their method involved extracting the NTDS.dit file, the Active Directory database storing user account data and password hashes. By temporarily powering down the domain controller’s VM, they copied the associated VMDK files, affixing these to the new VM to access and compress the NTDS.dit file with 7-zip. Additionally, they exfiltrated the SYSTEM hive, which contains the decryption key for the password hashes.
Armed with these credentials, Akira swiftly navigated the network, compromising additional accounts, exfiltrating data, and deploying ransomware — all within six hours.
Akira used two primary methods for ransomware deployment: via network shares and remote backup services. They exploited the legitimate Veritas Backup Exec Client process ‘beremote.exe’ to deploy ransomware binaries, bypassing security defenses by leveraging a legacy backup solution still present in the organization’s ecosystem.
Akira’s evolving tactics underscore the need for organizations to stay ahead of the curve in the ongoing cybersecurity arms race. By adopting proactive security measures and staying informed about emerging threats, businesses can better protect themselves against the rising tide of ransomware attacks.