ALBeast attack demonstration | Image: Miggo
A new configuration-based vulnerability, dubbed ALBeast, has been uncovered by Miggo Research, affecting a staggering number of applications relying on AWS Application Load Balancers (ALBs) for authentication. This critical flaw allows attackers to bypass authentication and authorization mechanisms, potentially leading to unauthorized access, data breaches, and data exfiltration.
ALBeast is a configuration-based vulnerability that targets applications using AWS ALB’s authentication features. By exploiting this flaw, threat actors can bypass authentication and authorization controls, gaining unauthorized access to sensitive resources. The vulnerability’s impact on the confidentiality, integrity, and availability of affected applications makes it a critical issue for organizations using AWS ALB.
Miggo Research first reported ALBeast to AWS on April 6th, 2024. Since then, both parties have collaborated closely to address the issue. AWS responded by updating its authentication feature documentation and implementing new code to validate the AWS ALB instance signing the token, ensuring that customers are protected against potential exploits. Despite these efforts, Miggo Research estimates that over 15,000 out of 371,000 potentially vulnerable ALBs and applications worldwide remain at risk.
The ALBeast vulnerability can be exploited through a relatively simple attack sequence:
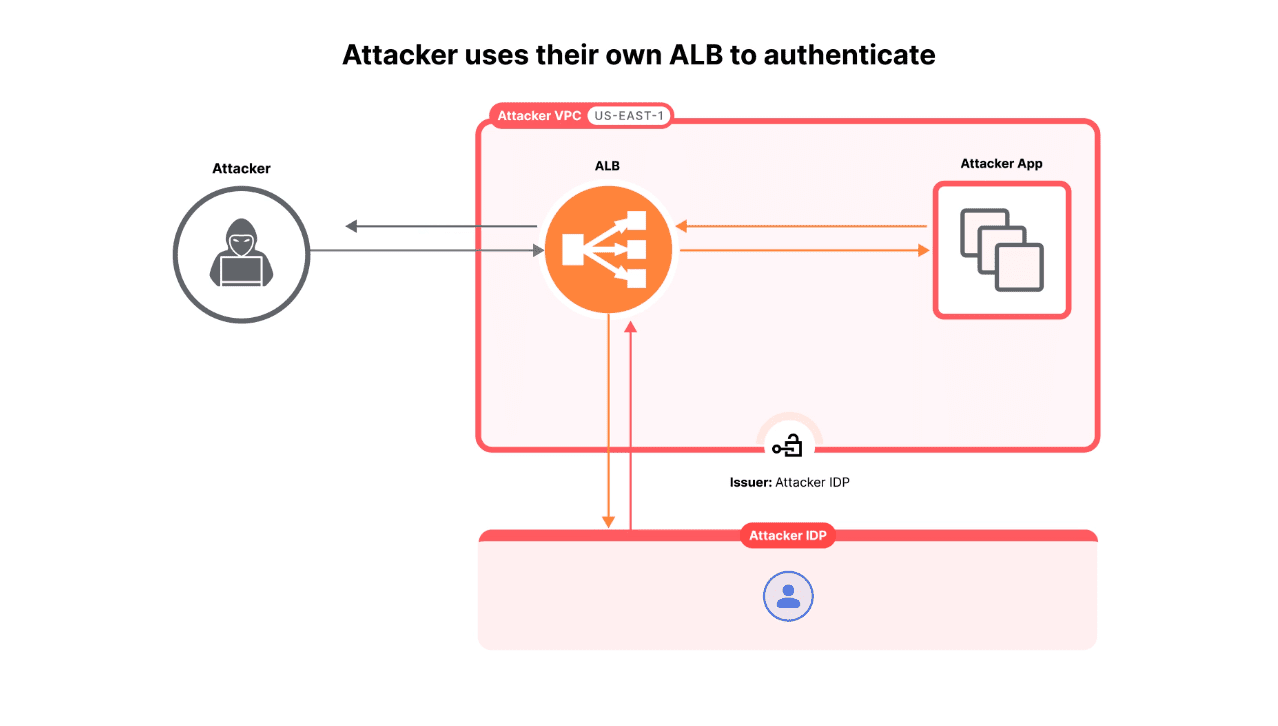
- Creating a Malicious ALB Instance: An attacker sets up their own ALB instance with authentication enabled in their AWS account.
- Forging the Token: The attacker then uses this ALB to sign a token they control, altering the ALB configuration to match the victim’s expected issuer.
- Bypassing Security: With the forged token, the attacker can bypass the authentication and authorization mechanisms of the victim’s application, gaining unauthorized access to protected resources.
This attack demonstrates how easily a misconfiguration can be exploited, turning a trusted authentication mechanism into a vulnerability.
AWS has stated that ALBeast is not a vulnerability in the ALB service itself but rather an issue stemming from misconfigurations within the shared responsibility model. Under this model, AWS is responsible for the security of the cloud infrastructure, while customers are responsible for securing their applications and configurations.
As a result, AWS users must ensure their applications comply with the updated documentation and best practices provided by AWS. This includes verifying the token signer in every application using ALB authentication and restricting target systems to only accept traffic from their Application Load Balancer.
To protect against ALBeast, Miggo Research recommends taking the following actions:
- Token Signer Verification: Ensure that every application using AWS ALB for authentication checks the token signer, as specified in the updated AWS documentation.
- Traffic Restriction: Configure security groups to restrict traffic to targets from only the Application Load Balancer, further reducing the risk of unauthorized access.
AWS has updated its documentation to reflect these security measures, urging customers to act promptly to safeguard their applications.
For a detailed technical analysis of the ALBeast vulnerability and how it was discovered, visit Miggo Research’s full report: The Hunt for ALBeast: A Technical Walkthrough.
Related Posts:
- PoC Exploit Available for CVE-2024-1212 (CVSS 10): Patch Kemp LoadMaster Now
- Hackers are selling legal Code Signing Certificates
- APT organization steals D-Link company digital certificate to sign its malware
- New Phishing Campaign Targets AWS Accounts: Security Experts Warn