Image: Fortinet
In recent months, the cybersecurity landscape has seen the rise of a potent ransomware variant known as Akira. FortiGuard Labs has been meticulously documenting the developments of this and other ransomware threats, releasing insightful reports.
Akira emerged in April 2023 and has versions designed for both Windows and Linux platforms. Its modus operandi is standard yet sinister. After infiltrating a network and pilfering data, Akira then encrypts victims’ files. Adding salt to the wound, the culprits deploy a double-extortion strategy; they not only demand ransoms for decryption but also threaten to make stolen data public.
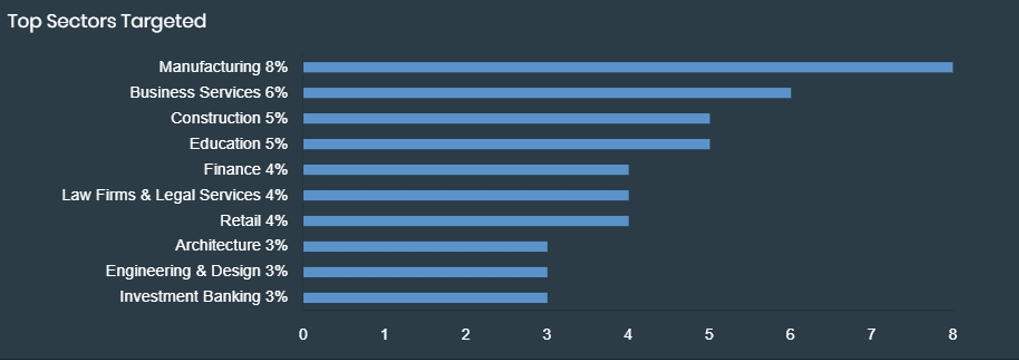
CERT India has pointed out that Akira predominantly targets entities utilizing VPN services without multi-factor authentication. There’s also the potential for attackers to buy network access from initial brokers. FortiRecon data paints a clear picture of Akira’s preferred targets. Manufacturing sectors bear the brunt of these attacks, closely followed by Business Services. Geographically, the United States tops the list of affected nations.
Windows version: Once Akira penetrates a Windows network and appropriates data, it seeks out and encrypts files. Notably, it steers clear of encrypting certain file extensions and directories, like “.exe,” “.dll,” and “Windows.” Its operational toolkit offers command-line options for tailored attacks, like specifying paths or defining encryption percentages. Encrypted files receive an “.akira” extension, and a ransom note titled “akira_readme.txt” is left behind.
Linux version: For Linux targets, Akira zeros in on a multitude of file extensions, from “.4dd” to “.iso.” It harnesses various symmetric key algorithms, including AES and IDEA, for encryption. Much like its Windows counterpart, the Linux version dispenses an identical ransom note post-encryption.

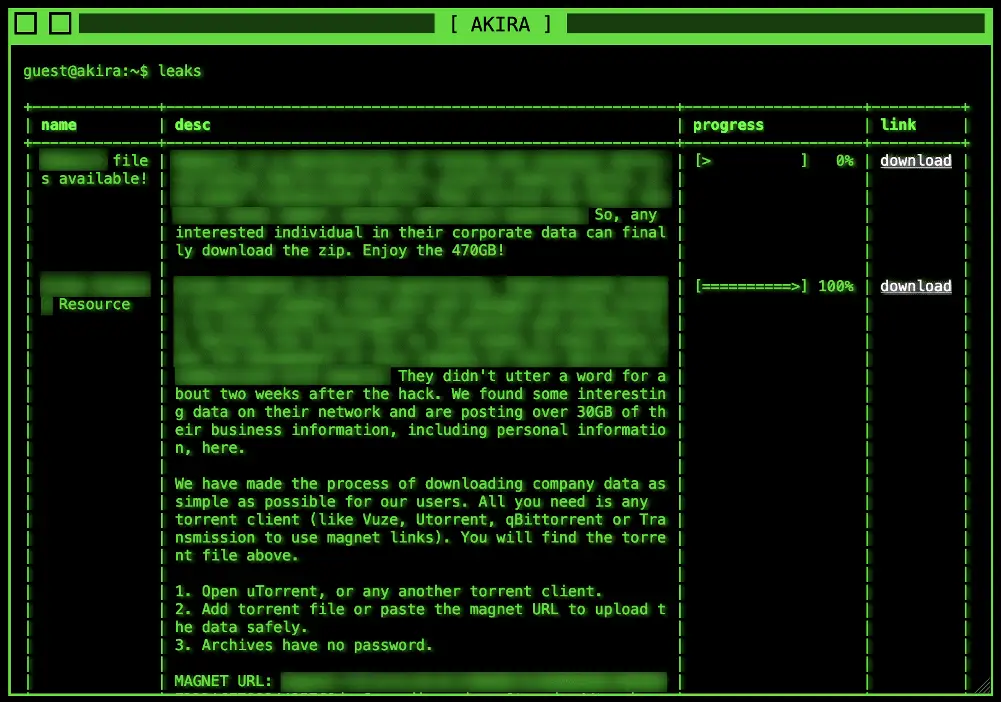
The Akira culprits operate a unique TOR site. Here, they display victim data, engage in communication, and even accept commands. For instance, the “leaks” command unveils links to pilfered data. As of September 2023, they’ve claimed at least six victims in that month alone, with over 20 organizations falling prey in August.
Megazord, a recent variant of Akira, surfaced in late August 2023. This iteration of the ransomware features a “powerranges.txt” ransom note, directing victims to Akira’s TOR site. Intriguingly, while standard Akira builds utilize C++, Megazord is written in Rust. This shift might herald future Akira iterations in Rust or even signal a complete rebranding. There have also been sightings of older Akira variants in May and June 2023.
The Akira ransomware underscores the evolving threat landscape, emphasizing the need for robust cybersecurity measures. As attackers diversify their tactics, businesses must bolster defenses, invest in state-of-the-art security solutions, and cultivate a culture of awareness.