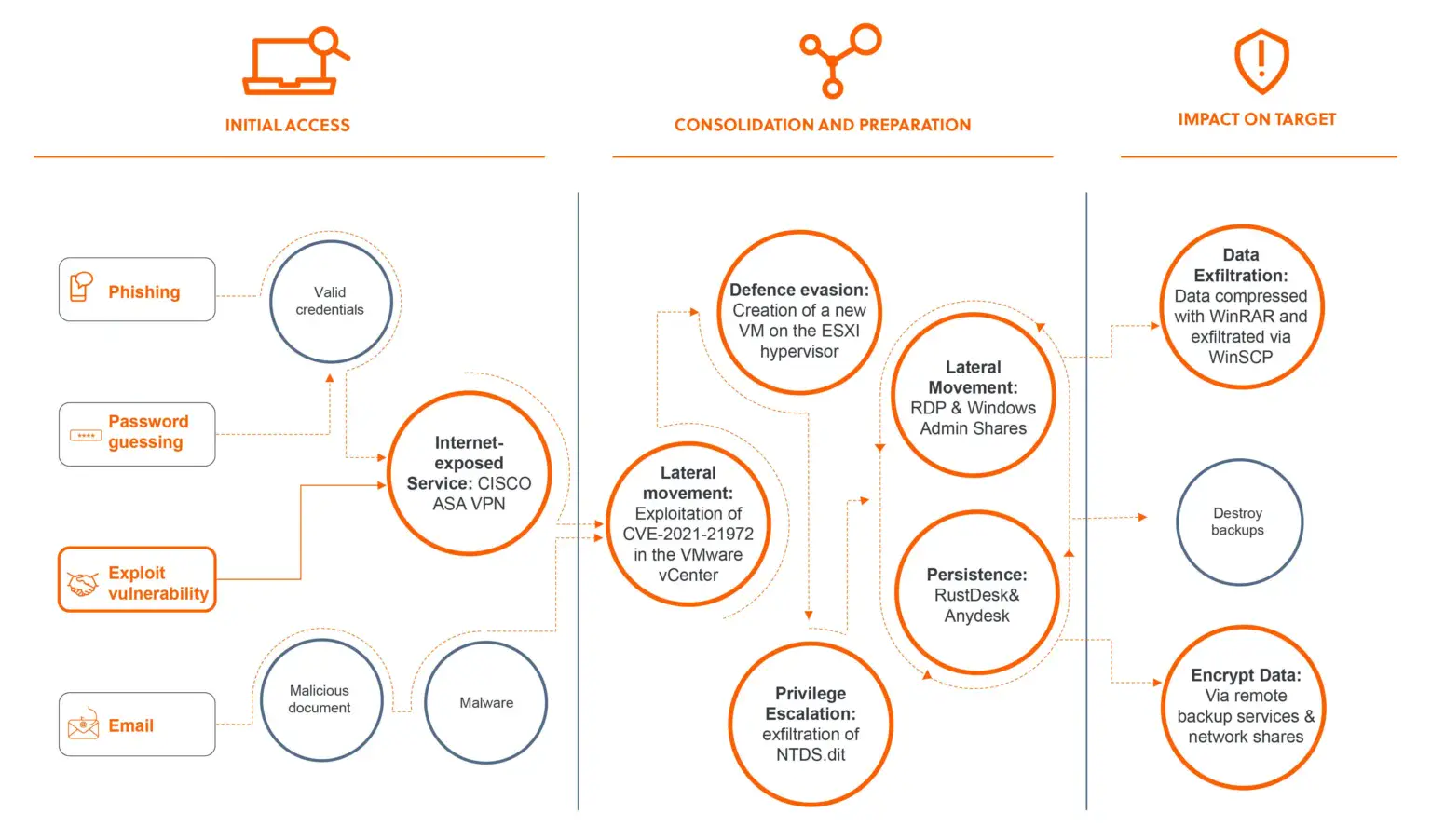
Akira Attack Chain | Image: S-RM
The Akira ransomware took a significant leap earlier this year with the introduction of a new Rust-based variant, according to a detailed analysis from Check Point Research (CPR). This version, known as “Akira v2,” demonstrates a strategic evolution in ransomware design, targeting ESXi bare-metal hypervisor servers and leveraging the unique properties of Rust to enhance its complexity and cross-platform capabilities.
Rust’s reputation for producing highly optimized, secure, and cross-platform binaries has made it a compelling choice for legitimate developers. Unfortunately, these same attributes are increasingly attracting cybercriminals. As CPR explains, “executables written in Rust have a reputation for being particularly challenging to reverse-engineer.” This makes them an ideal vehicle for sophisticated threats like Akira.
Rust’s aggressive inlining and monomorphization features contribute to assembly-level complexity, posing significant challenges for researchers. “The very nature of the language combined with the compiler’s drive to optimize its output can often result in forbidding disassembly,” CPR noted.
At its core, Akira v2 demonstrates a structured control flow optimized for multithreading, which boosts its performance. The ransomware’s main execution thread calls a series of functions—“Main -> default_action -> lock -> lock_closure”—that parse arguments, gather target files, and execute encryption in parallel threads.
A notable feature of this variant is its focus on ESXi servers. By default, it targets directories like /vmfs/volumes, commonly associated with VMware virtual machines, but retains the flexibility to encrypt other Linux systems. The ransomware’s operators can fine-tune its behavior via command-line flags such as –stopvm to shut down VMs or –exclude to skip specific files.
Akira employs a hybrid encryption approach, combining symmetric and asymmetric ciphers. Each targeted file receives a unique symmetric key, encrypted using a hardcoded Curve25519 public key. For symmetric encryption, Akira unusually uses SOSEMANUK, a stream cipher known for its complexity and previous use in ransomware like Pridelocker.
CPR’s analysis revealed that “the SOSEMANUK implementation is completely in-lined, and the cipher has to be identified using the traditional method of identifying incriminating constants.” This inlining, combined with Rust’s optimization strategies, makes deciphering the ransomware’s encryption process a Herculean task.
The malware is tailored for ease of use by its operators. Leveraging Rust libraries like indicatif, Akira provides a polished command-line interface (CLI) with progress bars, detailed status updates, and colorful output.
The adoption of Rust by ransomware developers marks a pivotal moment in cybersecurity. While Rust’s design principles offer undeniable benefits to legitimate developers, they also pose unique challenges to security professionals. CPR’s report highlights the need for new tools capable of “isolating and identifying spliced in-line code” to keep pace with Rust’s growing adoption in the malware ecosystem.
By embracing Rust, its developers have created a variant that is not only more potent but also harder to analyze. As CPR concluded, “Once upon a time, reverse-engineering C binaries were also primordial and scary; eventually, understanding improved, tooling caught up, and the task became much less formidable than it once was. We can only reason and hope that even the occasionally painful output of the Rust compiler will meet the same fate.”
Related Posts:
- Akira Ransomware Now Uses APT-Style Tactics to Breach Corporate Networks
- Akira Ransomware: The New Threat Targeting Windows & Linux
- Akira Goes Stealthy: Ransomware Group Prioritizes Data Theft for Extortion
- Akira Ransomware Exploit CVE-2024-40766 in SonicWall SonicOS