Am I Exploitable?
‘Am I Exploitable?’ is a python open source project that comes to meet the need of validating if your system is exploitable to specific vulnerabilities. The project can help you understand whether you are exploitable to a specific vulnerability and explain to you what is the vulnerable component or invulnerable component in your system. The project can create a graph that presents the validation flow according to the vulnerability checks we perform. MI-X supports machine-readable output. The results can be exported to three different file formats: json, csv and text. After executing the tool, you will see the validation flow – it will print out which checks were performed on the host/container followed by remediation and mitigation recommendations. We want to create a community of researchers and programmers that can add vulnerability checks for new vulnerabilities or critical or famous vulnerabilities. Whenever a new vulnerability comes up, we can offer this service that helps people validate if they are exploitable or not. In addition, the vulnerabilities checks we wrote so far, can be expanded with some checks we might have missed.
Features and usage options:
- Validate if exploitable to provided cve
- Validate if exploitable to the category of cves
- Get the vulnerability description
- Validate the host containers
- Present the validation flow logic as a graph.
- Export the results to one of the three output formats: json, csv, and text.
- Get remediation and mitigation recommendations.
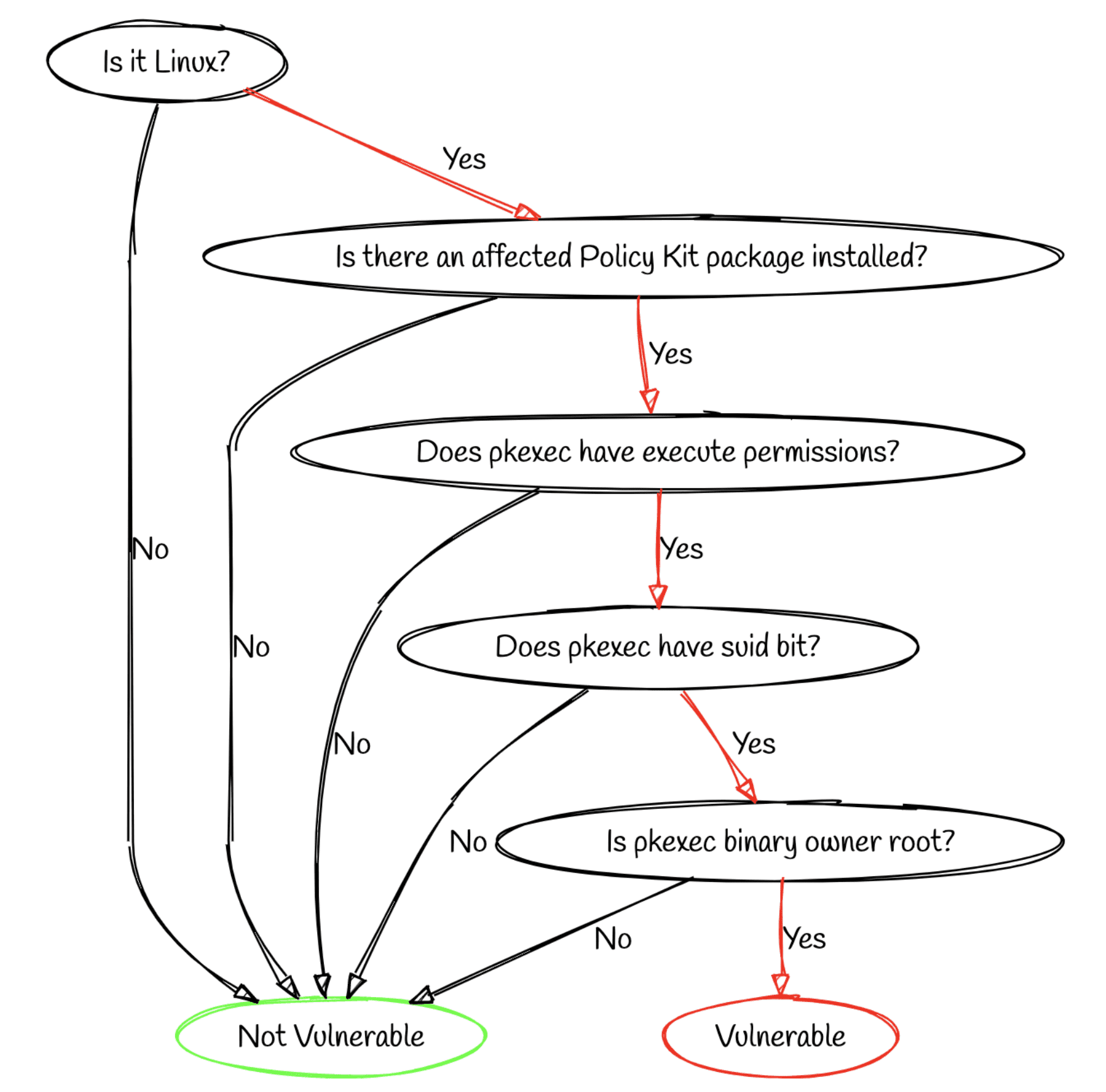
An example flow graph for CVE-2021-4034 (aka PwnKit):

Files
- am_i_exploitable.py – The main file which handles the user input and the CVEs calls.
- cves – Python package that contains a python file for each currently supported vulnerability.
- modules – Python package that contains modules. Modules are code implementations which are used in different CVE files.
Support Distributions
The tool supports the following Linux distributions:
Ubuntu, Debian, Red Hat, Centos, Fedora, SUSE, SLES, Amazon
Partial support for Alpine
Install & Use
Copyright (C) 2022 Rezilion