Image: techcrunch
At the beginning of this month, multiple Chinese security researchers published articles pointing to an e-commerce giant that had developed and exploited multiple vulnerabilities to escalate privileges and ultimately gain full control over users’ smartphones.
Upon successful privilege escalation, the malicious application could prevent users from uninstalling it, deceive and lure users, collect a wide range of users’ private information, and steal information from competing apps. Its ultimate goal is to significantly increase its installation and activity rates, prompting more conversions and boosting sales.
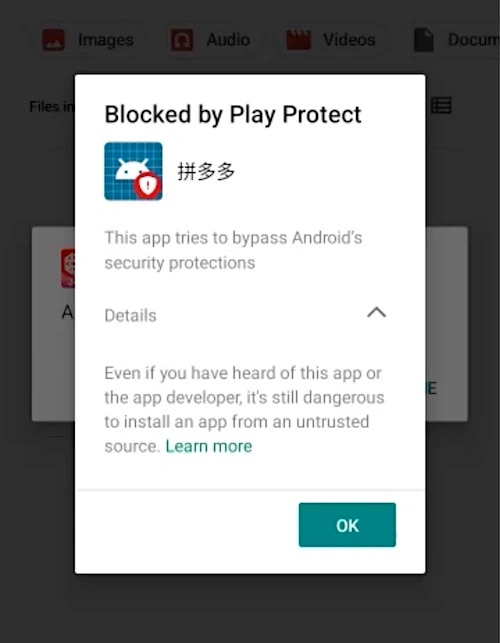
Following the report’s publication, speculation arose that the malicious app in question was Pinduoduo. This conjecture was proven accurate when Google announced last week that it had removed Pinduoduo from the Google Play Store and employed the Google Play Protect mechanism to automatically delete already-installed instances of Pinduoduo, citing the discovery of malicious behavior within the app.

Now, more evidence has surfaced to support these suspicions. Researchers from the security research firm Lookout spent two days conducting a detailed investigation of Pinduoduo, confirming the accuracy of the multiple Chinese security researchers’ reports.
Complex attacks:
Lookout’s analysis found that Pinduoduo exploited the Android Framework vulnerability (CVE-2023-20963) to attack the Android system, achieving privilege escalation without requiring any user interaction and operating undetected.
Limited by time and sample size, Lookout has yet to fully grasp Pinduoduo’s entire attack process, such as its prepared arsenal of over 30 DEX files tailored to target different brands and versions of Android smartphones, exploiting vulnerabilities for focused attacks.
In addition to exploiting zero-day vulnerabilities, Lookout also confirmed that Pinduoduo engaged in malicious activities, including adding widgets to infected devices, tracking the usage and data collection of installed applications, parsing notifications issued by other apps, and gathering Wi-Fi and location information.
Exploiting unpatched vulnerabilities:
Pinduoduo also leveraged some older vulnerabilities—ones for which Google had already released patches, but many Android devices were unable to receive the updates, leaving the vulnerabilities unaddressed. For example, Pinduoduo exploited EvilParcel, a privilege escalation vulnerability that has been actively used by hacker groups since 2012.
EvilParcel is a type of vulnerability that targets a set of related flaws, meaning multiple vulnerabilities are combined for exploitation. CVE-2023-20963 is one such vulnerability. Before the discovery of CVE-2023-20963, updated Android systems had resolved the issue. However, Pinduoduo used CVE-2023-20963 in conjunction with prior vulnerabilities to re-exploit the flaws.
Lookout confirmed these malicious exploitations in at least two Pinduoduo samples that contained the official Pinduoduo key signature, making Google’s removal and banishment of Pinduoduo justified.
It is worth noting that Lookout emphasized that the malicious versions of the Pinduoduo app were available in third-party markets, which users in China and elsewhere rely on because the official Google Play market is off-limits or not easy to access. No malicious versions were found in Play or Apple’s App Store. Previous reports claimed that the Google Play version of Pinduoduo could escalate privileges through cloud control modules, but Lookout’s findings appear to refute this assertion.
Via: arstechnica